META copyright infringement scam (fake) - Free Guide
META copyright infringement scam Removal Guide
What is META copyright infringement scam?
META copyright infringement scam attempts to steal your Facebook credentials
In the digital age, where social media acts as a global community, the darker side of the internet manifests itself through scams and deception. One such insidious scam currently gaining traction is the META copyright infringement scheme, primarily targeting popular Lithuanian accounts and major companies on Facebook.
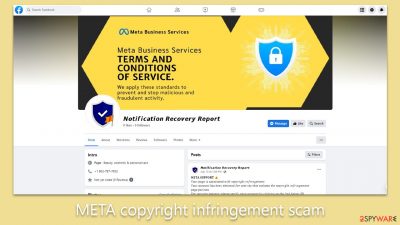
The perpetrator, operating under the pseudonym “Notification Recovery Report,” tags these accounts in posts and sends them fraudulent notifications alleging copyright infringement. For the so-called “security reasons,” the account owners are then coerced into verifying their page through a link provided in the message.
This malicious hyperlink, however, doesn't lead to Facebook's legitimate verification process but instead redirects users through a labyrinth of rogue websites. Many organizations heavily rely on their Facebook presence for business and community engagement, making this scam particularly disruptive and damaging. As we navigate our digital landscape, awareness and vigilance against such threats become paramount.
| Name | META copyright infringement scam, Notification Recovery Report |
| Type | Scam, phishing |
| Distribution | Facebook page tagging, email |
| Dangers | Potential theft of Facebook account credentials, redirects to other malicious websites, malware infection |
| Recovery | Scan the system for malware with SpyHunter 5Combo Cleaner and then remove data trackers with FortectIntego. Change your password and enable a multi-factor authenticator |
The message and what it is trying to achieve
Social media platforms, especially Facebook, are often targeted for scams or even for distribution of malware. A particular example of such malicious activity is the recent emergence of the “Notification Recovery Report” account.[1] Despite having zero followers, this account, created on July 10, 2023, has managed to stir up anxiety among popular profiles and large companies.
By exploiting Facebook's tagging feature, this account disseminates the same chilling message to dozens of profiles. The message alleges copyright infringement and reads:
META SUPPORT
Your page is associated with copyright infringement.
Your account has been detected for activity that violates the copyright infringement page policies.
For security reasons, please verify your account by clicking on the link below:
Account verification: hxxps://verification-account-page-meta.start.page.
If you don't confirm, our system will lock your account automatically and you won't be able to use it again.Thank you for helping us improve our account services. Community Messages Team Integration 2023.
The victims, concerned by the message, are directed to a sequence of rogue websites cloaked in the semblance of official Meta pages. These fake sites, filled with fraudulent notifications about supposed copyright infringements, scare users into sharing their sensitive information.
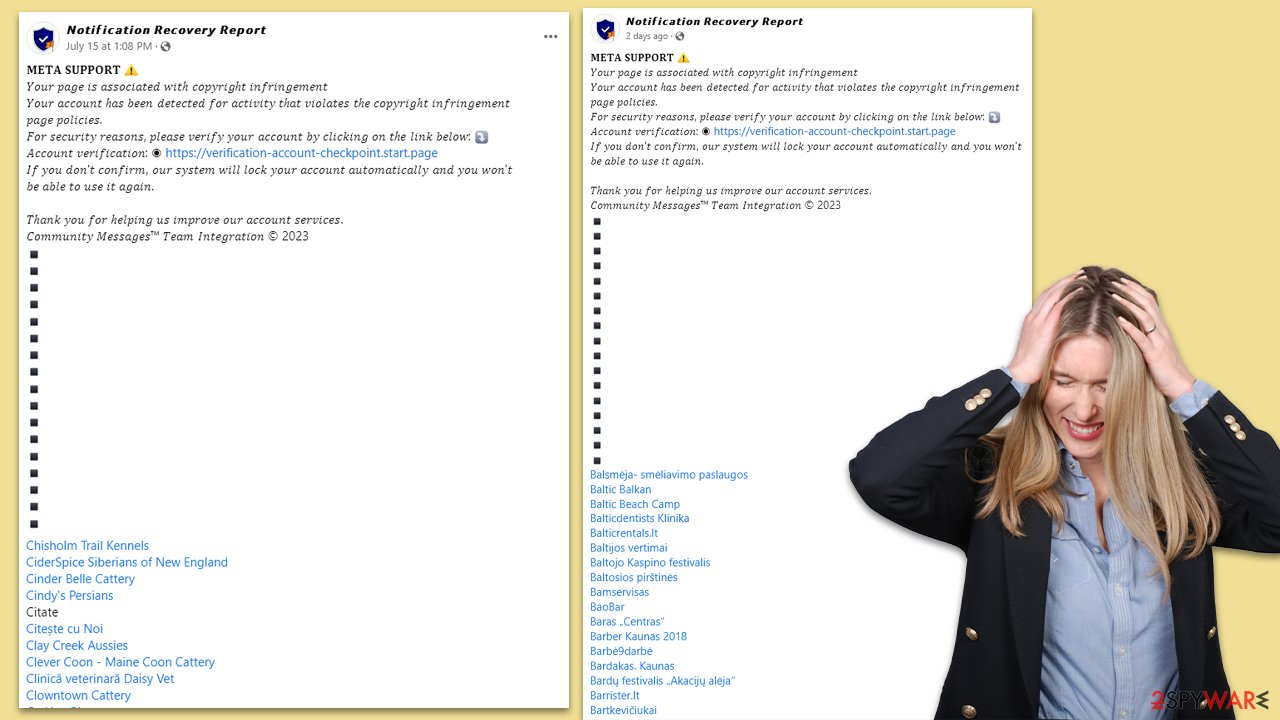
A glaring red flag is an intermediary page marked as “WARNING: Target Website May Be Unsafe!” The deceitful irony here is that the site displaying the warning is, in fact, an unsafe platform. Several internet security vendors have even classified this site as malicious. This then can lead to another malicious page,[2] where the data theft or malware installation can materialize.
The primary motive behind this scam is the theft of sensitive information. The orchestrated fear of losing access to their Facebook account prompts victims to provide whatever information is asked for, often their Facebook login credentials. In certain cases, they may also share more personal information, which could lead to identity theft.
As users, it's essential to be aware of such scams and remain vigilant when asked for sensitive data. Recognizing the signs of this scam is the first step towards safeguarding one's digital space. Never share personal information with unverified sources and remember, when in doubt, it's always best to seek professional advice.
Previous attempts to phish were focused on the distribution of malicious emails
The predecessor to the META copyright infringement scam began emerging even several years ago – these campaigns resurface all the time. These precursors, unlike the recent scam that unfolded directly on Facebook, primarily reached potential victims via misleading emails.[3]
The strategy involved sending counterfeit copyright infringement notifications, predominantly to organization accounts. These fraudulent emails generated a sense of urgency by threatening account suspension unless immediate action was taken. The messages made bogus claims such as, “Your account has been suspended. This is because your account, or activity on it, doesn't follow our Community Standards.”
The deceitful emails specifically pointed to an uploaded photo allegedly violating Facebook's copyright policies and threatened that, without an appeal within 24 hours, the user's account would face permanent disabling.
The emails cunningly included a link for users to appeal the decision, which, while appearing authentic at first glance, led unsuspecting users to a website designed to harvest their credentials. Despite the sender's email address being suspicious, the overall composition of the email was convincing, making it harder for the users to detect its fraudulent nature.
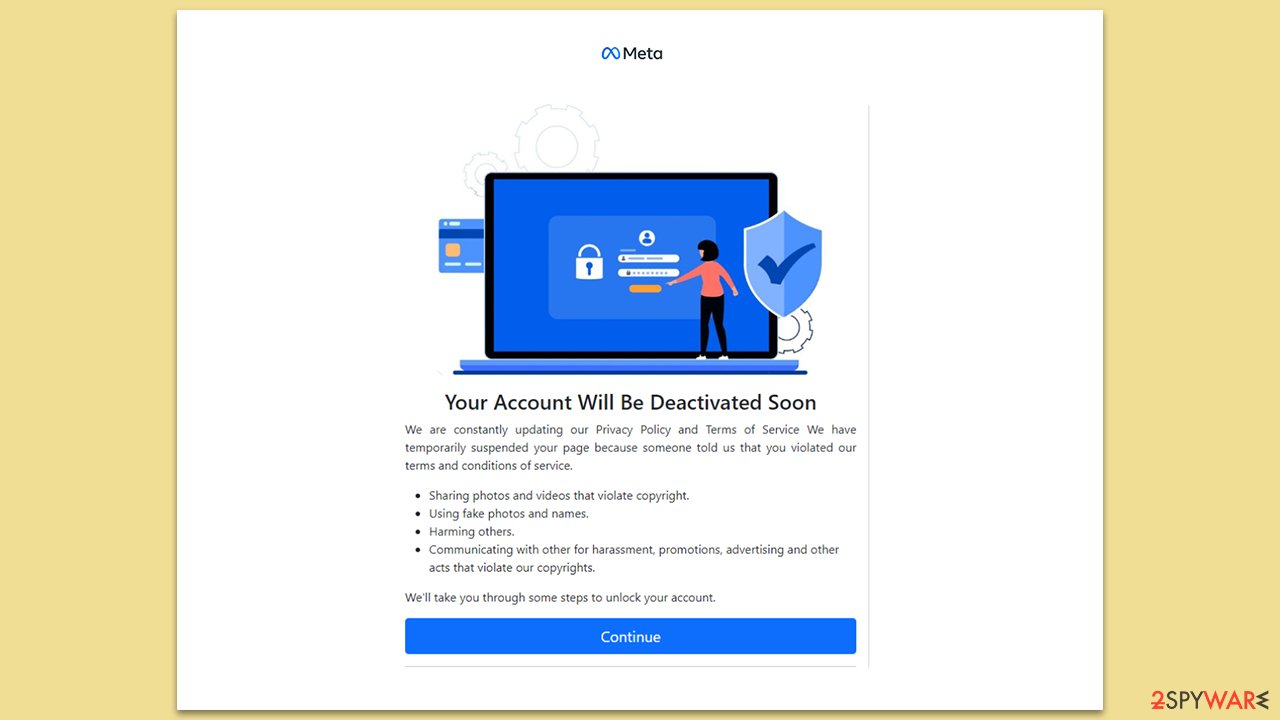
These deceptive tactics seemed to particularly prey on organizations heavily dependent on their Facebook pages for activities like advertising, brand awareness, and client interaction. Given the urgency and potential impact, the option to appeal appeared as a quick and reasonable solution. The consistent recurrence of such attacks suggested their success, demonstrating the effectiveness of the scam.
How to recover from being a victim of Facebook credential theft
Remaining vigilant and adopting good cybersecurity practices is essential to prevent falling victim to scams like the META copyright infringement scam on Facebook. One should always approach communications threatening account suspension or closure with skepticism, especially those demanding immediate action. In the online world, caution is the first line of defense.
A key protective measure is to verify the source of any received messages. Scammers often employ a technique called “email spoofing” to make their messages seem more legitimate. However, by cross-referencing the sender's details and examining the email for inconsistencies or errors, one can often spot a scam.
Hyperlinks within suspicious messages also pose a significant threat. It's advisable never to click on these. Instead, manually type the URL of the official website you're trying to reach into your browser. This reduces the risk of being redirected to a fraudulent site designed to steal your credentials.
Ensuring your passwords are regularly updated can also be a lifesaver. Adopt strong password practices: use a mix of letters, numbers, and special characters to make it harder for cybercriminals to guess your password. Adding an extra layer of security in the form of multi-factor authentication (MFA) can further protect your account by requiring a second form of verification.
If you find yourself already ensnared in the scam and have provided your credentials, it's crucial to take immediate action. Here are the steps you should follow:
- Change your Facebook password at once to prevent further unauthorized access.
- If the same password has been used for other online accounts, change those too. Scammers often try to exploit a single piece of stolen data across multiple platforms.
- Contact your bank or financial institutions if any financial information was involved. They can help secure your accounts and monitor for suspicious activity.
Once you've secured your accounts, it's time to safeguard your system:
- If you've visited malicious websites or clicked on malicious links, consider scanning your system for SpyHunter 5Combo Cleaner or Malwarebytes.
- To fix malware-caused system damage and clear your browser caches automatically, consider using the FortectIntego repair tool.
Swift action can mitigate the impact and prevent further harm.
How to prevent from getting spam tools
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Notification Recovery Report. Facebook. Social Network.
- ^ 16 security vendors flagged this URL as malicious. Virus Total. File and URL analysis.
- ^ Justinas Vainilavičius. Facebook users targeted in copyright infringement scam. Cybernews. Cyber Security News Today.
