Phobos ransomware / virus (Virus Removal Instructions) - updated Oct 2020
Phobos virus Removal Guide
What is Phobos ransomware virus?
Phobos ransomware is a dangerous cyber infection that mimics the infamous Dharma
Later versions kept the extension .phobos, but used different contact addresses, along with the composite extension. The most recent contact emails changed to ofizducwell1988@aol.com and fobosAmerika@protonmail.ch. Currently, Phobos is actively attacking users all around the world, asking for as much as $5,000 ransom in return for the decryptor. It still remains active – the more recent and prominent versions throughout the last year are Actin ransomware and Mamba ransomware.
The year 2020 shows that Phobos ransomware is not dead. At the beginning of the year researchers warned about ISO variant, and the most recent version that resurfaced in May is dubbed as Eking ransomware. The latter is known for being spread via Adobe Acrobat cracks in particular and using decphob@tuta.io and decphob@protonmail.com emails for contacts. Unfortunately, the decryption software for this expanding virus hasn't yet been developed.
| Name | Phobos |
| Type | Ransomware |
| Known since | 2017 |
| Versions of extensions in the same family | .actin, .actor, .mamba, .phoenix, .acton, .frendi, .adage, .acute, .help, .com, .blend, .WALLET, .1500dollars, .adame, .banjo, .BORISHORSE, .Banta, .BANKS, .Adair, .zax, .HORSELIKER, .BANKS, .Barak, .Caley, .deal, .Cales, .calix, .Caleb, .elder, .octopus, .age, .deuce, .Angus, .Calum, .Dever, .Devon, .devil, .devos, .bablo, .dever, .dewar, .eight, .revon, .eject, .iso, .eight, .eking etc. Most of them are repeated many times throughout the years of the virus activity |
| File extensions | [ID].[OttoZimmerman@protonmail.ch].PHOBOS, [ID].[Job2019@tutanota.com].phobos, [ID].[Cadillac.407@aol.com].phobos, [ID][Raphaeldupon@aol.com].phobos, [ID].[Gomer_simpson2@aol.com].phobos, [ID].[ofizducwell1988@aol.com].phobos, .[ID].[Absonkaine@aol.com].phoenix, .[ID].[Returnmefiles@aol.com].actor, .[ID].[Fileb@protonmail.com].mamba, .[ID].[kew07@qq.com].actin, .[ID].[Randal_inman@aol.com].help, .[ID].[Upfileme@protonmail.com].actin, .[ID].[Returnmefiles@aol.com].actor, .[ID].[DonovanTudor@aol.com].com, .[ID].helpteam38@protonmail.com].adage, .[ID].[danger@countermail.com].blend, .[ID].[Walletdata@hotmail.com].WALLET, .[ID].[Lockhelp@qq.com].acute, .[ID].[Cleverhorse@protonmail.com].1500dollars, .[ID].[Hadleeshelton@aol.com].Acton, .[ID].[The777@tuta.io].Acuna, .[ID].[Crysall.g@aol.com].banjo, .[ID].[worldofdonkeys@protonmail.com].BORISHORSE, .[ID].[Larabita@cock.li].Banta, .[ID].[Decryptbox@airmail.cc].Adair, .[ID].[Zax444@qq.com].zax, .[ID].Decrypt@files.mn].BANKS, .[ID].[Captainpilot@cock.li].barak, .[ID].[Restorebackup@qq.com].Caley, .[ID].[Hanesworth.fabian@aol.com].deal, .[ID].Recoveryfast@airmail.cc].Cales, .[ID].[painplain98@protonmail.com].calix, .[ID].[debourbonvincenz@aol.com].banjo, .[ID].[Decryptfiles@qq.com].Devon, .[ID].[apoyo2019@protonmail.com].bablo, .[ID].[Mr.helper@qq.com].dewar, .[ID].[Backup.iso@aol.com].iso, .id[1E857D00-2776].[use_harrd@protonmail.com].eight, [ID].[decphob@tuta.io].eking, [ID].[decphob@protonmail.com].eking, etc. |
| Encryption algorithm | AES |
| Executable | processhacker-2.39-setup.exe |
| Ransom demand | Varies, can reach up to $5,000 or even $70 000 when the target is large business or company. The amount increases after 6 hours |
| Main dangers | Data loss, money loss, system compromise, malware infiltration |
| Distribution | Infected files as attachments on legitimate-looking emails, malicious files from hacked or malware-related websites, software cracks |
| Elimination | Perform a scan with an anti-malware tool to remove Phobos ransomware |
| Repair | You need to double-check and scan the machine using something like FortectIntego or a system optimizer, so virus damage is deleted and alterations fixed or repaired automatically |
Phobos ransomware virus mostly spreads via malicious spam emails[1] or fake installers[2] (processhacker-2.39-setup.exe) for applications like Process Hacker 2. Once inside the computer, it starts scanning the system, targeting the predetermined file extensions.
The malware encrypts various pictures, multimedia, images, documents, and even databases or other data using AES cryptography.[3] Thus, files locked by Phobos ransomware cannot be opened without a specific decryption tool.
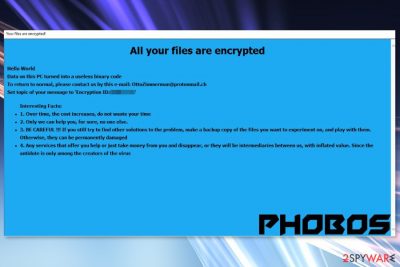
In the Phobos virus ransom note, criminals explain that the information stored on the affected computer was “turned into a useless binary code.” In order to make victims follow the ransom payment instructions, crooks tell that other third-party data recovery services will not help them.
However, they might take the money and disappear. Though, this situation is most likely to happen if you contact and transfer the money to authors of the Phobos ransomware virus. Cybercriminals are not eager to help you because the only focus is getting money from the victims.
Over the course of December 2018 and 2020, hackers released numerous new variants, which use different emails, including:
- Job2019@tutanota.com
- Bad_boy700@aol.com
- Cadillac.407@aol.com
- Everest_2010@aol.com
- Raphaeldupon@aol.com
- paper_plane1@aol.com
- barcelona_100@aol.com
- elizabethz7cu1jones@aol.com
- beltoro905073@aol.com
- Raphaeldupon@aol.com
- Gomer_simpson2@aol.com
- ofizducwell1988@aol.com
- FobosAmerika@protonmail.ch
- decphob@tuta.io
- decphob@protonmail.com
2019 came with even more news about Phobos virus because the ransomware started exploiting weak security to attack users all over the world.[4] It also targets businesses and large companies since these attacks ensure bigger profit from a single victim.[5] Badly secured RDP and other flaws used to enter the network and execute the malicious processes like file-locking and system changes.
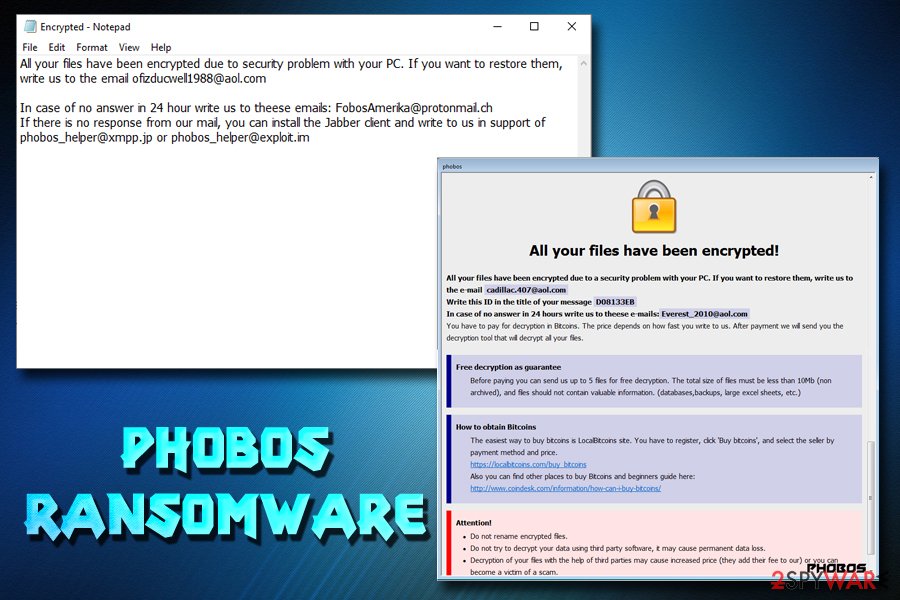
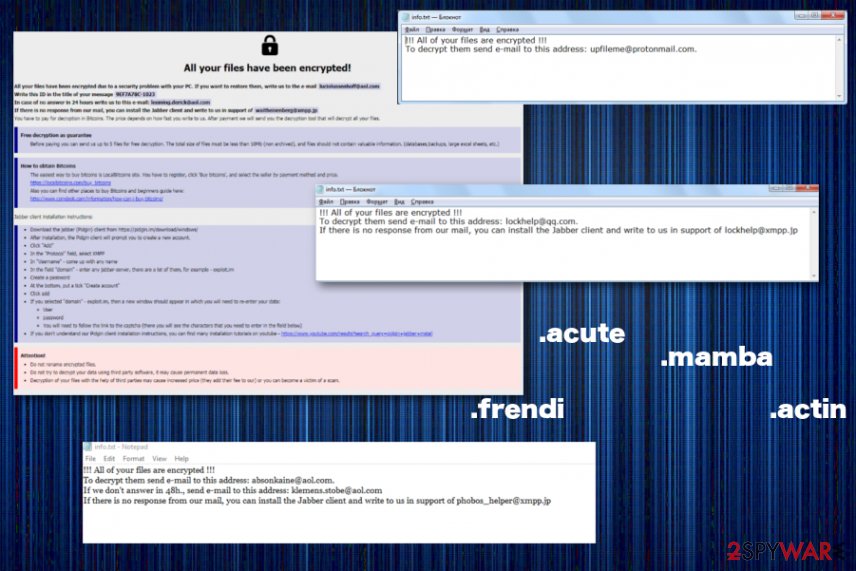
Phobos ransomware developers varied their ransom notes, naming them Encrypted.txt and Data.hta. One of the latest messages states the following:
All your files have been encrypted due to security problem with your PC. If you want to restore them, write us to the email ofizducwell1988@aol.com
In case of no answer in 24 hour write us to theese emails: FobosAmerika@protonmail.ch
If there is no response from our mail, you can install the Jabber client and write to us in support of phobos_helper@xmpp.jp or phobos_helper@exploit.im
It seems like the virus is gaining success in receiving payments, as Phobos ransomware developers already received 3.5 BTC ($13,257 at the time of the writing) into their Bitcoin wallet.[6] It once again proves that the ransomware business model is extremely successful, and these types of infections will not go away anywhere. For that reason, using comprehensive security measures is a necessity.
Hackers behind Phobos ransomware warn victims that, in case the ransom is not paid within a specific period, the size will increase significantly. However, cybersecurity specialists do not recommend contacting criminals and following their instructions because it might result in money loss.
If you got infected with the virus, do not panic, stay calm, and focus on Phobos ransomware removal. Trojans and ransomware often operate together to proliferate even more malware on the machine. Thus, ransomware infection might not only damage your files but corrupt the system as well. These threats often install programs, files or other malware to ensure persistence.
However, you should not try to eliminate malware-related files manually. To remove Phobos ransomware safely and successfully, you have to obtain a reputable software and terminate the virus within several minutes. As soon as malware is eliminated, we suggest you scan the machine with FortectIntego as it can fix all the damage done by the Phobos virus.
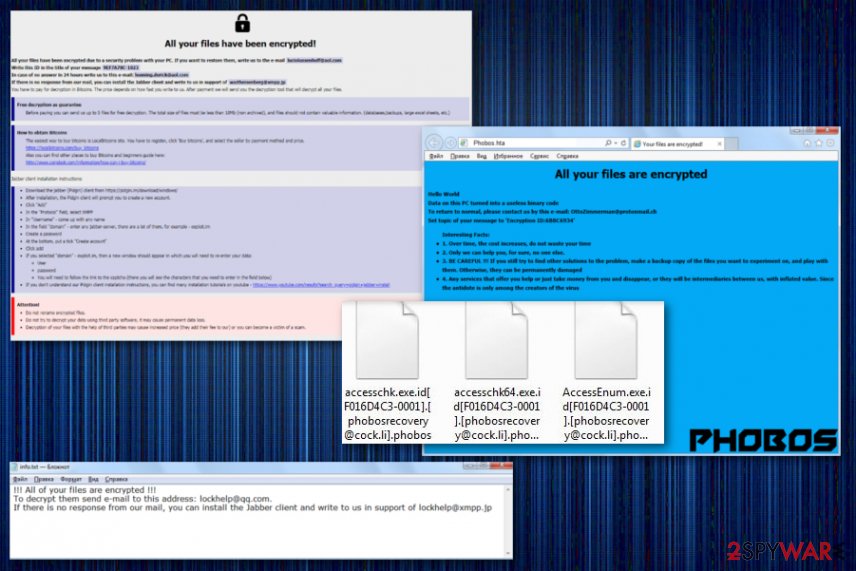
Phobos ransomware versions
The virus that came out first in 2017 is known for cybersecurity researchers for a while now, so data encryption and other extortion- based functionalities are analyzed. It is believed that the malware mainly is distributed from Ukraine and that the developers mimic dome features from other crypto-malware. Since October 2017, this family expanded, and even though the virus mainly uses .phobos extension to mark the files there are more versions that users tend to think.
Phobos ransomware
The first Phobos virus distribution month up until February 2019, delivered versions with the same .phobos file marker and only changed the contact information or names of the ransom notes. All the first variants looked similar to the Dharma ransomware because of the ransom message delivered as a hta program window and containing the thorough instructions about the payment. The full file marker added to encrypted files includes victims' ID and a full email address besides the .phobos at the end.
These first versions had extensions with contact emails:
- job2019@tutanota.com
- Bad_boy700@aol.com
- cadillac.407@aol.com
- Everest_2010@aol.com
- raphaeldupon@aol.com
- paper_plane1@aol.com
- barcelona_100@aol.com
- elizabethz7cu1jones@aol.com
- beltoro905073@aol.com
- gomer_simpson2@aol.com
- ofizducwell1988@aol.com
- FobosAmerika@protonmail.ch
- phobos.encrypt@qq.com
- pixell@tutanota.com
- elizabeth67bysthompson@aol.com
- pixell@cock.li
The ransom note for these particular versions differs from Encrypted.tx, Data.hta and contained pretty much the same message. The only few differences were particular countries where the versions got released. January 2019 found versions were more spread in Brazil than other countries.
The later ransomware variants throughout these activity years, including this .phobos marker, also mixed up the ransom note file names between Info.txt, info.hta, and encrypted.txt.
Frendi ransomware
Frendi ransomware was the version that came out at the end of February 2019. This is the first version known to researchers that haven't marked files with the initial .phobos appendix. The particular file extension that lands on encoded files include the .frendi appendix and tlalipidas1978@aol.com contact email. The same email address also included as the name of the main executable with ransomware payload.
Later on, a few more .phobos versions got delivered and after that at the start of April additional Frendi virus variants with withdirimugh1982@aol.com contact email emerged.
Phoenix ransomware
.phoenix is a file extension that also appeared in multiple versions of the virus throughout the years. Like other versions, not much changed from the initial cryptovirus, this threat included a few different contact emails in the ransom notes and file markers. autrey.b@aol.com and Costelloh@aol.com, hickeyblair@aol.com are one of those. Ransom notes resembling Dharma family and marked with PHOBOS at the corner remained the same for years, while developers only changed the contact information and IDs per victim.
Actor ransomware
This .actor file appendix appeared once or twice in these Phobos virus campaigns, which is not common for the developers. One of these variants found in 2019, at the start of May, contained returnmefiles@aol.com on the file extension and delivered a text file name Encrypted.txt with a few sentences, as per usual. Although, the common HTA window was not delivered, according to some victims, this version was spotted at different times the same year with the same contact information.
Mamba ransomware
Mamba ransomware came out with a few distinct features and an alternate name of HDD Cryptor. This virus was more dangerous because at first, it started targeting large businesses and attacking victims to gain large amounts via ransoms up to 70 000$. This was one of the versions that exploit unprotected RDP to infect the machines. Contact emails for this particular version are known to be fileb@protonmail.com, back7@protonmail.ch.
Actin ransomware
The version that again targets more PC users and individual victims – Actin ransomware. This is one of many versions in this family, but the only one with the particular .actin file appendix. This threat also uses AES algorithm for the encryption process and demands victims to contact developers via kew07@qq.com to get their files back allegedly. All those claims shouldn't be trusted because these cybercriminals know what they are doing and they have no goal to help people. Actin virus also came out more than a few times and had different emails for each campaign, including upfileme@protonmail.com, thedecrypt111@qq.com.
Acton ransomware
The slightly changed version from the previously described one, Acton ransomware was one of the less repeated variants int his Phobos ransomware family. Delivering the same info.hta program window with the payment instructions and contact information this time threat leaves out a ransom text file. Data encrypted by the virus get extensions including datadecryption@countermail.com.
Adage ransomware
The more recent versions in Phobos ransomware started to get more unique names and file extensions. Virus developers occasionally release variants with the original .phobos, but June 2019, in particular, was the month of new ransomware releases. .adage virus file marker comes in the traditional pattern .id[XXXXXXXX -1096].[lockhelp@qq.com].acute common for all the versions in Phobos family since 2017.
ISO ransomware
In the year 2020 Phobos creators delivered many versions reusing extensions like .jelp, .devos, and .dewarmany times. One of the more prominent and much more spreads around becomes this ISO ransomware version that carries a full pattern on extension .id[XXXXXXX-2589].[backup.iso@aol.com].iso. It remains to place the hat window and text file on the system with random demands and instructions. Ransom note file info.txt and info.hta get placed on the desktop and in other folders. In those messages email and Telegram messaging app contact information get listed: backup.iso@aol.com, @iso_recovery.
Eking ransomware
Despite numerous variants released in 2020, Eking ransomware stands out from the crowd to persistence and considerably high infections rate. The virus has been reported by users of third-party torrenting websites who assured that the payload of the ransomware has been downloaded along with Adobe Acrobat crack. Upon installation, the ransomware appends [id].[decphob@tuta.io].eking file extension and uses either info.hta pop-up or info.txt text file as a ransom note. Both information pages provide decphob@tuta.io and decphob@protonmail.com emails that should be messaged for further instructions.
Distribution methods of the file-encrypting virus
The crypto-malware can get inside the device when a user clicks on a malicious link, opens, or downloads an infected file. The malware executable can be included in the email or presented as a useful program in various torrents or download sites. Thus, users have to be careful and avoid questionable content online.
- Never open spam emails and stay away from the attachments included into an email that is sent from unknown senders.
- Do not download illegal content.
- Stay away from pop-ups informing about available updates.
- Do not download software from untrusted or unauthorized sources.
- Install a reputable antivirus program.
- Keep all your programs updated.
Security experts from Norway[7] suggest creating backups and updating them regularly. Unfortunately, sometimes it’s impossible to decrypt files with third-party software. Therefore, having backups prevents data loss.
Phobos virus elimination guide
Trying to locate and wipe out malware-related files manually might end up with serious damage to the system. Therefore, we do not recommend risking to delete the wrong files. It’s better to dedicate Phobos ransomware removal for the professionals. We mean, you should obtain a reputable malware removal software, such as SpyHunter 5Combo Cleaner, or Malwarebytes, and get rid of the cyber infection automatically.
However, ransomware might be resistant and block security programs. For this reason, you should reboot the computer to the Safe Mode with Networking first in order to remove Phobos ransomware virus entirely. You can find the instructions below for this method and other tips that may help termination malware fully.
Also, for files that Phobos ransomware virus may damage and corrupt, try FortectIntego or a PC repair tool, system optimization application. Such software can easily indicate affected or damaged files, programs, system functions, and even fox such damage automatically without triggering additional changes or alterations.
Getting rid of Phobos virus. Follow these steps
Manual removal using Safe Mode
In order to run automatic malware removal, follow these steps:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Phobos using System Restore
These instructions can help to get rid of the virus with the help of antivirus software too:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Phobos. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Phobos from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Only backups can help to restore all files encrypted by ransomware. However, we highly recommend trying alternative third-party tools that might help to recover at least some of the lost data.
If your files are encrypted by Phobos, you can use several methods to restore them:
Data Recovery Pro might help to restore files encrypted by Phobos ransomware
Originally, this software is designed to recover files after the system wreckage. However, it might be helpful after the ransomware attack.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Phobos ransomware;
- Restore them.
Windows Previous Versions feature might help to restore the most important files
Follow these steps to restore individual files after the ransomware attack (note: System Restore has to be enabled before the attack):
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might help to restore corrupted data
The Phobos virus should not delete Shadow Volume Copies, so this tool might be helpful:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Phobos decryptor is not available yet.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Phobos and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Jessica Kim Cohen. 10% of spam emails are 'malicious': 4 things to know. Becker's Hospital Review. Hospital business news and analysis for hospital and health system executives.
- ^ Tom Warren. Hackers hid malware in CCleaner software. The Verge. American technology news and media network.
- ^ Advanced Encryption Standard. Wikipedia. The free encyclopedia.
- ^ Danny Palmer. New Phobos ransomware exploits weak security to hit targets around the world. ZDNet. Technology news and analysis.
- ^ Lena Connolly, David Wall. Andrey Popov/Shutterstock Hackers are making personalised ransomware to target the most profitable and vulnerable. Theconversation. In-depth analysis, research and news.
- ^ Bitcoin Address. Blockchain. Digital wallets.
- ^ Viruset. Viruset. Norwegian security news.





















