CrySiS ransomware / virus (Virus Removal Guide) - updated Feb 2020
CrySiS virus Removal Guide
What is CrySiS ransomware virus?
CrySiS ransomware is an ever-evolving file locking malware that uses multiple attack vectors to infect thousands
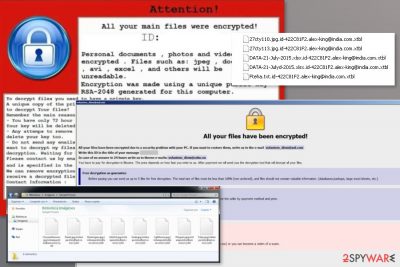
CrySiS ransomware, or otherwise known as Dharma, is a type of malicious software programmed to lock all personal files on the target system and hold them hostage until a ransom is paid in Bitcoins. Released in 2016, this malware mostly targets businesses and organizations with the help of various attack vectors, including targeted phishing emails, fake AV software installers, weakly protected RDP connections, and other methods. Malicious actors behind Ransom.Crysis ransomware release several new variants a month, each using different file extension that are appended to files after the locking process with AES, RSA and (sometimes) DES ciphers.
Once on the system, CrySiS ransomware prepares the machine for file encryption and then encrypts pictures, documents, databases, videos, music, and other files. The initial version appended .CrySis marker, although a multitude of different extensions has been used since then. A ransom note (such as README.txt, Decryption instructions.txt, Infohta, etc.) is also dropped to inform users about what happened to their files, and that they need to pay to retrieve access to them – crooks can provide CrySiS ransomware decryptor. Luckily, some of the Ransom.Crysis versions can be decrypted without paying criminals, as security researchers provided a working tool for free. For communication purposes, CrySiS virus authors provide two email addresses, such as 1024back@tuta.io or 2new2crypt@aol.com.
| Name | CrySiS |
| Type | File locking malware, cryptovirus |
| Alternative names | Dharma ransomware, Ransom.Crysis |
| Encryption algorithm | Malware employs a combination of RSA, AES and, in some cases, DES ciphers to lock all personal data, although it skips system and its own files |
| File extension | This malware family uses extended extensions, i.e., it does not only appends a short combination at the end after the dot, but also incorporates user ID, and a contact email into the affected fine names (example of an encrypted file: picture.jpg.id-3Y748R30.[Asdbtc@aol.com].asd) |
| Ransom size | Varies; the original version asked for 2.5 – 3 BTC |
| Ransom note | Malicious actors initially provided one ransom note README.txt; in later versions, two ransom notes are usually dropped on the system – Info.hta and FILES ENCRYPTED.txt |
| Contact | Crybercriminals use a variety of contact emails, depending on the version of malware |
| Decryption methods | unfortunately, only some of the older versions of CrySiS can be decrypted with the help of ESET [direct download], Avast [direct download] and Kaspersky [direct download] decryptors. Newest versions can only be decrypted by crybercriminals, although there is small chance of recovering at least some of the lost data with third-party software – check our recovery section below for details |
| Ransomware removal | You should remove CrySiS ransomware (after you make a copy of encrypted files, but before you attempt file recovery) with the help of reputable anti-malware software – perform a scan in Safe Mode if it does not work in normal mode |
| System fix | Ransomware alters the Windows registry and may corrupt system files. If you found your computer suffering from stability issues after malware termination, employ repair tool FortectIntego to fix virus damage on the system |
Ransom.Crysis infection and preparation routine
Before proceeding with the encryption routine, Crysis ransomware performs the necessary changes within the Windows operating system to lock all files on the hard drive, external drives, as well as networks without interruptions.
In most cases, users will be shown the User Account Control warning – if allowed, it will be impossible to stop the infection spread. A malicious executable then creates entries within %AppData%, %Temp%, or other folders, which consequently begins the infection process of Ransom.Crysis.
Here are some of the malicious changes performed by Ransom.Crysis ransomware virus:
- Makes changes within Windows registry to establish persistence
- Uninstalls anti-virus software (if the attack vector was performed via the RDP)
- Deletes Shadow Volume Copies by using vssadmin delete shadows /all /quiet command and disables Windows startup to prevent easy recovery
- Collects technical PC data and number of encrypted files on the system
- Attempts to escalate privileges on some Windows systems
- Sends appropriate information to Command and Control server
When malware succeeds in terminating anti-malware software within the computer, Crysis can operate without interruption. In such a case, we suggest accessing Safe Mode with Networking and dealing with the infection from there.
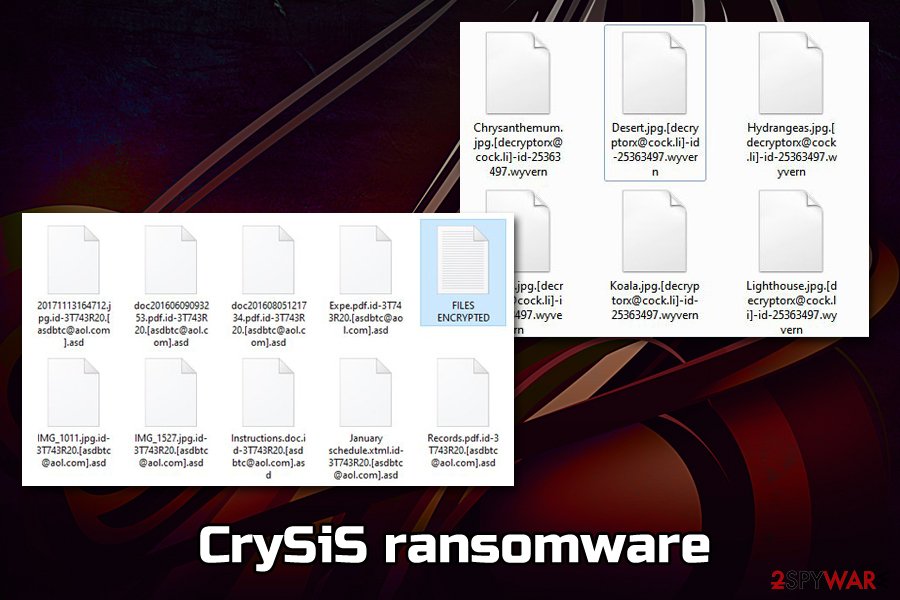
Crysis ransomware uses dozens of different file extensions and contact emails
The best-known versions of CrySis virus are Dharma ransomware and Arena ransomware. Due to similarities found in two of them, security experts often call the group of these two cyber threats as CrySiS/Dharma ransomware family.
There are hundreds of different file extensions CrySis ransomware uses to append files with after encryption, some of the previously used markers include:
- .dharma
- .locked
- .kraken
- .darkness
- .nochance
- .oshit
- .xtbl
- .wallet
- .wallet.lock
- .arena
- .java
- .ETH
- .KARLS
- .asd
- .ROGER
- etc.
Following data encryption, Arena CrySiS ransomware delivers a ransom note. Typically, it creates two files – HTML file that opens automatically on the affected screen, and the TXT file that is placed on the desktop. These files might be called Help_Decrypt_FILES.html, Help_Decrypt_FILES.txt, info.hta, Files encrypted!!.txt, etc. Authors of the malware tell victims to contact them in order to recover their files:
Attention! Your computer was attacked by virus-encoder.
All your files are encrypted cryptographically strong, without the original key the recovery is impossible! To get the decoder and the original key, you need to write us at the email: dalailama2015@protonmail.ch with subject “encryption” stating your id.
Do not waste your and our time on empty threats. Responses to letters only appropriate people are not adequate to ignore. P.S. only in case you do not receive a response from the first email address within 48 hours, please use this alternative email goldman0@india.com.
During the evolution of CrySiS virus, developers changed contact email addresses as well. Crooks are known for using these emails to communicate with victims:
- Tree_of_life@india.com
- Decryptallfiles@india.com
- Guardware@india.com
- mailrepa.lotos@aol.com.CrySiS
- cranbery@colorendgrace.com
- etc.
Security experts do not recommend following criminals’ instructions and paying the ransom. [1]Different versions of the virus demand to pay from 0.5 to 1 Bitcoin for the possibility to restore encrypted data. However, there’s no guarantee that crooks will keep their promise. Additionally, CrySiS ransomware, as well as some variants, are decryptable. Therefore, paying the ransom is a waste of money.

Before starting the data recovery procedure, you have to remove CrySiS ransomware from the PC. It’s necessary because while malware remains on the system, it can easily encrypt files repeatedly. Nevertheless, you should also copy over all the encrypted data before Ransom.Crysis termination if you have no backups available, as deleting malware might permanently damage files.
For CrySiS removal, you should employ SpyHunter 5Combo Cleaner, Malwarebytes, or other reputable anti-malware software. If you are having issues within the normal mode, you should access Safe Mode with Networking as per the instructions below. Then, proceed with data recovery procedures – the success rate depends on which version of CrySiS ransomware you are dealing with. Additionally, if you noticed that your machine works sluggishly or crashes, we suggest using FortectIntego for malware damage fix.
Crysis Master Key leaked: free decryptor is already here!
We have some great news for victims of CrySiS ransomware and for all victims infected with XTBL ransomware variants (these viruses typically append [victim's ID].[email@address].xtbl file extensions to encrypted data). Shockingly, an unknown individual has registered on one security-related Internet forum and shared master keys[2] for all variants of ransomware in November 2016.
The individual shared keys in the form of a header file, which gives an idea that he or she is very closely related to this ransomware project or even is one of its developers. .XTBL viruses are known to be greedy and ask for enormous ransoms, so we are sure that such news is going to bring a lot of joy for victims who have lost their files in the past.
If you are a victim of the Crysis ransomware project, we hope that you still have encoded files on the computer, because malware experts have rapidly used leaked keys to update a Crysis decryptor.[3] You can find its download link in data recovery instructions under this post. Good luck and stay safe!
Criminals switched from malicious spam emails to RDP attacks
Once Crysis malware emerged, it was distributed via malicious spam emails that included some infected attachment. If a victim was tricked into opening it, the malicious payload was dropped on the system.
However, in September 2016,[4] malware researchers reported about a new method which CrySiS ransomware uses to infiltrate computers. The virus now uses Remote Desktop Protocol (RDP) to infiltrate computers instead of the previously practiced distribution using spam emails and deceptive software updates. The first attacks were spotted in Australia and New Zealand.
This distribution strategy allows searching the Internet for unprotected RDP channels and connecting to them. The computer admin’s password required to do that can be extracted by brute-forcing malicious attacks and finding a crack in the system.
What is especially concerning is that after gaining access to the Remote Desktop Protocol, the cyber criminals can install CrySiS not only on the hacked computer but on other devices connected via the same network (printers, routers, NAS, etc.) or even brute-force their way into the nearby computers.
This technique is not unprecedented, though. It has been used by the DMA Locker, Apocalypse, and several other ransomware and was proven successful. The ever-developing viruses are yet another reminder of the importance of keeping ourselves protected [5].
Furthermore, in February 2017, TrendMicro research team[6] has revealed some staggering statistics, indicating that Crysis has doubled the number of brute force attacks against corporations and institutions just within the month of January 2017.
The parasite which had previously targeted mainly Australia and New Zealand is now expanding to the rest of the world, and the experts keep recording a growing number of attacks in Europe and US. The virus especially focuses on healthcare institutions and looks for ways to infiltrate their inner networks. Brazil, Argentina, and Turkey suffered from the malware the most.
In particular, the attacks are carried out by searching for open RDP ports and then identifying whether the devices connected to these networks are some corporate computers. If they find that this is the case, hackers continue the attack and brute-force their way into the targeted computers by cracking the login name and password.

Tips to avoid ransomware attack
One of the main reasons why Crysis ransomware is so successful is due to a variety of distribution techniques used by its authors. A more diverse approach allows malicious actors to infect users more efficiently, as many victims do not protect their PCs comprehensively.
Security experts prompt users to proceed with the following advice[7].
- Protect their computers with a reliable anti-virus and anti-spyware program.
- Enabling firewall.
- Install system and software updates regularly.
- Always check for the software updates on the official websites rather than downloading them from random sites.
- Do not open suspicious emails, especially spam.
- Avoid visiting obscure and unreliable file sharing websites.
- Refrain from downloading unknown software on your computer.
Since CrySiS is often spread via fake anti-malware software installers, it is important to download such files only from vendor's websites, and never trust pop-ups and notifications which claim that your system is infected and needs to be scanned with anti-malware software provided on the site.
Instructions to remove CrySiS virus
Please, do not try to remove CrySiS ransomware manually. It’s a complex cyber threat that makes numerous changes to the system and might inject malicious code into legit system processes. Therefore, you should rely on reputable security software and let it remove this cyber threat without causing more damage to the system.
For CrySiS removal we recommend using FortectIntego or Malwarebytes. However, there might appear obstacles which hinder successful elimination. But our team of experts has prepared instructions which should help you tame the virus and initiate the full system scan. Please check them below.
But before you do run the scan, make sure that your antivirus and malware removal utilities are updated to their latest version. Otherwise, the software may not be able to detect and delete CrySiS from your system, so the virus will continue rampaging on your computer.
Getting rid of CrySiS virus. Follow these steps
Manual removal using Safe Mode
To remove ransomware files with the help of Safe Mode, use a guide provided below:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove CrySiS using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of CrySiS. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove CrySiS from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Being a CrySiS ransomware victim, you can be offered by its developers (e.g. hackers) to purchase a decryption tool which will supposedly solve all of your problems and recover the files that it has locked. DO NOT do that! With the cyber criminals, you have no guarantees that you will receive the decryption key or that it will be able to decrypt the locked files. You better eliminate the virus from your PC using FortectIntego and use the data recovery methods provided below to try redeeming at least a small portion of your precious files.
If your files are encrypted by CrySiS, you can use several methods to restore them:
Opting for Data Recovery Pro method
Data Recovery Pro can be considered one of options capable of helping you recover your encrypted data. This program is designed to provide users the professional data recovery service. To use it properly, follow these guidelines:
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by CrySiS ransomware;
- Restore them.
Using Windows Previous Versions feature
Windows Previous Versions feature is one of system features helping users recover their data after unexpected changes. In this case, you can try using this feature to recover your data after ransomware attack. NOTE: this method only valid if the System Restore function is enabled.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer data recovery method
The third data recovery method employs ShadowExplorer software which relies on Shadow Volume Copies. With their help, this program can recover damaged files. However, in this case, it is really important to check whether the ransomware did not remove these Shadow Volume Copies. If you are lucky enough, follow these steps here:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
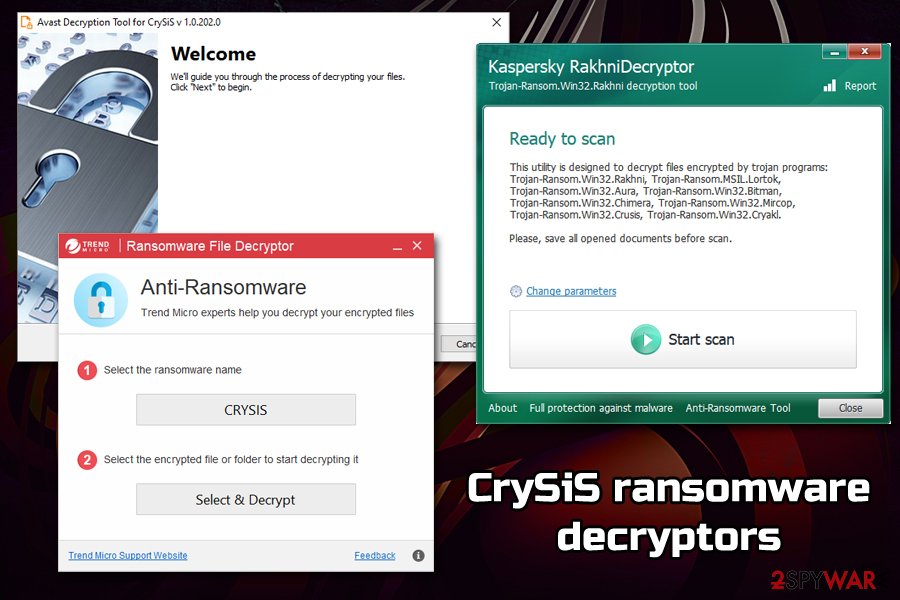
Using Crysis ransomware Decryptor
You can recover all your files for free using a special decryption software that has been updated on after one stranger leaked Crysis Master keys online. You can download the decryptor here. If you need more extensive details on how to use the decrytor, please check out the instructions provided by Kaspersky.
Additionally, other tools have been released that work with some Crysis versions:
- Trend Micro Ransomware Decryptor [download] [how-to guide]
- ESET Decryptor for Crysis Ransomware [download]
- Avast Decryptor for Crysis [download]
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from CrySiS and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Fahmida Y. Rashid. 4 reasons not to pay up in a ransomware attack. InfoWorld. Destination of choice for technology decision makers and business leaders.
- ^ Michael Mimoso. Crysis ransomware master decryption keys released. Threat Post. Security news.
- ^ Diego Perez. New decryption tool for Crysis ransomware. WeLiveSecurity. IT news, views and insight.
- ^ Pierluigi Paganini. CRYSIS Ransomware is back and crooks are using RDP attacks once again. SecurityAffairs. IT, security and hacking news.
- ^ Brenda Schmerl. 10 Ways to Protect Yourself Online. Reader's Digest. When professional meets personal.
- ^ Jay Yaneza. Brute Force RDP Attacks Plant CRYSIS Ransomware. TrendMicro Blogs. Security news, views and opinions.
- ^ Five Tips for Safe Web Surfing, Whether at Your Desk or On-the-Go. IT Business Edge.





















