Mamba ransomware / virus (Virus Removal Guide) - updated May 2019
Mamba virus Removal Guide
What is Mamba ransomware virus?
Mamba ransomware is a file locking virus that not only locks up files but also rewrites Master Boot Record, preventing victims from entering the computer

Mamba ransomware is a file locking virus that deviated from Phobos ransomware, which incorporates a lot of similarities with Dharma/CrySiS virus. The malware mostly uses weak RDP connections to propagate, although other methods, like spam emails, exploit kits, fake updates, etc., might be used as well.
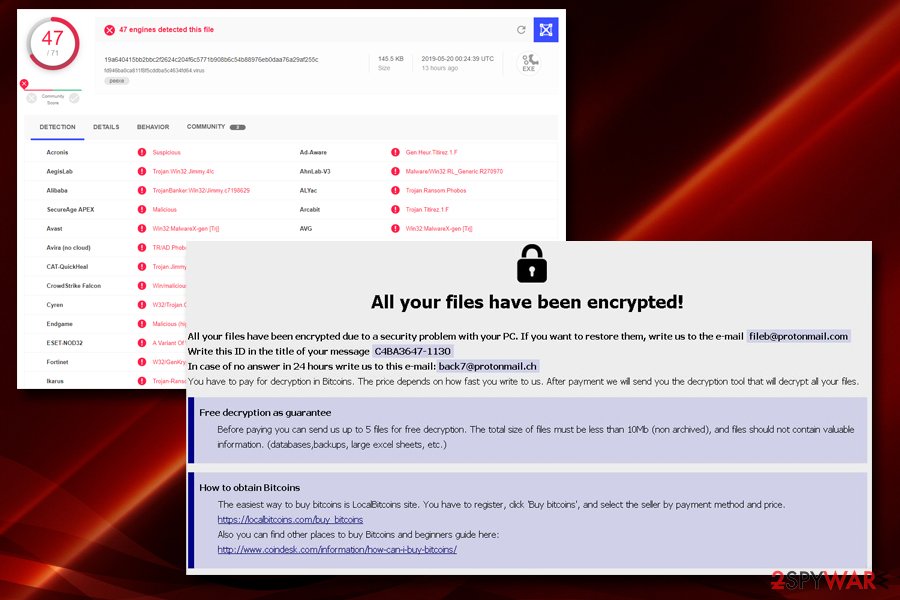
Once inside, Mamba ransomware encrypts files on the local as well networked drives with the help of AES-2048 cipher. Initial variant of the virus used .phobos appendix, although other extensions were used later – .fendi, .phoenix, and others. The latest version[1] incorporates .id[XXXXXX-1130].[fileb@protonmail.com].mamba file extension, and drops info.txt/info.hta ransom note. After encrypting data, Mamba virus reboots the machine and prevents users from accessing the machine, as Master Boot Record is rewritten.
To decrypt data or even be able to enter the device, hackers behind Mamba ransomware ask victims to contact them via a variety of different emails, depending on the virus variant – the latest one asks users to write to fileb@protonmail.com or back7@protonmail.ch. Unfortunately, there is currently no decryptor for this version available, but users can use alternative methods for data restore. Before that, however, the infected victims should remove Mamba ransomware from their device.
| Name | Mamba |
|---|---|
| Type of malware | Ransomware |
| Also known as | HDD Cryptor, HDDCrypt |
| Related | 152.exe, 141.exe, DefragmentService |
| File extensions | .phobos, .fendi, .phoenix, .mamba |
| Symptoms | Personal files inaccessible, lock screen displayed at boot |
| Danger | High. Can cause permanent data loss and system's crach |
| Attacks being held in | 2016 against San Francisco’s Municipal Transportation Agency 2017 attacked corporations in Brazil and Saudi Arabia New strains detected in 2018, though attacks haven't yet been executed |
| Mamba victims should use FortectIntego or another professional security tools to get rid of this malicious virus | |
Mamba virus attacked San Francisco’s Municipal Transportation Agency in November 2016 and asked to pay $73,000[2] ransom. In August 2017, ransomware came back and attacked several corporations in Brazil and Saudi Arabia.[3] Exhibiting modus operandi traits similar to Petya, Mamba ransomware targets data taking advantage of the DiskCryptor software. It is also known as HDD Cryptor, while the latest version known is dubbed as HDDCrypt. Detected at the end of March 2018, the virus does not deviate from its ancestors.
Reportedly, the virus drops 152.exe or 141.exe files on the computer, which are responsible for carrying out the encryption process. After encrypting victim’s files, the virus reboots the computer and displays the following message on the boot screen:
“You are Hacked ! H.D.D. Encrypted , Contact Us For Decryption Key (w889901665@yandex.com)
YOURID: [Victim’s ID]”
The victim can enter the decryption password on the boot screen; however, he or she needs to get one first. Victims have to get in touch with malware authors and get information on how to decrypt data and get access to the computer again. This virus asks to pay a ransom of 1BTC per 1 host. The money should be transferred to a provided Bitcoin wallet.
However, we always recommend users NOT to pay the ransom since it gives no guarantee that files will be decrypted[4]. Mamba removal is at utmost importance, and it should be completed using anti-malware tools, for example, FortectIntego or SpyHunter 5Combo Cleaner.
2019: latest Mamba ransomware variants exploit weak RDPs for propagation
Mamba ransomware is based on Dharma, so its primary distribution method remains manual – breaking into the computers via RDP[5] and installing the malware is something that hackers practice every time they detect a potential victim.
Once again, after several months of a break, Mamba ransomware returned at the end of 2018 and is being actively distributed since. Hackers use a variety of contact addresses and ask for a different amount of ransom inside ransom notes.
The latest variant of Mamba ransomware uses .id[XXXXXX-1130].[fileb@protonmail.com].mamba file extension and demands an unknown amount of payment in Bitcoin, which is declared once the victim contacts crooks via fileb@protonmail.com or back7@protonmail.ch email addresses. Additionally, hackers also offer a free decryption service for 5 files that cannot contain important information.
Nevertheless, the ransom should not be paid, as users should instead remove Mamba ransomware and use alternative file recovery methods.
Experts warn about expected Mamba ransomware comeback in 2018
Mamba is not typical ransomware. Its developers organize an outbreak against organizations and demand for huge ransom. Once collected, goes idle for a while. Silent since 2017 August, Mamba is expected to come back in the form of HDDCrypt ransomware.[6]
At the beginning of April 2018, ransomware researchers found out an unusual ransomware sample, which has been recognized as HDDCrypt by BitDefender, Emsisoft, Symantec, ESET-NOD32, and other reputable AV engines.[7] The current version rewrites PC's Master Boot Record sectors and locks the user out of his or her PC. As we have already mentioned, the modus operandi of Mamba ransomware reminds the infamous Petya, as well as Satana. It uses AES-256-06 cipher to lock victims PCs and activates a pirated copy of the open source software DiskCryptor.
Luckily, Mamba ransomware HDDCrypt variant did not go wild. Most probably the ransomware is currently in the development phase, though people should be cautious. Do not download standalone file installers from suspicious sources, as well as freeware without checking the installation setup carefully. Finally, don't forget to install the latest updates for your OS and update the anti-virus program regularly.
Mamba ransomware launched new attacks in August 2017
Mamba virus uses PSEXEC utility to install and run ransomware on the network. The same behavior we have seen in NotPetya operation. When it compromises the network, it creates a C: \xampp\http folder where it installs DiskCryptor components. This utility is used for executing ransomware on the local computer.
This tool also generates unique passwords for each computer that are connected to the same network by executing this command:
C: \TEMP\721.exe longPassword /accepteula
One of the sneakiest features of the malware is that it installs itself as a Windows Service and hides itself under the DefragmentationService name. It also gets LocalSystem privileges, so Mamba gets full control over the computer.
When preparatory work is over, and all malicious components are installed on the system, malware reboots the affected device. Then it configures bootloader to Master Boot Record (MBR) and starts data encryption with DiskCryptor.
Mamba encrypts disk partitions and shows an unusual ransom note. Cyber criminals demand to contact them by one of the provided emails in order to get decryption key:
- mcrytp2017@yandex.com
- citrix2234@protonmail.com
The ransom note also includes ransom unique victim’s ID number. However, we highly recommend not wasting your time with communicating with criminals and following their demands. You should remove Mamba automatically and restore your files from backups or use alternative recovery methods.
Mamba hit public transit system of San Francisco in November 2016

At the end of November of 2016, Mamba ransomware managed to find its way to San Fransisco Municipal railway system servers and corrupt essential records with unbreakable encryption. According to reports, the virus did hit 2,112 computers out of 8,656, blocking the email system, payment system and also railway scheduling system.
The virus displayed the same message on all railway system computers: You hacked, all data encrypted, contact for a key (cryptom27@yandex.ru)[8]. Ransomware managed to take down ticket dispensers, too.
What is more, the author of the Mamba malware has responded to some journalists from San Fransisco newspaper, saying that he didn't intend to infect the railway system, but since it has already happened, the organization has to pay 100 Bitcoin ($73,000) to get the decryption software.
The author calls himself Any Saolis, but obviously, that is not the real perpetrator's name. What is more, the attacker disclosed that he has gained access to private company's documents and that he is going to publish them online if the railway company refuses to pay the ransom[9].
However, the company has already restored the system and confirmed that attackers didn't manage to access any sensitive data at all[10]. The ransom wasn't paid.

Distribution methods of the ransomware virus
The virus spreads like a Trojan horse, so the user can install it while thinking that it is a harmless file. You might download it from email after opening an infectious email attachment or launching a malicious software update.
Consequently, it is highly recommended to stay away from sites that provide questionable downloads or show pop-up alerts stating that you need to update your software urgently. Such bogus updates typically contain malware.
Besides, ransomware threats frequently spread with the help of exploit kits. To prevent ransomware attacks, users should:
- protect their computers in advance by installing anti-malware programs,
- creating data backups,
- bypassing questionable sites on the Internet.
Elimination instructions for the Mamba ransomware
To remove Mamba virus, just as we have said, it is strongly advisable to use anti-malware utility, such as FortectIntego or SpyHunter 5Combo Cleaner. We recommend using it because it is programmed by IT experts who analyze each virus individually and create algorithms capable of detecting all files belonging to viruses and removing them.
Unless you are an advanced IT expert, you should not try to carry out Mamba removal manually, because you risk to delete wrong files, leave virus’ components and other unwanted components on the computer system.
Currently, the free Mamba decryption tool has not been found; therefore, the only way to restore files is to copy and paste them on the computer from a backup.
Getting rid of Mamba virus. Follow these steps
Manual removal using Safe Mode
If you cannot run automatic Mamba elimination, follow these steps:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Mamba using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Mamba. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Mamba from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Although there is no free decryption tool released, please, do not panic and do not rush to pay the ransom. Criminals might send you an infectious file together with the decryption software, or provide no decryption tool at all. You can wait, if you want – sometimes security experts manage to come up with free decryption tools in case they succeed to crack the ransomware code. Of course, you can recover files from backup disk or drive – just remove Mamba virus first.
If your files are encrypted by Mamba, you can use several methods to restore them:
Data Recovery Pro might help to recover your data
If your files have been encrypted by Mamba, you can try Data Recovery Pro service. Install this program using these instructions:
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Mamba ransomware;
- Restore them.
Mamba decryptor is not available yet
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Mamba and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ GrujaRS. #Phobos #Ransomware new extension. Twitter. Social network.
- ^ Julie Splinters. Free rides on Thanksgiving day? Ransomware hacks San Francisco’s transport system. 2-Spyware. Project dedicated to helping people know more about spyware, malware, adware and other dangerous programs that are spread on the Internet.
- ^ Anton Ivanov, Orkhan Mamedov. The return of Mamba ransomware. SecureList. Information about Viruses, Hackers and Spam.
- ^ Jeffrey Esposito. Hospital learns the hard way why you don’t pay ransomware crooks. Kaspersky Blog. Official Blog from Kaspersky Lab covers information to help protect you against viruses, spyware, hackers, spam .
- ^ Danny Palmer. New Phobos ransomware exploits weak security to hit targets around the world. ZDNet. Technology News, Analysis, Comments and Product Reviews.
- ^ HDDCrypt (or Mamba) ransomware. Twitter. MalwareHunterTeam.
- ^ File name bff29fd7fcc923087977aacec721e37e analysis. VirusTotal. Free service that analyzes suspicious files and URLs.
- ^ Joe Fitzgerald Rodriguez. ‘You Hacked’ appears at Muni stations as fare payment system crashes. The San Francisco Examiner. Monarch of the Dailies — Local, breaking news from San Francisco since 1865.
- ^ Bailey McCann. SF Muni Hacker threatens to release release stolen data. CivSource. News coverage of state and local government and technology issues.
- ^ Michael Heller. SF Municipal Railway restores systems after ransomware attack. SearchSecurity. The latest cybersecurity news, tips and features.





















