Microsoft Account Deactivation scam (fake) - Free Instructions
Microsoft Account Deactivation scam Removal Guide
What is Microsoft Account Deactivation scam?
Microsoft Account Deactivation is a fake message you might receive from scammers in your email
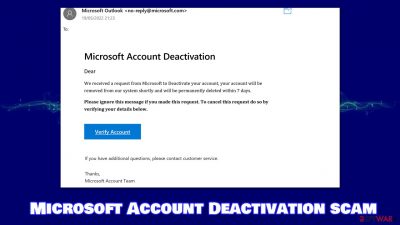
Microsoft Account Deactivation is an email scam you might receive one day unexpectedly. Many users are unpleasantly surprised by it, as they have not requested an account deactivation service. This makes many people wonder whether or not the email is legitimate and can be trusted – the answer is no.
Upon receiving the email, users are warned that their Microsoft accounts will be permanently deleted within seven days, as the request has been received to do so. They are also notified that they should click the link below to verify their account if this request has been made by accident.
Users who click the “Verify Account” link would be redirected to the Microsoft spoofing site,[1] where they would be asked to enter their account name and password. Unknowingly, victims of the Microsoft Account Deactivation scam would be providing their account details directly to cybercriminals, which can later be used for other malicious purposes.
| Name | Microsoft Account Deactivation |
| Type | Scam, phishing email |
| Distribution | The fake message is received via email |
| Dangers | Personal account detail disclosure to cybercriminals, malware infection |
| Malware removal | If you have clicked links and downloaded files, we recommend you perform a full system scan with SpyHunter 5Combo Cleaner security software |
| Remediation tips | Scan your device with FortectIntego to repair damaged system files and remove trackers; make sure you change your password for your Microsoft account if you have disclosed it to unknown parties |
The fake message and what to expect
Spam and phishing[2] emails are something that has been around for decades now, as it makes an effective method of malware distribution. Opening booby-trapped MS Office documents, for example, are among the most prevalent ways of getting your system infected with malware.
Not all email spam is dedicated to malware. There are plenty of fake messages that pretend to come from legitime, high-profile sources such as Netflix or Amazon, which attempt to steal user credentials of the said account. For example, if you are using Netflix, you could receive a fake email claiming that your account was compromised and you have to verify it by entering your credentials – that's where a hyperlink to a spoofing website is provided.
Here, we are dealing with this example's analogy, apart from it using Microsoft's name instead. Here's the full message you might expect when dealing with the Microsoft Account Deactivation email:
Microsoft Account Deactivation
Dear
We received a request from Microsoft to Deactivate your account, you accoint will be removed from our system shortly and will be permanently deleted within 7 days.
Please ignore this message if you made this request. To cancel request do so by verifying your details belowVerify Account
If you have additional questions, please contact customer service.
Thanks,
Microsoft Account Team
What is relatively unique about this scam is that it's crafted rather carefully – it contains no grammar or spelling mistakes, and the email address it was sent from seems relatively familiar – “no-reply@microsoft.com.” However, it is important to note that the email is not that of a legitimate Microsoft account team and is simply a fake. You should only trust emails that use “@accountprotection.microsoft.com” instead.
Those who fail to recognize the deception and click the “Verify Account” button might be redirected to a fake Microsoft page, where they will be asked to enter their account credentials. The website would look identical to that of Microsoft's official one and might be impossible to identify visually.
How to avoid being scammed
Spam campaigns are extremely prevalent due to malware-infected machines that form a so-called botnet.[3] Unknowingly to those affected, their computers automatically send out phishing messages to hundreds of other victims. In some rare cases, phishing emails are sent out by humans, too, although this usually manifests as a targeted attack against an organization or a business rather than a regular computer user.
Here are some tips that should help you from being tricked by scams similar to Microsoft Account Deactivation:
- Look at the sender's email – it is often not what you might expect to receive from an official company account.
- The sender's email might be similar to an official one or might be deliberately misspelled.
- An email address might also be spoofed, so you should still be skeptical, even if the address is legitimate.
- Look for grammar and spelling mistakes, formatting failures, and similar.
- If the email ends in the Junk email section, delete it immediately without interacting.
What to do next?
First of all, please do not interact with the email – do not click any links or download software if offered. You can easily expose your personal information to cybercriminals, resulting in further phishing attacks or even identity fraud. Likewise, links on spam emails might lead to malicious websites where malware could be downloaded and installed.
If you have unfortunately interacted with the email, such as clicked links and disclosed your personal information, you could expect to receive more phishing attempts coming your way. For example, you might receive more emails or phone calls that would include your personal details – be wary.
If you have downloaded something from the email or clicked links, we recommend you immediately scan your system with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful security software to make sure that there's no malware on your device. If something is indeed found, it will be deleted immediately. Using FortectIntego is also beneficial in such cases, as you could fix any system damage that could have occurred due to infection.
We also recommend reporting the incident to your local authorities that deal with fraud. You might find the following links useful:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
How to prevent from getting spam tools
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ What is Spoofing – Definition and Explanation. Kaspersky. Security research blog.
- ^ Phishing. Wikipedia. The free encyclopedia.
- ^ What is a botnet?. Malwarebytes. Official webiste.
