News-kewafe.com ads (scam) - Free Instructions
News-kewafe.com ads Removal Guide
What is News-kewafe.com ads?
News-kewafe.com shows pop-up ads that might direct you to malicious websites
News-kewafe.com is a malicious website created for the sole purpose of scamming unsuspecting users. Oftentimes people start to notice this web address when they begin seeing random pop-ups popping up out of nowhere – something that isn't triggered by any action or site visits whatsoever. In reality, these bothersome notifications are due to push notifications accepted previously as part of an elaborate fraud plot.
Usually, unsuspecting users end up at the News-kewafe.com scam page when they click on a malicious link from an unreliable website or due to adware-related redirects. They are generally unaware of anything out of the ordinary and think it's just another security verification test being requested from them. Nevertheless, no matter how one stumbles upon this fraudulent site, it pays to remain vigilant with all online activity.
When a user clicks the “Allow” button within the notification prompt, they allow News-kewafe.com to send information through the push notifications feature whenever desired. This activity cannot be done unless if the browser is open and running – however, we want you to know that there is an effective way of getting rid of these irritating pop-ups – we explain everything below.
| Name | News-kewafe.com |
| Type | Push notifications, ads, pop-ups, scam |
| Distribution | The intrusive activity can start at some point after the “Allow” button within the notification prompt is clicked |
| Symptoms | Push notifications show on the desktop at random time intervals. They show fraudulent content and links to potentially dangerous websites |
| Risks | If you click on links provided by the website, you might end up infecting your system with malware/PUPs, disclosing your personal information to cybercriminals, or losing money for useless services |
| Removal | To block the intrusive pop-ups, you need to access your browser's settings section. Also, perform a scan with SpyHunter 5Combo Cleaner anti-virus to check for infections |
| Other tips | Potentially unwanted applications often leave traces within web browsers – cookies, for example, are used for tracking. You should get rid of these leftovers with FortectIntego or employ our manual guide |
How users get scammed
Unsuspecting users are often redirected to fraudulent sites through a malicious script embedded in other websites or when they click on an unsolicited link. This means the redirect is done without warning, making it simpler for scammers to deceive people with several deceptive messages that urge them to allow notifications. Here is one of the examples you might encounter after entering News-kewafe.com website:
Click Allow if you are not a robot
This message gives the false impression of being a basic bot check, which is commonly used by legitimate websites to prevent possible DDoS attacks. Familiarity with this type of request makes people more likely to follow the instructions they have been given. People may also be told their browser is hindering video playback or even asked to provide confirmation of age – all familiar components of an ordinary website security measure.
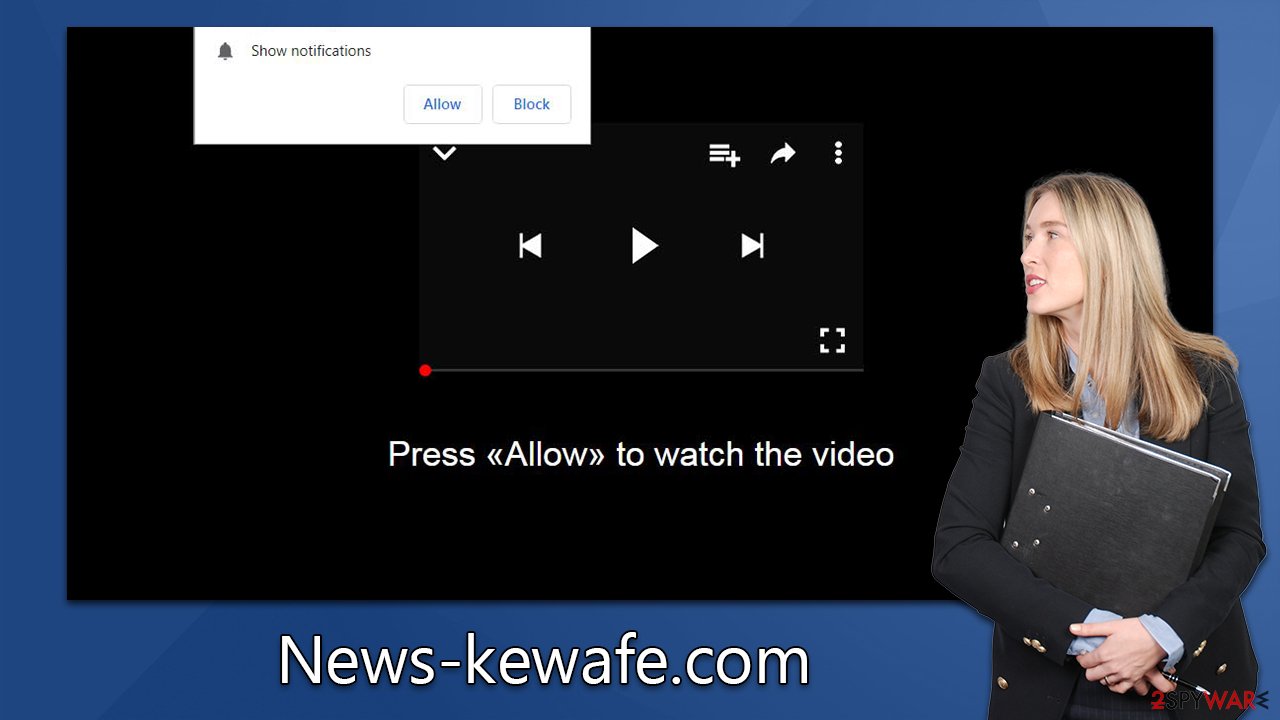
Dangers of enabling notifications from a malicious website
When users grant permission for push notifications, they may receive them at any time while their browser is open. This enables interested parties to display various advertisements, which can generate revenue. However, scammers may use unreliable advertising networks, which can result in poor quality, misleading or malicious ads.
While you may encounter regular ads that do not differ much from those seen online, there is plenty of malicious content that could be shown as well, including:
- Misleading virus infection alerts are designed to deceive users into believing their systems have been infiltrated with malicious software, urging them to utilize the proposed anti-malware. In order to appear authentic, these prompts often imitate logos and notices from established security vendors.
- Get-rich-quick schemes often attempt to lure people with claims of unbelievable returns within a few weeks or days when investing only nominal capital. To add credibility, fraudulent testimonials from local celebrities and fabricated Facebook messages are normally included in the sales pitch.
- Gift card and giveaway scams can appear to be lucrative offer, claiming that you were chosen for an expensive reward from well-known companies like Amazon or Google. However, it is important to remember that these are likely scams created by criminals in order to collect personal information. Avoid engaging with any suspicious offers, as they could potentially put your data at risk.
This is why we recommend avoiding News-kewafe.com ads at all costs – they might trick you into spending money on useless services or provide your personal information to cybercriminals. Instead, follow the steps below to get rid of the annoying activity once and for all.
Check for adware
If you are being rerouted to News-kewafe.com, chances are that adware has been installed in your system. Adware is an annoying kind of software specifically designed to display intrusive advertisements on a user's screen; this way, the developers get paid for each click made on these ads.
From its uncertain distribution to data tracking procedures that are often questionable, this software is not a desirable choice. Its ads can be incredibly intrusive and display deceptive or dangerous material frequently, making it even more difficult to ignore. In some cases, the existence of malicious or unwanted programs may go unnoticed due to various camouflaging techniques employed by developers.
As an example, a malicious app might not show up on the installed program list and hijack existing processes. It could also create scheduled tasks to restart malevolent processes or modify registry settings so that it loads every time the system starts.
We suggest scanning your system with SpyHunter 5Combo Cleaner, Malwarebytes, or any other effective anti-malware program. It can quickly delete all detected threats simultaneously, and you won't have to stress over anything else. Once all malicious programs are removed, rid your browser caches and clear away leftover files – fortunately, FortectIntego can help in this process, as it can automatically detect and remove them for you.
How to remove push notification prompts from your system
Eliminating undesired push notifications is not a complicated process, but many individuals may not be familiar with how to locate and remove them. As the feature has been available for some time and most users do not interact with them, they may not have had the need to remove them. Follow the steps below to prevent unwanted advertisements from appearing on your screen.
Google Chrome (desktop)
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.

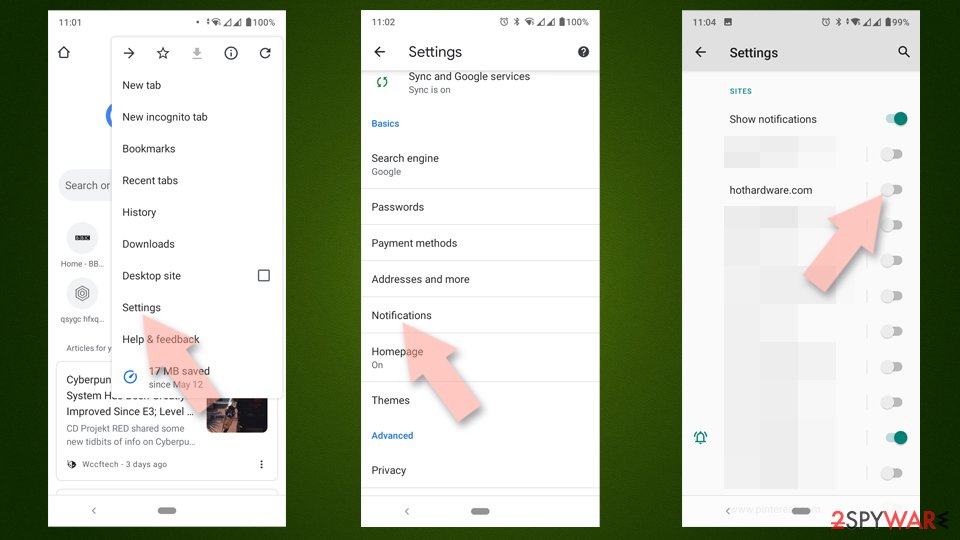
Google Chrome (Android)
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to the Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.

MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.

Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.

Internet Explorer
- Open Internet Explorer, and click on the Gear icon at the top-right of the window.
- Select Internet options and go to the Privacy tab.
- In the Pop-up Blocker section, click on Settings.
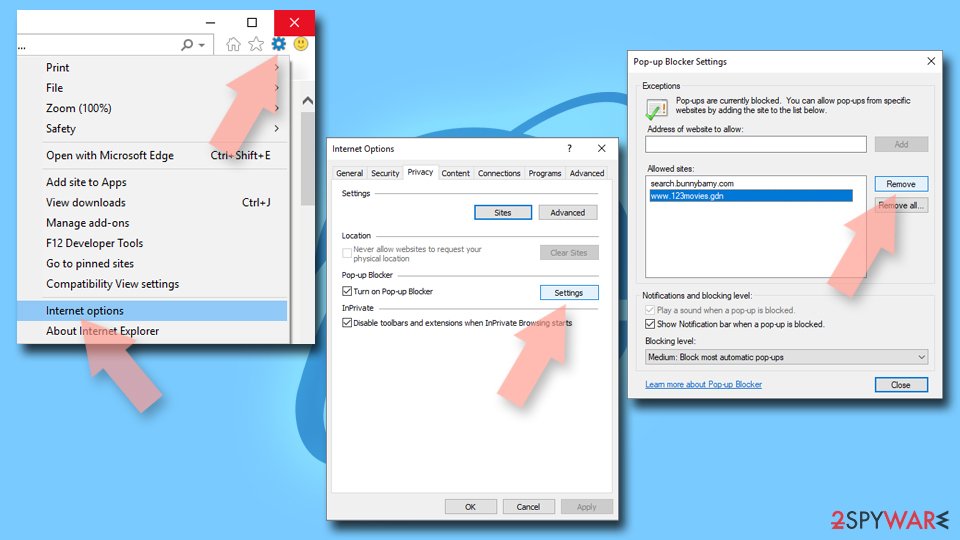
- Locate the web address in question under Allowed sites and pick Remove.
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
