Mapo ransomware (Removal Instructions) - Quick Decryption Solution
Mapo virus Removal Guide
What is Mapo ransomware?
Mapo ransomware is a file locking virus which stems from Outsider malware family
Mapo ransomware is a type of malware that focuses money extortion by blackmailing users to pay a ransom after locking all personal files on the infected machine. Just as many other malicious programs of such type, it enters host machines by using various deceptive methods and then encrypts all data by using a sophisticated encryption algorithm (RSA),[1] preventing victims from accessing their pictures, documents, videos, etc. Each of the files modified in such a way is marked by .mapo extension, for example, a picture.jpg is turned into a picture.jpg.mapo.
Additionally, Mapo virus also inserts a MAPO-Readme.txt file into most folders on the machine – it serves as a message from ransomware developers. Hackers claim that victims need to write an email to support.mbox@pm.me or support-mapo@pm.me with the attached ransom note to negotiate the ransom, which is paid in Bitcoin.
Mapo ransomware is a variant of Outsider, which itself stems from GarrantyDecrypt ransomware. This malware strain often targets businesses and organizations, so it encrypts all the files on the connected networks and drives as well. At the time of the writing, there is no Mapo decryptor available, and, while some victims managed to get their data back by paying criminals, some victims never got the decryption software even after paying.
| Name | Mapo |
| Type | Ransomware, cryptovirus |
| Malware family | Mapo belongs to malware strain known as GarrantyDecrypt-Outsider ransomware |
| Encryption method | The virus uses RSA encryption algorithm to lock all personal data located on the HDD and the connected networks/drives |
| File marker | Pictures, documents, databases, videos, music, and other data is appended with .mapo extension |
| Ransom note | MAPO-Readme.txt is placed into most folders on the system |
| Contact email | support.mbox@pm.me or support-mapo@pm.me |
| Ransom size | The ransom amount highly varies from victim to victims, but there are few known cases when the attackers asked for $2,000 – $4,000 in Bitcoin |
| Termination | Perform a full system scan in Safe Mode with reputable anti-malware software |
| File decryption | Only possible via backups or third-party recovery software |
| Recovery | To restore tour Windows system to pre-infection condition, use repair software FortectIntego |
Because Mapo ransomware aims to infect organisations mostly, it is highly likely that is uses one of the following popular malware delivery methods:
Nevertheless, malware authors can also use such methods as spam emails, software cracks, fake updates, web infects, and similar methods for Mapo virus propagation when it comes to regular users. Therefore, it is always important to install comprehensive security software that would prevent ransomware intrusions. Keep in mind that Mapo ransomware removal can also only be performed with anti-malware software. To recover from virus damage, we recommend using a PC repair tool FortectIntego.
Once the malicious executable is launched from the Desktop, Mapo ransomware performs a variety of changes to the system, including modification of Windows registry and Master Boot Record, Shadow Volume Copy deletion, etc. Once the system preparations are complete, the virus encrypts all the data on the host machine as well as all the connected networks and contacts a remote server, which allows the communication.
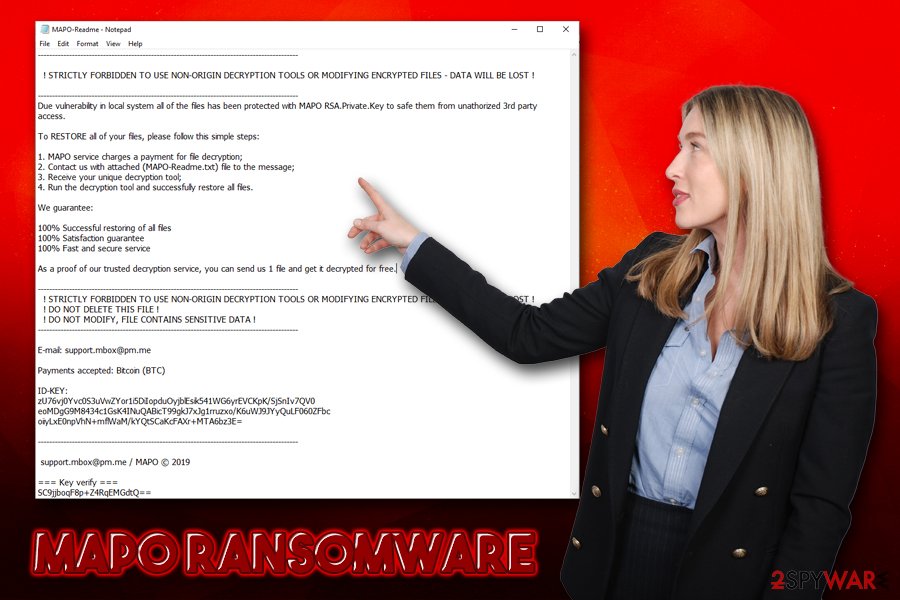
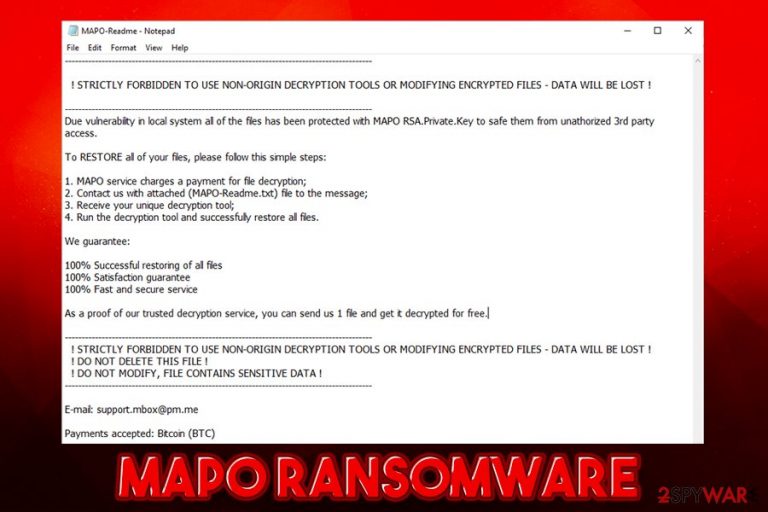
After that, users are presented with the MAPO-Readme.txt ransom note which states the following:
——————————————————————————————–
! STRICTLY FORBIDDEN TO USE NON-ORIGIN DECRYPTION TOOLS OR MODIFYING ENCRYPTED FILES – DATA WILL BE LOST !
——————————————————————————————–
Due vulnerability in local system all of the files has been protected with MAPO RSA.Private.Key to safe them from unathorized 3rd party access.To RESTORE all of your files, please follow this simple steps:
1. MAPO service charges a payment for file decryption;
2. Contact us with attached (MAPO-Readme.txt) file to the message;
3. Receive your unique decryption tool;
4. Run the decryption tool and successfully restore all files.We guarantee:
100% Successful restoring of all files
100% Satisfaction guarantee
100% Fast and secure serviceAs a proof of our trusted decryption service, you can send us 1 file and get it decrypted for free.
——————————————————————————————–
! STRICTLY FORBIDDEN TO USE NON-ORIGIN DECRYPTION TOOLS OR MODIFYING ENCRYPTED FILES – DATA WILL BE LOST !
! DO NOT DELETE THIS FILE !
! DO NOT MODIFY, FILE CONTAINS SENSITIVE DATA !
——————————————————————————————–E-mail: support.mbox@pm.me
Payments accepted: Bitcoin (BTC)
ID-KEY:
——————————————————————————————–
support.mbox@pm.me / MAPO © 2019
=== Key verify ===
While it is true that the key required to unlock all files is only accessible to the attackers and that the data might get corrupted after users remove Mapo ransomware, it does not mean that you should oblige to the demands. First of all, it is advisable to make a backup of the encrypted data and then get rid of the virus with anti-malware software.
As for .mapo file recovery, you can try using third-party recovery software if no backups are available to you, or if the malware encrypted backups as well. By all means, there is still an option of paying the ransom for the decryptor, but keep in mind that some users did not receive the tool even after paying a ransom of $2,000 – $4,000.
Protect your machine and all the connected networks from ransomware
Ransomware developers often operate large campaigns and release new versions of malware to obtain maximum profits from the illegal business. That being said, most hackers are sophisticated individuals who chose the wrong path for using their intelligence, as they are stealing money from innocent people. They also often openly laugh about users not being careful, or even indicate security flaws in the ransom note itself.
Regardless of how gruesome the ransomware business is, getting infected with the malware is something that can be avoided, along with as adequate security measures are practiced. The fundamental rule when it comes to cybersecurity is good online practices that are combined with adequate security tools that reinforce the protection even more. Here are some tips from industry experts[4] that will help you avoid most of malware in the future:
- Install reputable anti-malware software and keep it updated;
- Patch Windows along with all the installed applications with the latest security updates;
- Disable RDP when not used;
- Use adequate passwords and avoid default TCP port when using RDP;
- Never allow MS Office documents attached to emails to run macro commands by pressing “Enable Content”;
- Use strong passwords for everything and never reuse them;
- Use two-factor authentication where possible;
- Install ad-block to prevent malicious ads from executing the background scripts;
- Uninstall Flash Player and Java;
- Backup all your important files and keep them on a remote server or external device.
Mapo ransomware removal steps
While it is possible to remove Mapo ransomware manually, the process would require advanced computer and malware operation knowledge. Therefore, it is best to use reputable anti-malware software like SpyHunter 5Combo Cleaner or Malwarebytes to do the job. Be aware that malware is constantly evolving, so not all AV engines can recognize new variants straight away – in some cases, you might have to use several anti-malware tools until the malicious payload is terminated.
It is also worth noting that some Mapo ransomware removal might be prevented due to self-protection mechanisms, or the virus might disable anti-malware software altogether. To prevent that from happening, you should access Safe Mode with Networking and perform a full system scan from there.
When it comes to file recovery, it might be possible to recover at least some portion of .mapo encrypted files with the help of third-party recovery tools. The success rate of it declines the more infected machine gets used, and recovery software might not work at all. As previously mentioned, make sure you make a copy of all the encrypted files before you do anything. If the decryption with recovery software is unsuccessful, you should wait till security experts find a bug in the malware code or till law enforcement catches criminals, consequently making them release all the keys.
Getting rid of Mapo virus. Follow these steps
Manual removal using Safe Mode
If Mapo ransomware interferes with virus removal, access Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Mapo using System Restore
Use Safe Mode to get rid of the virus:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Mapo. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Mapo from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Mapo, you can use several methods to restore them:
Data Recovery Pro option
Data recovery software might recover at least some of the locked files, although it highly depends on how much the machine was used post-infection.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Mapo ransomware;
- Restore them.
Make use of Windows Previous Versions feature
If you had System Restore enabled, you might be able to retrieve files one-by-one.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might sometimes retrieve all your encrypted files
Mapo ransomware always attempts to remove Shadow Volume Copies. If this operation fails, ShadowExplorer might be able to recover all your files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryptor is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Mapo and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ RSA Algorithm in Cryptography. GeeksforGeeks. A computer science portal for geeks.
- ^ Jakub Křoustek. Ransomware attacks via RDP choke SMBs. Avast. Security blog.
- ^ Vulnerability (computing). Wikipedia. The free encyclopedia.
- ^ Dieviren. Dieviren. Cybersecurity advice from German experts.







