News-tabiva.cc ads (spam) - Free Instructions
News-tabiva.cc ads Removal Guide
What is News-tabiva.cc ads?
News-tabiva.cc was created to make money with pay-per-click advertising
Since Apple first released push notification function in 2009, it opened new doors for people looking to make money online. The main purpose of notifications is to give companies and individuals the ability to inform their customers, readers about the latest news and updates.
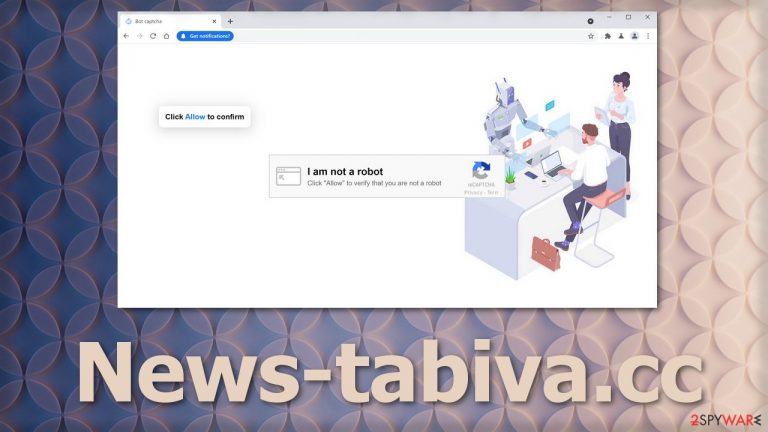
In recent times, abuse of push notifications became a problem, and it does not seem it will go away any time soon. News-tabiva.cc is a fake website, like many others, using social engineering tactics[1] to fool people into allowing push notifications and then spamming them with advertisements.
These ads, if clicked on, generate revenue for developers. The problem is that they are not upfront with users that they will send commercial content. Furthermore, the creators do not filter where the ads will come from, so not only legitimate advertisers will be pushed, but also questionable ones.
There are many issues associated with this. Scammers also advertise; there is no other way for them to reach people. They can create ads that do not look anything out of the ordinary. If they gain users' trust, they can easily manipulate them and lure out sensitive information or suggest downloading tools that look handy, but in reality, they can be potentially unwanted programs[2] or even malware.[3]
| NAME | News-tabiva.cc |
| TYPE | Push notification spam; adware |
| SYMPTOMS | Pop-up ads, banners, and other types of commercial content appearing on the screen, sometimes even when the browser is closed |
| DISTRIBUTION | Redirects from shady websites, deceptive ads, software installations from unofficial sources |
| DANGERS | Ads sent from the website can be created by scammers and lead to dangerous websites where people can be manipulated into providing their personal information or downloading malicious programs |
| ELIMINATION | Removal can be completed in two ways – manually, by going to the browser settings, or by deploying professional security software to scan the system |
| FURTHER STEPS | FortectIntego repair tool should be used after the elimination is complete to fix any remaining damage |
There are many similar websites that look almost exactly the same and serve the same purpose. Some of the examples we already wrote about – Huronews.com, Ndraisineff.online, Spinachtighten.com. It seems that they are very easily reproducible, so if a hundred of them get exposed one day, they stop working, and a hundred other ones go up the next day.
It is rare for a person to find a page like this on his own. Usually, people get redirected to it by an already shady site they were visiting because they clicked on a deceptive ad or a sneaky redirect. When they come on the site, they are asked to confirm that they are not robots.
If a person is rushing or not very tech-savvy, he can fail to notice that this is not a legitimate captcha[4] verification process. A real page will never ask you to grant permission to show notifications to verify you are a human.
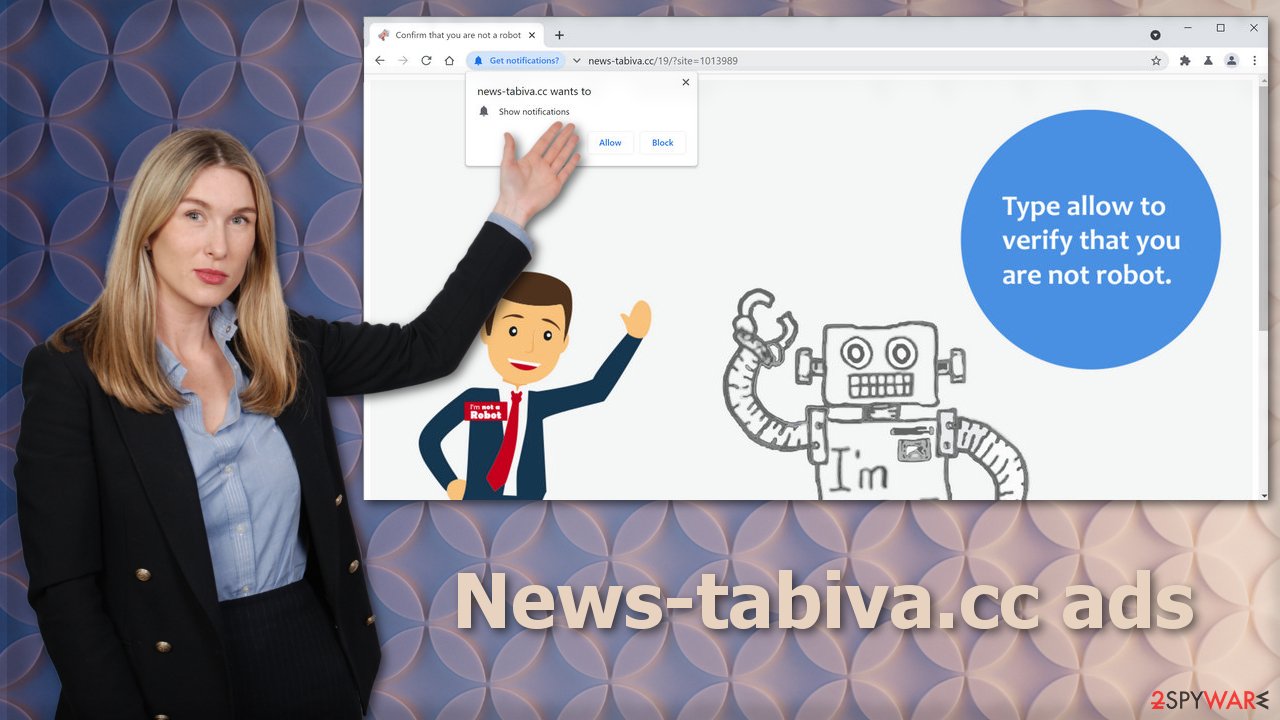
Some of the other messages you might see that try to trick you:
Click Allow to watch the video
Download is ready. Click Allow to download your file
Press Allow to confirm your age
These pages do not have any content to provide, so users do not receive anything after clicking the “Allow” button. All that happens, probably, is users get redirected to another page. Victims start getting spammed with pop-up ads. The frequency in which they appear depends on what settings the creator of News-tabiva.cc has chosen.
Some people might not even notice anything weird, so it is best to go by the rule not to trust everything you see on the internet. Selfish individuals have their ways to fool gullible people by using scare tactics. Among real ads, you might receive those that warn you about system errors, virus threats, or needed updates.
You should never update your software through a random website. Always go to the official source or open the software itself and check if it really needs to be updated, or it is a trick to get you to download a PUP or malware instead of the update.
If you have noticed ads on your desktop or mobile device coming from this website, you should block notifications immediately. The sites you visit through the ads might also be gathering information about your browsing behavior with the help of cookies, so use FortectIntego to delete them automatically. This maintenance program will also clear cache, so you should notice an improvement in performance.
Manual removal method
Google Chrome (desktop):
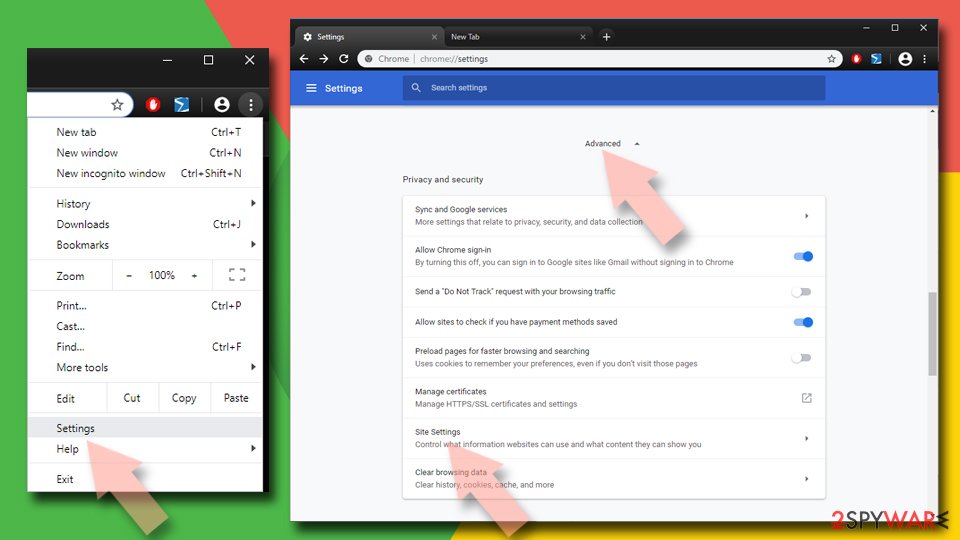
- Open Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate Privacy and security section and pick Site Settings > Notifications.
Safari
- Click on Safari > Preferences…
- Go to Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.

Mozilla Firefox:
- Go to Menu and then select Options.
- Go to Privacy & Security > Notifications > Settings.
- Choose Block after picking this option from the drop-down menu.
- Confirm with Save Changes.

MS Edge (Chromium):
- Go to Menu and pick Settings.
- Select Site permissions.
- Click on Notifications.
- Find the site URL, and click More actions.
- Pick Block.

Android (Google Chrome):
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).
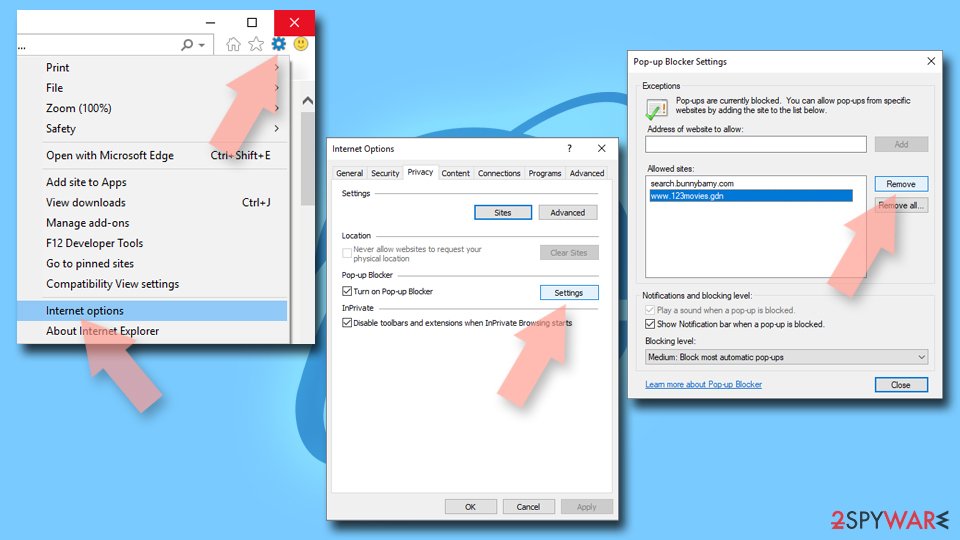
Internet Explorer:
- Open Internet Explorer, and click on the Gear icon at the top-right on the window.
- Select Internet options and go to Privacy tab.
- In the Pop-up Blocker section, click on Settings.
- Locate web address in question under Allowed sites and pick Remove.
Other removal options
If the previous method did not stop the intrusive pop-ups, this might be the work of adware, which belongs to potentially unwanted programs. This app could have gotten into your system because it was disguised as a useful tool that you thought you needed. In reality, the promoted functions of these applications are rarely working, and in turn, they perform tasks in the background without the users' knowledge.
The other possibility is, you might not know about the existence of such a program at all. If you use unofficial sources to download free software, often they use software bundling to monetize you in other ways. People often rush through the installation process because it is boring, and they want to test the software as soon as possible.
But going through all the steps is crucial if you do not want uninvited guests. Always choose the “Advanced” or “Custom” installation methods so nothing would be hidden from you. Read the Terms of Use and Privacy Policy to determine what data will be collected and how it will be used.
The PUPs are sometimes out in the open or hidden in the files you want to download. Go through them all and look for anything suspicious. If you see files that seem totally unrelated to the software you want to get, uncheck the boxes next to them.
The easiest removal method of such programs is by getting professional security software like SpyHunter 5Combo Cleaner or Malwarebytes to perform a scan of your system. They can detect PUAs, malware and eliminate all the files belonging to them. Finding the right program to delete might be complicated if you do not have experience. It can have many different names and icons, so it is not something particular.
If you still want to do this yourself, we have step-by-step instructions for Windows and macOS users:
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
If you are using Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ How to identify and avoid social engineering cyber attacks. Canadian Bankers Association. Fraud Prevention.
- ^ Liam Tung. Google: Unwanted bundled software is way more aggressive than malware. ZDNet. Cybersecurity News.
- ^ What are the different types of Malware?. Comtact. IT Services.
- ^ CAPTCHA. Wikipedia. Free Encyclopedia.
