Extortion Scam (Free Guide) - updated Sep 2020
Extortion Scam Removal Guide
What is Extortion Scam?
Extortion Scam – a phishing email campaign used for blackmailing users to make them pay ransom in Bitcoin

Extortion Scam is scam email campaign that is used to blackmail victims into paying money. While it is unclear how many separate scammers are involved in the scam, there are hundreds of variants floating around the internet. While the text of the email might differ slightly, the content remains the same.
Typically, bad actors claim that users' machine has been hacked and the malware has been injected into their system. Allegedly, victims were recorded via the web camera while they were visiting porn sites. Extortion Scam then proceeds with a demand of a ransom to be paid into the specified Bitcoin wallet for the attackers not to reveal the leaked photos/videos to victims' relatives and friends.
What makes these type of scams believable is that they usually include a user's password or/and the name in the Subject line of the email, making users panic and believe that the email is genuine. If you encountered extortion scam yourself, never give in to demands of email authors, as they acquired your personal information through dark web hacking portals, and your computer is most likely malware-free.
| Summary | |
| Name | Extortion Scam |
| Goal | Blackmail users into paying money in Bitcoin |
| Claims | Bad actors try to scare users into believing that their system has been hacked and controversial photos/videos taken |
| Versions |
|
| Next steps | Ignore the email, report it to the appropriate authorities and change all your passwords |
| Additional precautions | Scan your machine with security software such as SpyHunter 5Combo Cleaner or Malwarebytes. In case you noticed that your machine is experiencing lag, errors, crashes, or other post-infection issues, we recommend using FortectIntego |
The password or other personal information that is included inside the Extortion Scam provides the feeling of it being real, and many people fall for it. How do crooks know this information? It is relatively simple, and they are not sophisticated hackers who create complex malware to do all the things they claim they do.
Extortion Scam authors simply use information that was leaked in data breaches – they happen every day. Whether it is a large organization, a small online shop or e-commerce website,[1] all the information leaked from these sites end up on the Dark Web.[2] Surprisingly, email addresses and names are relatively cheap, so anybody can buy as much data as they need.
The data sold might be old, so that is why users often see an old password in the Extortion Scam emails. However, criminals are quick to elaborate on the issue, claiming that the alleged malware that is installed on the system is capable of reading all passwords, regardless if it has been changed or not. For example:
Of course you can will change your password, or already made it. But it doesn't matter, my rat software update it every time.
Another reason why Extortion Scam works is that it affects a sensitive topic – the one that people usually want to keep private, and crooks are threatening to disclose these images to users' relatives, friends and social media platforms. Therefore, many users are simply too ashamed and pay the demanded money which can reach $7,000.[3]
In some cases, Extortion Scam email asks users to transfer the money within a certain amount of time (e.g., two days), or all of the leaked photos will be exposed and device locked. Basically, extortionists are trying to use all possible scare tactics in order to make terrified victims pay.
Extortion Scams (sextortion) have been around for many years, but previously mainly focused on extorting nude videos or pictures and then blackmailing them into disclosing those. However, the model of such blackmailing changed completely, and bad actors now focus on receiving a large amount of money.
The FBI reported[4] that in July 2018 alone, the amount of Extortion Scam reports increased by 13,000 comparing it to previous months. Additionally, there are thousands of unreported occurrences, so the scale of the operation is large, and can involve organized crime members.
You should remove Extortion Scam message from your inbox immediately and ignore everything that is written inside the email. Change your passwords and scan your PC with security software. In case an infection was present, eliminate it and then use FortectIntego to fix virus damage and bring your machine to a working state.
Different variants of Extortion Scams do not change the primary goal
Bitcoin blackmail email 2020 scam
In the wake of the coronavirus epidemic, many people were forced to work from home – they either connect to the management programs or used remote connections (RDP, for example) to perform daily tasks. Students and kids were also forced to stay home due to the pandemic.
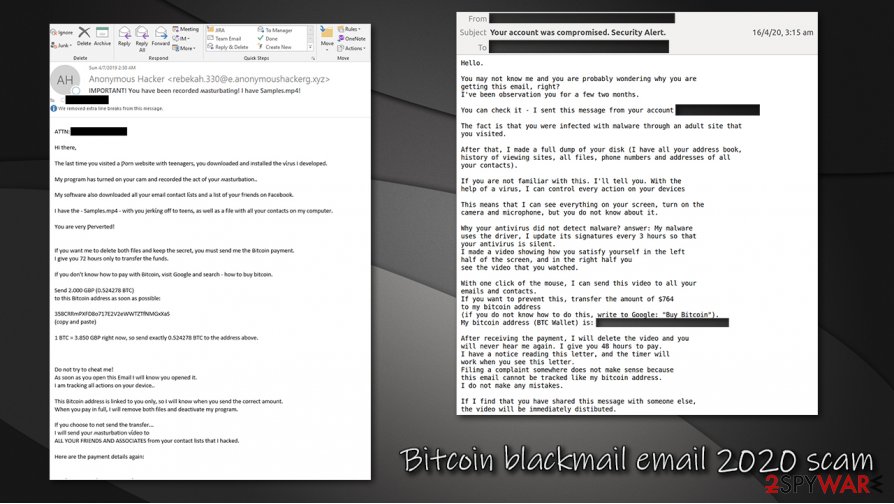
Those who usually went out for a coffee on a daily basis or frequently visited the cinema were also forced to seek entertainment at home. As a result, internet traffic increased dramatically, as Netflix, Facebook, and many other websites saw a significant rise in visitors and new subscriptions. Unfortunately, cybercriminals knew such tendencies very well and saw an opportunity to cash up quickly.
In April, the Federal Trade Commission issued another warning[5] about a new wave of Bitcoin blackmail email 2020 scam. The FTC claimed that the reports spiked significantly, although this number is relatively skewed – most of the people who receive potentially embarrassing messages like Bitcoin blackmail email 2020 do not contact the authorities due to the nature of the message.
Just like with other types of fraud, Bitcoin blackmail email 2020 scam authors attempt to exploit people's minds by using sensitive subjects. The claims of malware infection, hacking, disclosure of the personal password, and sensitive footage leakage are just a few of many traits that might make users give in to the scam and pay up.
You should never pay attention to such unsolicited claims that are stated in the Bitcoin blackmail email 2020 scam, as you will most certainly lose money for nothing. Attackers do not have any information or video footage about you – they got your password from the hacking forums, and this is all just a scheme to extort money from innocent users.
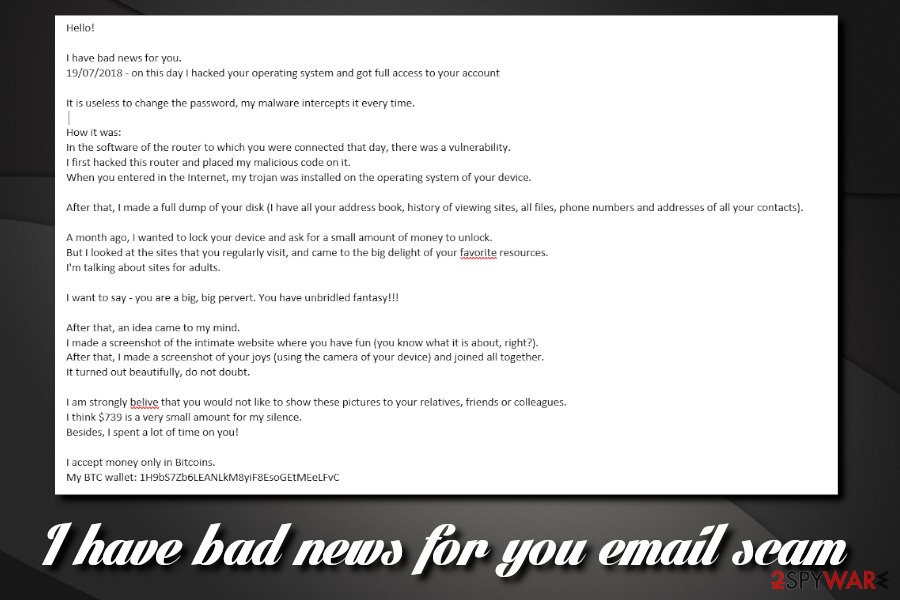
I have bad news for you email scam
This variant of the extortion scam provides a date when victims' computer was allegedly infected with malware via the vulnerability[6] in the router. Cybercriminal then proceeds with explaining how the “infection” compromised the whole operating system of the victim.
According to the scam email, the hacker initially wanted to lock up the device in order to ask for a small amount of money. But instead, he or she checked websites that the victim regularly visits and decided to go with the blackmailing tactic instead.
I have bad news for you Email Scam then asks users to pay $813 into a specified Bitcoin wallet to keep the pictures away from relatives, friends, and colleagues. You should under no circumstances try to contact cybercriminals, as you will end up being scammed.
I am a spyware software developer email scam
As the title says, this scam claims that the originator of the email is a software developer. He or she claims that the victim visited a dangerous website and disclosed the email password. Hacker then explains that malware has been inserted into the operating system, and changing the password will not help.
Bad actor asks for $900 in order to keep the supposedly taken pictures away from relatives and friends. As usual, human emotions and shame feelings are exploited, ensuring that some users will fall for the trick.
I am a spyware software developer email scam is full of red flags when it comes to its legitimacy. Users who understand how viruses work would know that the scenario explained by the email author is not possible, as even malware cannot be transferred to victims' machine via the email unless they open attachments or click on malicious links.
Thus, I am a spyware software developer email is another hoax, trying to pretend that the threat is real.
I'm a programmer who cracked your email scam
This fraudulent message is almost identical to I am a spyware software developer email scam with the subject line “Security Alert. Your account has been hacked” or “Email is compromised. Password must be changed”. It also claims that the email author was a skilled programmer who injected a malicious code onto the operating system. Victims are asked to pay $870 into a specified Bitcoin wallet.
Bad actors are trying to shame the victim by stating the following:
But I was struck by the sites of intimate content that you very often visit. I am in shock of your reach fantasies! Wow! I've never seen anything like this! I did not even know that SUCH content could be so exciting!
The fake email is littered with grammar and spelling mistakes, so it only brings a conclusion that the author is probably not from an English-speaking country. Nevertheless, please remove I'm a programmer who cracked your email scam from your inbox and change all your passwords. Also, scan your PC for malware.
Porn Blackmail virus
Porn Blackmail virus is one of the Extortion Scam variants. The purpose of the scam is the same – to make users pay a ransom of up to $7,000 in Bitcoin. Scammers include the password of the target in the Subject line, which might be terrifying to most of the people who receive such an email in their Inbox.
The difference between Porn Blackmail virus and previous versions is that it claims that the user visited a porn website which was infected with malware. Allegedly, using a Remote Desktop, they managed to gain remote access to the PC, hack the camera, and film the controversial video of the victim.
The crooks promise to delete all the videos they obtained if the payment in Bitcoin would be transferred into a specific wallet. Also, they threaten to expose the video if the ransom is not paid within a day and highly discourage users from going to the police.
As usual, ignore cybercriminals and do not get tricked by Porn Blackmail virus. Scan your PC with anti-malware software just to be sure, and use the safety precautions we advised in this article below.

Phishing emails have been around for a long time: learn how to recognize them
Cybercriminals often use social engineering to trick their victims, so it comes as no surprise that phishing emails are one of the most widely spread scam methods around. In most cases, spam and phishing emails are used to deliver malware payloads, such as ransomware or banking trojans. However, some criminals use a more direct approach, trying to lie about the infection itself which does not actually exist.
Unfortunately, not many users are IT savvy and do not know how viruses work, or anything about their infiltration tactics. For such reasons, there are thousands of people who fall for the trick, cleverly engineered by cybercriminals. Here are some tips by experts on how to avoid scams:
- Do not panic when you receive a threatening email;
- Read through it carefully; even if your password or name is mentioned, it does not mean your PC is infected with malware;
- If you are not sure, scan your computer with comprehensive anti-malware tools;
- Copy and paste first line of the scam message and search for it online – there will be plenty hints that it is a scam;
If you received a scam email, report it to the appropriate bodies in your area and change your passwords.
Get rid of Extortion Scam email without contacting crooks
After receiving a scam message, you should make sure that your system is not compromised. We suggest using FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes (Safe Mode with Networking is the best environment to do so) for Extortion Scam virus removal. If no malware is present on your computer, you should immediately change your passwords on your accounts, and report the incident.
As soon as that is done, you can safely remove Extortion Scam email from your Inbox with no consequences whatsoever. Remember, all the personal information disclosed in the email was acquired from a data breach, so as long as your passwords are updated, you should be safe.
Getting rid of Extortion Scam. Follow these steps
Manual removal using Safe Mode
If you are unsure whether or not your PC is infected with malware, enter Safe Mode with Networking and perform full system scan:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Extortion Scam using System Restore
You can also eliminate the virus with the help of System Restore.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Extortion Scam. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Extortion Scam and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting spam tools
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Olivia Morelli. Magecart strikes again: targets Shopper Approved eCommerce websites. 2-spyware. Cybersecurity News and Articles.
- ^ Paid Content: Here's how much your personal information is selling for on the dark web. Fox News. American news network.
- ^ Jaeson Schultz. Anatomy of a sextortion scam. Talos Intelligence. Security Blog.
- ^ FBI, This Week: Sextortion Reports on the Rise. FBI. Federal Bureau of Investigation.
- ^ Scam emails demand Bitcoin, threaten blackmail. FTC. Federal Trade Commission.
- ^ Thomas Holt. What are software vulnerabilities, and why are there so many of them?. The Conversation. Academic rigour, journalistic flair.







