Metoza.info browser hijacker (virus) - Free Guide
Metoza.info browser hijacker Removal Guide
What is Metoza.info browser hijacker?
Metoza.info – a browser hijacker that fails to provide secure search results
Potentially unwanted programs are very prominent, and thousands of users install them every day. While some people might get deceived by certain promises and install the app intentionally, most don't even notice how this sneaky software manages to get in. This is because of a deceptive distribution technique is known as software bundling[1] – where users are tricked into installing applications they otherwise wouldn't. Metoza.info is one of such deceptive apps, as it is not usually intentionally installed but along with freeware downloaded from third-party websites.
As soon as it manages to get on the system, it takes over the web browser immediately – be it Google Chrome, Mozilla Firefox, MS Edge, etc. The most significant visual and technical change lies within the alteration of the browser's homepage, which is set to Metoza.info.
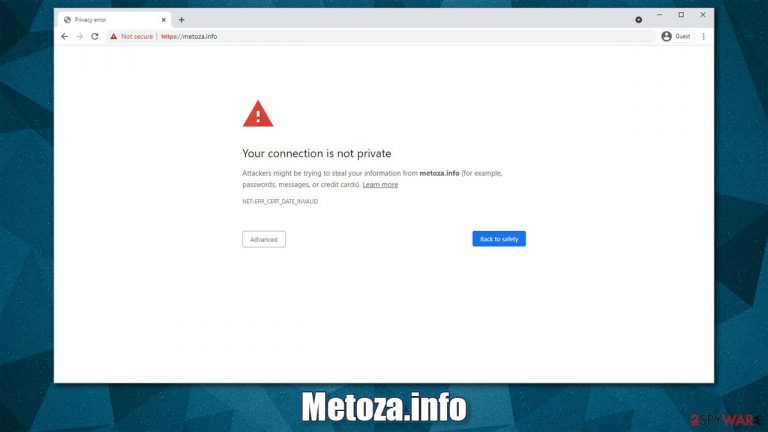
The implemented search bar alters search results in a negative way. In fact, the website itself does not use a security certificate, which prompts Google to deliver a security warning and an error message NET::ERR_CERT_DATE_INVALID. To make matters worse, the search bar fails to produce any results at all, making it useless in the first place.
If you have found unwanted changes in your browser, you should never ignore them, especially when they occur abruptly. There could be other potential programs or even malware[2] installed on your system, so you should make sure you check it properly.
| Name | Metoza.info |
|---|---|
| Type | Browser hijacker, potentially unwanted program |
| Distribution | Mostly software bundles, although deceptive ads are also used |
| Symptoms | A new extension is installed on the browser; homepage and new tab address are set to something else; a customized search engine is appended to the homepage; search results are filled with sponsored links and ads |
| Risks | Installation of other potentially unwanted programs, privacy risks due to information gathering practices, financial losses |
| Uninstall | Potentially unwanted programs can usually be removed manually, although automatic elimination with SpyHunter 5Combo Cleaner or Malwarebytes can be much quicker and more effective |
| Additional steps | Cleaning web browsers is an important step that needs to be undertaken. You can do that automatically with the help of FortectIntego |
What is a security certificate and why is it important
If you would type in the website's URL into your browser, you would likely get a warning saying:
Your connection is not private
Attackers might be trying to steal your information from metoza.info (for example, passwords, messages, or credit cards)
This is a standard warning from Google, which indicates that the security certificate, otherwise known as SSL certificate, is not being used or has been expired, which means that no encryption tool is used to secure data used by the site. If used, such a tool would encrypt all the incoming and outgoing connections, securing user information in the process (such connections use HTTPS protocol instead of HTTP).[3]
Typically, all reputable websites use these certificates in order to ensure that users' information is not in danger of being stolen by cybercriminals. Thus, websites that only employ HTTP connections are not considered to be secure and users should avoid them at all costs.
If you would utilize Metoza.info for your web browsing, all the information entered via the site could become visible to the attackers and then be stolen without you knowing anything about it. This issue is huge, all things considered; if you proceed using the search box provided by the hijacker, you might later suffer from the incoming phishing attacks or have your identity stolen.

Remove browser hijackers easily and clean your browsers
Browser hijackers are not considered malicious, generally speaking. Most of them come as browser extensions and can be easily eradicated. Nonetheless, there are plenty of problems that could come with these potentially unwanted programs during the elimination process.
For example, an app could be installed on the system level of your computer. In such case, uninstall it as follows:
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Mac
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

If you have noticed that your browser settings have suddenly changed, you should immediately perform a full system scan with SpyHunter 5Combo Cleaner, Malwarebytes or another reputable security software. This will ensure that there's no malware present on your computer. PUPs can also be removed by anti-malware tools, although that might not always be possible.
After you scan your machine and remove all the unwanted programs and extensions, you should take your time to clean your web browsers carefully. Various tracking technologies, such as cookies or web beacons, can be used to track you. These items can remain on your browser/computer even after the hijacker is removed. If you want to properly clean your PC (also to repair any system damage that could have been sustained due to an infection), we strongly recommend using the FortectIntego PC repair tool. Alternatively, you can clean browsers manually.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Ways to avoid potentially unwanted programs
Most people are not fond of browser hijackers, as nobody likes having their browsing preferences changed suddenly. Of course, there are always some people who are not particularly picky about such things, but one should concentrate on what matters the most – computer security and personal safety.
Thus, most users would not install potentially unwanted programs intentionally on their devices. To make them do it, PUP developers often come up with deceptive tactics to distribute their creations. Here are a few most popular ways:
- Software bundling is the most common distribution technique used by freeware distributors. The installers are packed with additional components, which are usually hidden from users' views. In order to avoid being a victim of it, you should always pick the Advanced/Custom installation settings instead of Recommended/Quick ones, untick all the pre-checked boxes (apart from ToS/Privacy Policy ones), read the fine print, and never rush through steps.
- Deceptive ads. Users can come across a pop-up ad that might claim various false issues. For example, the system is infected with viruses, or Flash Player/Chrome needs to be updated. All these statements are fake and should always be ignored. Always download software from the official sources – simply check the URL of the website that is offering you to download the allegedly needed software.
- Promotions. Potentially unwanted programs are often advertised through ads at the top of search results. They often have fake logos or fake comments from alleged users. These applications should generally be avoided, as they have plenty of negative features and can be considered potentially unwanted.
As evident, employing a powerful security tool, such as SpyHunter 5Combo Cleaner or Malwarebytes can improve your chances of avoiding the installation of suspicious and malicious software. Keep in mind that having good security practices is really important, as no anti-malware tool can protect your 100%. In fact, one of the main reasons why users get infected with ransomware such as Rigd or Efdc is because they ignore security software warnings after downloading software cracks.
How to prevent from getting browser hijacker
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Bundled Software. Techopedia. Professional IT insight.
- ^ Malware. Wikipedia. The free encyclopedia.
- ^ Why is HTTP not secure? | HTTP vs. HTTPS. Cloudflare. The Web Performance & Security Company.
