Mobili adware (Free Instructions)
Mobili adware Removal Guide
What is Mobili adware?
Mobili adware is a potentially unwanted application you should get rid of
Mobili is an adware[1] program that may have been installed on your computer without your knowledge. This can lead to the appearance of unwanted pop-ups, discounts, promotions, and in-text links while you're surfing the internet. If you experience this, it's probable that your computer has been infected with adware.
The ads generated by Mobili adware may not be secure. They frequently display misleading information about the status of your computer, attempting to lure you into clicking on counterfeit gift cards and other phishing-related content. Rather than engaging with these ads, we advise that you eliminate the adware from your computer as quickly as possible.
This malicious software is only compatible with Windows-based systems, so users of Mac computers can rest easy knowing they will not be affected. We will provide further details on the malware and guide you through removing it from your computer, effectively putting an end to the aggravating ads and other potential problems it may create.
| Name | Mobili adware |
| Type | Adware, potentially unwanted program |
| Distribution | Software bundling, third-party websites, misleading ads |
| Symptoms | Shows intrusive advertisements, phishing material, and promotes other potentially unwanted applications |
| Risks | Shown ads may redirect to potentially harmful or even malicious websites, resulting in malware infection, personal information exposure, and financial losses |
| Removal | The easiest way to eliminate adware from a Windows computer is by using SpyHunter 5Combo Cleaner security software and then cleaning out web browser caches |
| Other steps | After you eliminate all PUPs and malware, you should clean your browsers of cookies and other data to protect your privacy – you can use FortectIntego for that |
Operation
Mobili is a malicious program that takes over your browser homepage and search engine, displaying unwanted ads unrelated to the websites you visit. It can be challenging to identify unusual activity during web browsing sessions, especially for users without ad blockers who may already experience intrusive advertising on various sites.
Nevertheless, there are often signs of infection that warrant your attention. For instance, the presence of Mobili adware can be indicated by the following symptoms:
- Frequent display of ads, including pop-up messages.
- Clicking on links may redirect you to other malicious websites.
- The “Mobili” program is installed on your system, running various background processes with similar names.
- Ads often prompt you to install fake Adobe Flash Player or other deceptive software updates and may also display false virus warnings on your system.
Upon installation, the Mobili browser hijacker alters your search queries, directing them through questionable search engines. Additionally, it opens new tabs in your browser showcasing ads that attempt to sell software, promote counterfeit software updates, and propagate tech support scams.
By staying vigilant and recognizing these signs of infection, you can take the necessary steps to protect your computer from the harmful effects of adware.

How to protect yourself from adware and other threats
Adware is infamous for its deceptive behavior and methods of distribution. Many users often discover a potentially unwanted program on their computers without intentionally installing it – or so it appears. While it's true to some extent, adware rarely propagates via automated channels like software vulnerabilities[2] or spam emails. Misleading phishing alerts and bundled software installers are more commonly employed.
To sidestep this undesirable circumstance, be vigilant during the installation process of free downloads from third-party websites. Opting for “Recommended/Quick settings” or overlooking pre-selected checkboxes often permits potentially unwanted or malicious software to infiltrate. Therefore, always exercise caution during this procedure – choose “Advanced/Custom” settings when available, reject all proposals for supplementary software, and keep an eye out for the fine print.
Adware also frequently spreads through fraudulent advertisements. Be wary of messages or pop-ups claiming that something is absent from your system and requires installation. For instance:
- You might be informed that a specific font is necessary to view the page.
- You could be told that your Flash Player is outdated.
- False virus infection warnings might also distribute adware or malware.
By remaining cautious and staying informed about these deceptive tactics, you can better protect your computer from the unwanted effects of adware like Mobili.
Removal guide
Adware becomes especially dangerous when installed as a system-level application. This allows it to penetrate more deeply into the system and carry out more damaging activities. For example, it may create background connections to unsecured domains or transmit data that exposes users to cyberattacks.
Adware's stealthy nature makes it difficult to detect, and the threat it poses is heightened since it lingers on the system even after the primary application is uninstalled. The infection might even reemerge later, as its files persist in the “AppData” folder.
To effectively eradicate all potential risks to your system, the most direct method is to perform a scan using trustworthy security software, such as SpyHunter 5Combo Cleaner or Malwarebytes. Doing so can prevent inadvertently leaving any harmful files active on the system. Alternatively, you can follow the manual steps provided below:
Windows 10/8
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Windows 7/XP
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
After the elimination of the main program, you should also make sure to remove its remnants that would reside in the AppData folder as follows:
- Press Win + E to open File Explorer
- At the top, go to the View tab
- Mark the Hidden items checkbox
- Next, go to your main drive (usually drive C) and enter the following path:
C:\Users\YOURUSERNAME\AppData\Roaming - Locate the Tidings folder and delete it by pressing Shift + Del on your keyboard.
Taking care of your browsers
In order to avoid undesired data monitoring, it's crucial to remove cookies and other internet data from your browser. Adware commonly uses cookies for tracking purposes, and Mobili is no different. It saves cookies on the affected user's computer, allowing ongoing surveillance of their online actions, including browsing history, search queries, viewed advertisements, device details, unique identifiers, and more. The most straightforward approach to clean browsing data is by utilizing the maintenance tool FortectIntego. However, if you prefer manual methods, the steps are provided below.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

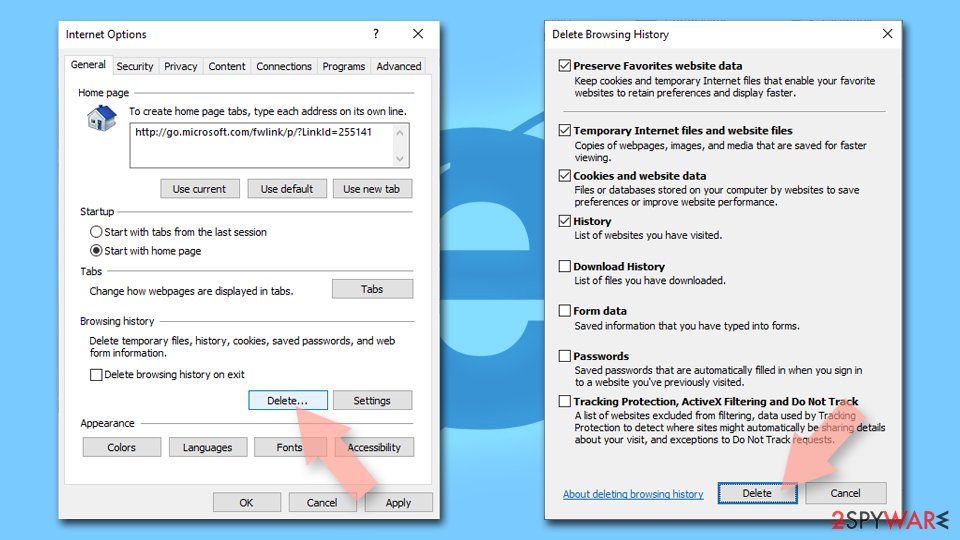
Internet Explorer
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Will Kenton. Adware. Investopedia. Source of financial content on the web.
- ^ What Are Software Vulnerabilities, and Why Are There So Many of Them?. Scientific American. Science Magazine.
