Memz virus (Removal Instructions) - Free Guide
Memz virus Removal Guide
What is Memz virus?
Memz virus is the custom-made trojan that overwrites Windows boot sequence with Nyan Cat meme animation

Memz virus is the trojan originally created by Leurak as viewer-made malware for the YouTuber Danooct1 that is distributed freely online.[1] Due to this spreading on the internet and destructive activity, it gained fame and popularity. This is a dangerous malware that runs many payloads and executes them one after the other. Although it shows internet memes this trojan is not a joke and can damage the machine because the more recent version of Memz trojan is especially destructive and once launched on a physical device it rewrites the operating system without the possibility to reverse these changes.[2] This is a trojan that can make significant changes in the infected machine and even access or steal data stored on the computer. Such malware can install additional programs on the PC after the initial infiltration.
There are at least two versions of MEMZ trojan: one harmless version, which people use for fun. This one delivers memes and doesn't run any malicious payloads. The second malware version is the one that affects the Master Boot Record by overwriting the first 64 KB of data of the hard drive and can cause serious damage to the operating system. If you have encountered Memz virus, you should take all the measures in order to delete the infection and restore the Windows system back to normal.
| Name | Memz virus |
|---|---|
| Type | Trojan |
| Originally created | As custom viewer-made malware by the YouTuber danooct1 |
| Main danger | It can wipe all the data from the machine permanently |
| Symptoms | Launches various processes, delivers pop-ups, crashes the system, and shows internet meme pictures, jokes. Launches system reboot and alter system changes |
| Distribution | Spam emails, infected files, other malware |
| Elimination | Rely on security software or anti-malware tool and remove MEMZ virus |
| System fix | Trojans can seriously damage any Windows system files, so it can start crashing or returning errors. If you want to attempt to fix this damage automatically, we recommend you try FortectIntego |
Memz virus was intended for fun, but malicious actors got a hold of the script and managed to distribute many more variants online. The initial malware had multiple warnings when the executable was about to be opened, but many users ignored them and allowed their machines to be infected anyways. Now trojan is distributed on the internet for various reasons and can be exceptionally malicious and damaging.
Memz trojan uses highly complex and unique payloads and activates them all one by one in a row. The first scripts are not that damaging, but the malware runs a few programs to make changes on the system and ensure the persistence. However, the final payload is the most harmful because it can lead to permanent damage and make the machine completely unusable.
Once installed, Memz virus has only a few symptoms that the infected users might notice:
- automatic web search results for disturbing things;
- programs or applications opened and closed out of nowhere;
- mouse cursor changing and moving;
- weird errors, system crashes.
Memz trojan manages to damage the computer or spread more malware on the already infected machine. It causes screen colors inverting every second, various web browser windows opening and closing, creating the tunnel effect and triggering reboots of the machine. In other words, if you are among the unlucky ones who are infected with it, you will not be able to operate your properly until you remove Memz virus from the system.
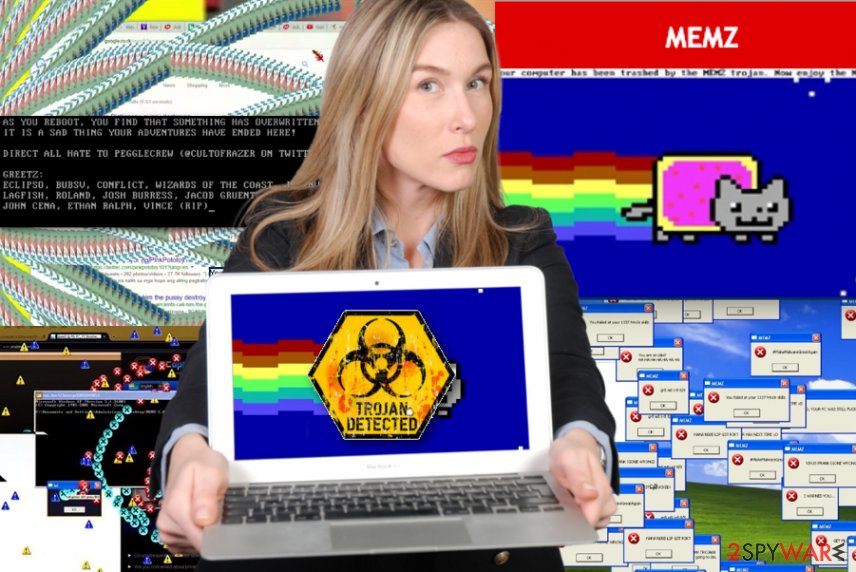
Once the virus made needed changes and infected the machine, you can encounter countless pop-ups appearing on the screen with internet memes or random pictures. While Memz virus can take over your desktop with all flashing and popping content, the more harmful feature which allows the infection to overwrite the data on the hard disk. Your Master Boot Record can get affected by this trojan.
When the machine cannot run the operating system, Memz virus delivers this message:
Your computer has been trashed by the MEMZ Trojan. Now enjoy the Nyan cat…
Memz virus even shows animation and plays sounds of the meme. This trojan compromises the machine and disrupts the system, but it also can install ransomware or other cyber threats and run additional programs or scripts. For that reason, you should react as soon as possible to terminate the trojan before it is too late.
You should remove Memz virus from the machine once you encounter any malware infection indicating symptoms and clean the machine using anti-malware tools. This is the best solution for any of the trojan versions. However, the destructive trojan variant overwrites the first 64 KB of the boot drive, so you need to use bootable recovery media like Windows installation disk. This way, you may recover the system, as experts[3] may recommend.
In other instances, employ an automatic anti-malware tool, such as SpyHunter 5Combo Cleaner or Malwarebytes, and scan the device entirely for the proper Memz virus removal. Keep in mind that if you open the Task Manager for the process, your computer will immediately crash, causing even more issues. So you should reboot the PC into Safe Mode and then perform a full system scan from there – we explain how below. After you delete the malware, you should also employ FortectIntego to fix any post-infection damage that Windows could have suffered in the process.
Trojans are typically distributed via spam emails or malicious scripts by cybercriminals
In most cases, threats like this malware get on the system from emails via infected files or background scripts loaded from fake updates/malicious websites. Those emails can pose as messages from customer support or shipping services because such emails are frequent when people tend to shop online these days.
Unfortunately, the common type and names of well-known companies or services help to trick users into opening the email and the file attached that contains malicious macros or direct virus payload. The only thing the user needs to do to launch the trojan or ransomware is to open the downloaded file on the machine.
However, such malicious threats can be delivered by the malicious actors themselves because criminals managed to deliver it online for free on various platforms and dark web forums. So victims may become affected during more targeted attacks. Keep paying close attention to emails and content you visit, click on, and get exposed to online to avoid cyber infections in the future.
Terminate the Memz trojan and clean the damage, other programs, and files
Since the malware categorizes as a trojan, it shows up on the machine out of nowhere and can run various processes besides the typical system changes and features that can be noticed by the victim. No matter which version of this trojan you got the full Memz virus removal is crucial for the system.
Make sure to remove Memz virus as soon as possible so damage can be avoided and the computer becomes virus-free again. We would recommend using professional anti-malware tools and rely on trustworthy sources to get the programs. Rely on SpyHunter 5Combo Cleaner, or Malwarebytes for malware elimination, and later scan the computer with powerful recovery software, such as FortectIntego – it would fix system lag, errors, or crashes due to damaged system files.
Getting rid of Memz virus. Follow these steps
Manual removal using Safe Mode
You may need some additional help to remove Memz trojan completely, so rely on Safe Mode with Networking and then try to scan the machine with anti-malware
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Memz using System Restore
System Restore feature might help to reverse the changes this trojan has made
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Memz. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Memz and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting trojans
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ MEMZ. github. Software development platform.
- ^ In response to the MEMZ trojan incidents.. Naswers. Microsoft community forum.
- ^ Virusi. Virusi. Spyware related news.







