Montserrat ransomware (Recovery Instructions Included) - Virus Removal Guide
Montserrat virus Removal Guide
What is Montserrat ransomware?
Montserrat ransomware – dangerous malware that adds the .encrypted backup appendix to each locked component
Montserrat ransomware, also known as BaCkUp ransomware, is a newly-released cyber threat that uses both an appendix and file marker to sign encrypted files and documents. The main targets are English-speaking users that employ Windows machines for their computing work. The stealth infiltration begins with a spam message or software crack. After opening such content, Montserrat virus ends up on the machine and starts modifying registries. The malware also brings the Backup.exe executable to the system which allows the parasite to fulfill its module. This leads to the secret encryption of various files and all data ends up with the .encrypted_backup appendix and the .BaCkUp file marker. Afterward, the cyber threat provides the How to the restore data.html message where the crooks' demands are expressed. These people require to write them via montserrat501@protonmail.com or montserrat501@airmail.cc email addresses and offer to send a file that holds no larger of size than 10 MB to receive evidence that the decryption software truly exists.
| Name | Montserrat ransomware |
|---|---|
| Category | Ransomware/malware |
| Danger level | High. Locks files that can result in permanent data loss, can modify various system directories, and infiltrate other malicious strings such as trojans |
| Appendix/file marker | Once all the files are encrypted by using the Advanced Encryption Standard, the components end up with the .encrypted_backup extension and the .BaCkUp file marker |
| Target | Regarding the language in which the ransom note is written, the hackers are targetting people who speak English and live in English-speaking countries |
| Ransom note | All the demands are provided in the How to the restore data.html ransom message |
| Emails | The criminals provide montserrat501@protonmail.com or montserrat501@airmail.cc email addresses as a way to contact these people and receive further payment instructions |
| Distribution | The most common distribution sources of ransomware infections include email spam messages and their infected attachments, software cracks, and malicious software updates |
| Removal | You should opt for the removal process ASAP before the ransomware provides any more damage. For this purpose, employ reliable antimalware software |
| Fixing | If you have discovered some system locations that have been touched by the ransomware or additional threats, you can try repairing your machine and its components with software such as FortectIntego |
Montserrat ransomware is detected by 46 AV engines at the time of writing. According to VirusTotal file detection information,[1] some of the detection names include Trojan.GenericKD.42093054, Win32:RansomX-gen [Ransom], Trojan.Win32.Zudochka.dtd, Ransom.Montserrat, Trojan.Encoder.30337, Trojan.TR/FileCoder.ofeiy, and others.
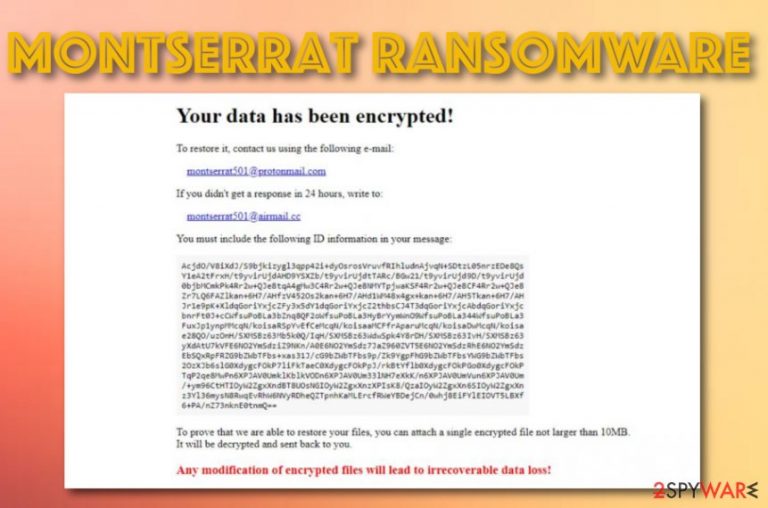
Montserrat ransomware does not provide any particular ransom demands via the ransom message, however, the criminals are most likely to urge for cryptocurrencies such as Bitcoin (the most popular one), Litecoin, Monero, or Ethereum as these types of transfers ensure the anonymity of the entire process. Take a peek how to the ransom note looks like:
Your data has been encrypted!
To restore it, contact us using the following e-mail:
montserrat501@protonmail.com
If you didn’t get a response in 24 hours, write to:
montserrat501@airmail.cc
You must include the following ID information in your message:
[Redacted] To prove that we are able to restore your files, you can attach a single encrypted file not larger than 10MB.
It will be decrypted and sent back to you.
Any modification of encrypted files will lead to irrecoverable data loss!
Montserrat ransomware uses an AES encryption cipher[2] to lock up all components that are found on the computer. The malware targets files such as databases, images, audio, video, excel sheets, word documents, powerpoints, and similar data. After the locking, both encryption and decryption keys are safely stored on remote servers.
Montserrat ransomware developers might try to harden the decryption process for you. They might have included a specific module into the ransomware that allows it to execute PowerShell commands and eliminate the Shadow Volume Copies of all encrypted files. This way the chances of decrypting data independently lessen.

Furthermore, Montserrat ransomware might hold other commands and modify locations such as the Windows Registry and Task Manager for carrying out its activities. Sometimes, this type of malware ensures that the system will be scanned for encryptable files and documents once in a while, for example, half an hour.
Continuously, Montserrat ransomware will make sure that it is loaded every time when you boot your Windows computer system, it might end up disabling some antivirus software and modifying the Windows hosts file. The last activity is carried out to prevent you from visiting security-related websites where you might get valuable information on the virus's removal.
In addition, Montserrat ransomware can bring other malicious products to the system, this way you will have to different types of malware operating on your machine at once. The risk of system and software damage will definitely increase if your computer system receives such type of infection as a Trojan virus.
The only way to avoid such risk is to remove Montserrat ransomware from your Windows computer system by employing reliable software. However, if the ransomware virus has already managed to bring other threats into your machine, they will need to be eliminated too. If some damage was caused to your computer, try using FortectIntego to repair it.
If your antimalware is somehow failing to detect the ransomware or you have run into difficulties while performing the Montserrat ransomware removal process, you should boot your machine in Safe Mode with Networking or activate System Restore. We have provided some instructing steps on these two methods, take a look at the end of this article.
One more tip from our side would be not to pay the Montserrat ransomware cybercriminals as you can easily get scammed. These people might urge for a big price between $200 and $2000 in Bitcoin or another type of cryptocurrency that you will not receive back. Instead of risking in your money, go to the end of this page and find some alternative data recovery tips.
Ransomware often gets delivered via cracked software and email spam
Cybersecurity experts from LosVirus.es[3] claim that ransomware virus ends up on the system by using multiple deceptive techniques. However, the most commonly used infiltration methods are the following ones:
- Email spam. When the malware gets delivered via phishing email messages and their clipped attachments/links included. The criminals pretend to be from reliable shipping organizations such as FedEx or from other well-known firms/institutions that are related to banking, healthcare, education.
- Software cracks. A big variety of illegitimate products and services are distributed on peer-to-peer networks[4] such as The Pirate Bay, eMule, and BitTorrent. These websites have weak protection and crooks can easily misuse them for their malicious purposes.
- Fake software updates. Some ransomware infections are spread via fake JavaScript, Adobe Flash Player, or other types of updates. The updating windows might pop up whenever visiting an unsecured source and start encouraging you to download a particular upgrade for your outdated software.
These are just the most popular techniques that are used for spreading ransomware but there, of course, are many more of them, for example, exploit kits, malvertising, malicious links, PUPs, etc. The best way to protect yourself is to take all security measures seriously. You should be careful with all the emails that you receive and always identify the sender.
If the email message comes with suspicious attachments, links, or a lot of grammar mistakes included, you should delete the message right away. Continuously, do not download software from unreliable sources such as p2p networks. Get all of your products from original developers and avoid installing malware via software cracks.
Continuously, do not download any unknown updates. If you have been randomly provided with an upgrade, you should check the app's official website and look for pending updates there. Last but not least, always have an active antivirus tool that will inform you if something potentially malicious is trying to invade your computer system.
The removal process of Montserrat ransomware
Montserrat ransomware removal is a process that should be completed with big care and requires a lot of effort. You should not try to eliminate the malware without using antimalware help. Manual elimination is not a possibility in this case and you might easily fail while trying to get rid of the cyber threat on your own.
Continuously, the automatical system software is more capable to remove Montserrat ransomware from all infected locations on the computer. The program will scan the entire machine and search all potentially affected directories. Afterward, the automatical program will be able to deal with the cyber threat safely and effectively.
When Montserrat ransomware is gone, it is time to search for system damage. You can employ software such as SpyHunter 5Combo Cleaner or Malwarebytes and perform a full machine checkup process with these programs. When the scan results show which locations have been damaged, you can try fixing them by employing another tool such as FortectIntego.
Getting rid of Montserrat virus. Follow these steps
Manual removal using Safe Mode
To disable malicious processes on your Windows computer system, you should boot your machine in Safe Mode with Networking. Apply this function by completing the following guidelines:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Montserrat using System Restore
To deactivate malware-laden activities on your machine, start the computer in System Restore. Turn this feature on by completing the following steps:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Montserrat. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Montserrat from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Montserrat, you can use several methods to restore them:
Data Recovery Pro might help you with file restoring purposes.
Try this software if the ransomware virus has encrypted your data files and documents. Perform all steps as required to reach the best results possible.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Montserrat ransomware;
- Restore them.
Try using Windows Previous Versions feature for data restoring tasks.
Try using this piece of software if you have enabled the System Restore function in the past, otherwise, you might not receive delighting results.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer might allow you to recover some individual files.
If the ransomware virus has erased or permanently damaged the Shadow Volume Copies of encrypted data, this software might not be that helpful as expected.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, no official decryptor has been released for this cyber threat.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Montserrat and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ 46 engines detected this file. Virus Total. File information.
- ^ Advanced Encryption Standard. Wikipedia. The free encyclopedia.
- ^ LosVirus.es. LosVirus. Security and spyware news.
- ^ What is a P2P network?. Quora.com. Relevant questions and answers.







