Markets adware (virus) - Free Guide
Markets adware Removal Guide
What is Markets adware?
Markets adware is a potentially unwanted application that might spoil your online time with ads

Markets is an adware application that might be installed on your computer without you realizing it. This can result in intrusive pop-ups, deals, offers, and in-text links appearing while you're browsing the web. If you notice this happening, it's likely that your computer is infected with adware.
The ads from Markets adware might not be safe. They often contain false information about your computer's health, try to get you to click on fake gift cards and other phishing[1] content. Instead of interacting with these ads, we recommend that you remove the adware from your computer as soon as possible.
This malware is only compatible with Windows-based machines, so Mac users can rest assured that they will not be affected. We'll provide more information on the virus and show you how to get rid of it from your computer in a manner that stops the obnoxious ads and other annoying issues it could cause.
| Name | Markets adware |
| Type | Adware, potentially unwanted application |
| Distribution | Software bundling, third-party websites, misleading ads |
| Symptoms | Shows intrusive advertisements, phishing material, and promotes other potentially unwanted applications |
| Risks | Markets ads may redirect to potentially harmful or even malicious websites, resulting in malware infection, personal information exposure, and financial losses |
| Related | Words, Drinker, Energy |
| Removal | The simplest approach to get rid of hazardous software from Windows is to use SpyHunter 5Combo Cleaner security software and then clean web browsers. |
| Other steps | After you eliminate all PUPs and malware, you should clean your browsers from cookies and other data to protect your privacy – you can use FortectIntego for that |
How you got infected with the Markets virus
Adware is notorious for its suspicious behavior and distribution. Many users, for example, find a potentially unwanted program on their computers without having installed it in the first place – or at least it seems so to many. This is just partly true, as adware seldom spreads through automatic channels such as software vulnerabilities[2] or spam emails. Misleading phishing notifications and bundled software installers are popular instead.
To avoid this undesirable situation, pay close attention to the installation procedure of free downloads from third-party sites. Selecting “Recommended/Quick settings” or omitting pre-ticked checkboxes frequently allows potentially unwanted or harmful software to get installed. Thus, you should always pay close attention to this process – pick “Advanced/Custom” settings when the option is given, decline all the offers of additional software, and watch out for fine print.
Fake ads are also a common way to spread adware. You should always watch out for messages or pop-ups which claim that something is missing from your system and needs to be installed. For example, you could be told that you need to install a particular font to view the page or that your Flash Player is out of date. Fake virus infection notices can also spread adware or malware.
Markets adware analysis
Adware is deceptive, and there may be times when unusual activity during web surfing sessions isn't noticed right away. Since those who don't use ad blockers might be subjected to highly intrusive advertising on numerous websites, they may not consider anything odd in general.
However, there are often symptoms of infection present that you should really pay attention to. For example, Markets adware infection can be spotted by the following symptoms:
- Ads are shown regularly, sometimes as pop-up messages;
- Clicks on links can lead you to other malicious websites;
- “Markets” program is installed on your system, which runs processes “Markets app 2022” and “Markets tech Copyright All rights reserved”;
- The adverts frequently request that you install fake Adobe Flash Player or other fraudulent computer software updates. Warnings about a virus on your system might also appear.

Removal explained
Deceptive software, like adware, is especially dangerous when installed as a system-level program. This allows it to root itself more deeply into the system and perform more damaging actions. For example, some might start running background connections with insecure domains or transferring data that makes people vulnerable to cyberattacks.
Although Markets adware is not always easy to spot, it is more dangerous because it resides on your system even after you uninstall the main app. In fact, the infection might return later because its files remain in the “AppData” folder.
The easiest way to eliminate all threats to your system is to scan it with powerful security software, such as SpyHunter 5Combo Cleaner or Malwarebytes. This way, you won't have to worry about leaving some malicious files running on the system by accident. Alternatively, you can proceed with the manual steps below:
Windows 10/8
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Windows 7/XP
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.
![Uninstall from Windows 7/XP Uninstall from Windows 7/XP]()
- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Once the main program is deleted, you need to remove the leftover files as follows:
- Press Win + E to open File Explorer
- At the top, go to the View tab
- Mark the Hidden items checkbox
- Next, go to your main drive (usually drive C) and enter the following path:
C:\Users\YOURUSERNAME\AppData\Roaming - Locate the Markets folder and delete it all.
Finally, you should delete cookies[3] and other web data from your browser to stop unwanted data tracking. Cookies are a popular tool utilized by adware, and Markets is no exception. It places and keeps cookies on the machines of its victims locally, allowing continuous monitoring of online activities, including their surfing history, search terms, advertisements viewed, technical device data, unique identifiers, and more.
You can easily get rid of all this leftover data with FortectIntego, although you can perform the manual steps below:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Internet Explorer
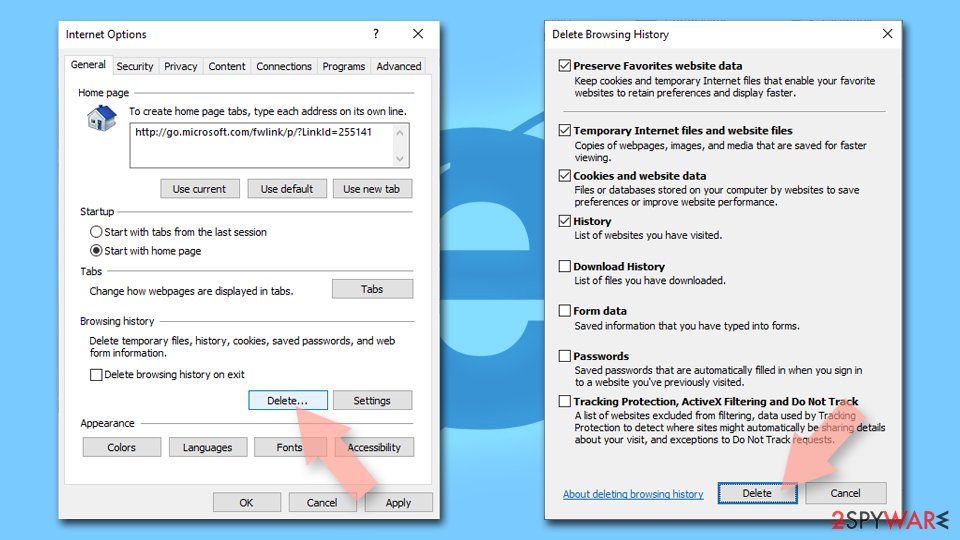
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
![Clear temporary files from Internet Explorer Clear temporary files from Internet Explorer]()
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Phishing attacks. Imperva. Application and data security.
- ^ homas Holt. What Are Software Vulnerabilities, and Why Are There So Many of Them?. Scientific American. Science Magazine.
- ^ HTTP cookie. Wikipedia. The free encyclopedia.