N1ghTm4r3 email scam (Removal Guide) - Free Instructions
N1ghTm4r3 email scam Removal Guide
What is N1ghTm4r3 email scam?
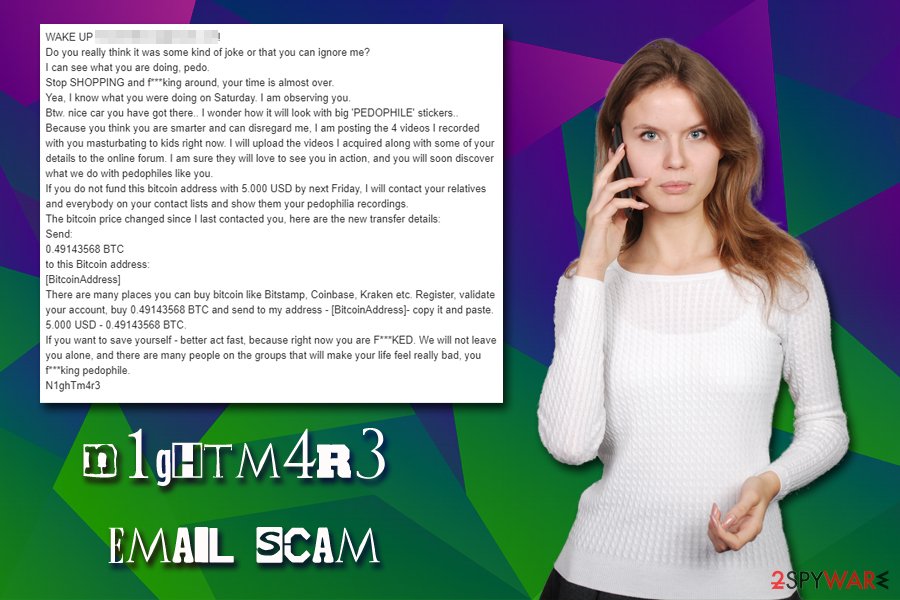
N1ghTm4r3 email scam is a blackmail campaign accusing users of watching child pornography

N1ghTm4r3 email scam is yet another sextortion scam that recently reached users in the US and the UK. Threat actors behind the message claim that the they implanted a spyware program on the host machine which allowed them to hijack their camera and record a video of them watching illegal pornographic content. In order to stop the attackers from posting the allegedly captured images of a private act on social media, online forums, as well as contact list, users have to pay as much as $5,000 in Bitcoin (or £5,000 in the UK). As evident, N1ghTm4r3 email is just a scam, and users should never transfer the demanded money.
While it is highly unlikely that your machine is infected with spyware or any other type of malware, it is known that previous sextortion campaigns introduced such threats to users' machines as banking Trojans and ransomware. Therefore, if you clicked on any links inside the N1ghTm4r3 email, you should immediately scan your computer for malware.
| Name | N1ghTm4r3 email scam |
| Type | Sextortion scam |
| Claims | The email claims that the user was watching child porn, and the act was recorded with a hijacked web camera |
| The demand | Email authors demand $5,000 to prevent the sensitive content from being posted on public forums and other places |
| Related | Porn Blackmail virus, Extortion scam |
| Demographics | Targets users in the USA and the UK |
| Further actions | Never pay the demanded money in Bitcoin; instead, contact local authorities that deal with scam and report the incident. Then scan your device with anti-malware software (we suggest FortectIntego, SpyHunter 5Combo Cleaner) and change all your passwords as a precaution measure |
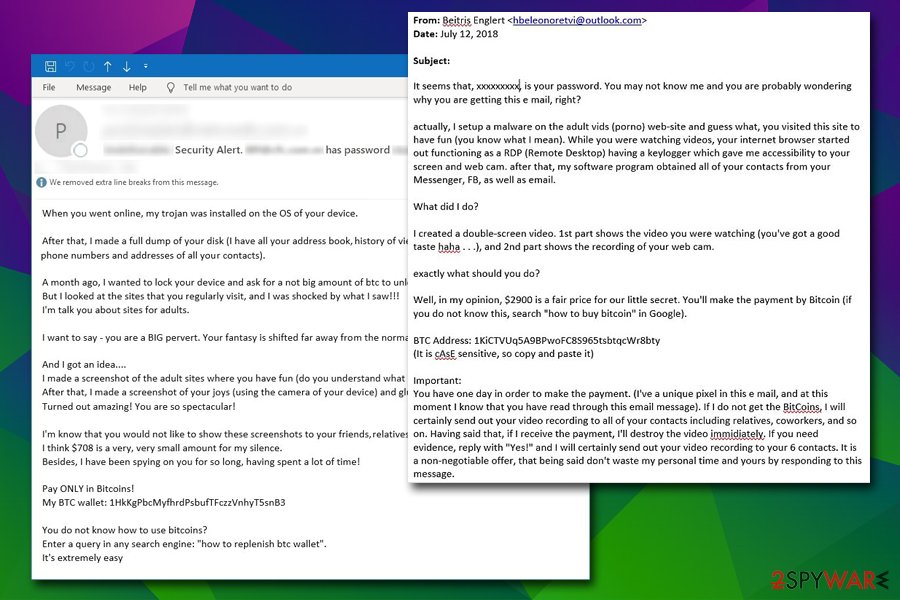
Extortion scam is not a new phenomenon – the first spike of these bogus emails surged back in July 2018.[1] Victims were receiving emails which included their passwords within the subject line, making the scam more believable. However, this information was typically acquired from previous data breaches – something most users are not aware of.
In the N1ghTm4r3 email scam case, no passwords or similar information is provided, however. This is generally cheaper, as the hackers do to have to waste money on buying the information on the Dark Web. The scam email consists of the following body:
Yeah. I know you are a pedophile. Actually I know way more about you than you think. I am a computer scientist (internet security specialist) with affiliation with the Anonymous group. Few months ago you downloaded an application. That application had a special code implanted purposely.
I was observing you for quite some time and what I have collected here is overwhelming. I know about your sexual preferences and your interest in young bodies. I have secured 4 video files clearly showing how you mɑsturbate (captured from your camera) to young teenagers (captured from your internet browser). Glued together is a pretty overwhelming evidence that you are a pedophile.
Because I know you are a wealthy person and that you do care about your reputation, I am willing to gίve you a chance to atone and I will leave you alone. You do know what Bitcoin is, right?
If you do not fund this bitcoin address with 5.000 GBP by next Friday, I will contact your relatives and everybody on your contact lists and show them your pedophilia recordings.
Don’t even think about going to police. If you try, I will immediately know it and I will Ѕeƞd them your mɑsturbation videos, pedo.
The subject lines might be one of the following:[2]
- I know you are a pedophile
- What the **** are you doing, pedophile?
N1ghTm4r3 scam email also uses Unicode characters in order to prevent the detection by built-in scanners from email providers, so the message might not end up in the Spam box as it is usual.
If you received such an email (or a similar one), you should not panic. While you do not have to remove N1ghTm4r3 email straight away, you should be careful if any links or attachments are included inside. If the message consists only of a text, there is nothing to be worried about as long as you do not pay the bad actors.
You should instead contact your local authorities that deal with fraud and forward them the phshing message. After that, can proceed with N1ghTm4r3 email scam removal and change all your passwords just as a precaution measure (make sure you never reuse passwords). Finally, scan your computer with FortectIntego, SpyHunter 5Combo Cleaner, or other reputable security software to ensure no malware is installed – this is especially important if you clicked on links inside the N1ghTm4r3 or other scam email.
The N1ghTm4r3 email scam scheme and psychological manipulation
Sextortion scams became a prevalent form of fraud – Symantec researchers reported that they blocked almost 300 million of such emails in less than six months alone, protecting users from being scammed.[3] However, this is a statistic of just one AV vendor, so the exact number of fake messages like N1ghTm4r3 email scam remains unknown. As evident, the number of such emails is astonishingly high, and it only takes using a botnet for an effective scam distribution.
N1ghTm4r3 email scam begins with a claim of the recipient being a pedophile, right in the Subject line. Nobody would like to be called that, so it immediately sparks curiosity from victims – they want to know what the email is about. Caught off guard, users might straight out panic – pedophilia is illegal and punishable by law, so accusations might bring many users anxiety.
N1ghTm4r3 email author claims that he is a security researcher who works with the Anonymous group. Allegedly, an application that was induced with spyware was downloaded by the victim, so it enabled the alleged “expert” to hijack the camera connected to the device. N1ghTm4r3 then claims that the user was recorded while masturbating to child porn, and the only way to stop these videos from being exposed online is by paying the demanded ransom in Bitcoin.
There is no doubt that no security researchers would use their skills to cause harm to users which, in this case, is money extortion. While most of the users will have nothing to do with illegal porn material, those who do visit porn sites might be afraid of them being redirected to a questionable video or a picture. Without a doubt, X-rated sites are far from secure, but it is highly unlikely that they would redirect to child porn in the first place. Nevertheless, it is always a good idea to employ ad-block to prevent unwanted redirects and pop-ups on adult sites.
Due to the sensitive nature of N1ghTm4r3 email and similar scams, most of the cases remain unreported, with some of the victims paying the requested money. Hence, the scheme became a lucrative business to cybercriminals, and it is highly unlikely to stop any time soon.
While there have been documented cases of bad actors actually hacking into users' cameras, recording them and asking for money, the vast majority of these phishing emails are simply just scams crafted by “script kiddie,” as described by Lukas Lotz, a software developer who analyzed the US campaign.[4]
Phishing emails can be used for money extortion and malware distribution
Possibly 99% of users who use a computer connected to the internet have a dedicated email they use for communication and other reasons. Due to the feature being so widespread, there is no surprise that hackers adapted email function to distribute malware and scam victims – it remains one of the most widespread tools used by cybercriminals for malicious deeds.
While email providers use multiple layers of protection when dealing with bogus messages, some of the use of various new techniques to bypass built-in scanners. Thus, some phishing emails manage to end in the Inbox, which increases the chances of users opening it in the first place.
Therefore, you should be extremely cautious when dealing with emails, even if they look legitimate. Be aware that crooks might use email spoofing technique which allows them a different “From” address to be shown to the victims, making the scam more believable.

You should not pay the demanded money to N1ghTm4r3 email scam authors and instead report it to the authorities
If N1ghTm4r3 email scam is just a single occurrence, you should not be worried too much, as your email address might have been leaked from a previous data breach – these occur relatively often, and there is little you can do to avoid it completely. However, you should always protect your email account with complex passwords and make sure not to reuse them on other sites (according to security researchers at Virginia Tech, 52% of 28.8 million studied users were reusing their passwords on multiple sites).[5]
Before you remove N1ghTm4r3 email scam from your Inbox, make sure you contact relevant authorities and report about the scam attempt. Then, scan your machine with anti-malware software to ensure it is safe and malware-free. Note that, if spyware was indeed planted on your machine, you should also check your online banking history for unauthorized transactions. If any were made, immediately contact your bank and block the access to cybercriminals.
How to prevent from getting spam tools
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Brian Krebs. Sextortion Scam Uses Recipient’s Hacked Passwords. Krebs on Security. Security blog.
- ^ Urban Schrott. Email sextortion scam, claiming victim’s paedophilia links, hits Irish mailboxes. ESET Ireland. Official security blog.
- ^ The Revival and Rise of Email Extortion Scams. Symantec. Threat Intelligence blog.
- ^ Scam and Blackmail from N1GHTM4R3. Lukas Blogging. Official report.
- ^ Chun Wang, Steve T.K. Jan, Hang Hu, Douglas Bossart and Gang Wang. The Next Domino To Fall: Empirical Analysis of User Passwords across Online Services. Virginia Tech. Department of Computer Science.
