NMCRYPT ransomware (virus) - Decryption Methods Included
NMCRYPT virus Removal Guide
What is NMCRYPT ransomware?
NMCRYPT crypto-virus is the ransomware that demands to pay almost $7000 ransom in Bitcoins for the alleged file recovery tool
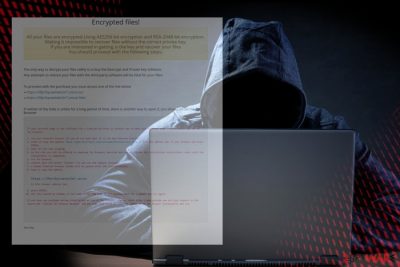
NMCRYPT is a dangerous crypto-ransomware virus[1] that is currently being distributed via unprotected Remote Desktop Services, malicious email attachments, and rogue software updates. Its developers exploit AES-256 and RSA-2048 encryption algorithms to take victim's files hostage. The ransomware is known for targeting video, audio, photos, text, database, spreadsheets, and presentations in particular. Encrypted files get the particular suffix, which is why the virus is also dubbed as .NMCRYPT file extension virus. Upon successful unraveling, the victim is presented with a Recover your files.html ransom note, which demands to pay $6,705.02 ransom in Bitcoins asap.
| NMCRYPT file virus | |
|---|---|
| Classification | Ransomware |
| Danger level | High. Locks personal files and corrupts system's settings. Free decryptor is not available. |
| Symptoms | Personal files inaccessible. File extensions changed to .NMCRYPT. Each folder contains Recover your files.html file |
| Size of redemption | $6705.02 in Bitcoins |
| Encryption applied | AES-256 and RSA-2048 |
| Elimination | The threat can be terminated with the help of anti-malware tools |
| Automatic virus damage removal available. Download FortectIntego and run a full system scan to find and fix any altered or corrupted files | |
NMCRYPT is the second ransomware virus after Vurten demanding a huge ransom in exchange for a decryptor. Typically, the size of the redemption ranges from $200 to $500, does not exceed $2000.[2] Thus, it seems that we're currently dealing with a real gold-digger.
The ransomware virus has been spotted in the wild in the middle of April 2018. Recognized as a Generic.Ransom.XRatLocker.5E892A47, Ransom.Haknata.S1240226, Ransom_AIRACROP.SM, Trojan.Win32.Deshacop.enxprt, and similar detections by reputable anti-virus engines, seems to be targeting English-speaking in particular.
Ransomware researchers have currently analyzed the infection and disagree upon its origin. While some of them claim it to be derived from NMoreira ransomware, the others assert that it's yet another crypto-malware based on HiddenTear open-source ransomware. Anyway, it's a fact that the NMCRYPT virus encrypts files that can not currently be decrypted without paying the ransom.
Once installed, it opens Command Prompt under administrative privileges and runs a script to delete Volume Shadow Copies, which are created by Windows by default. Besides, it disables all previous Windows versions that have been created using the Windows Recovery option. This way, hackers minimize the possibility to unlock files encrypted by ransomware and maximize revenue.
Personal files are locked using AES-256 and RSA-2048 ciphers, which allow hackers to ensure strong-coded encryption. The combination of double-layered encryption makes it practically impossible to crack the code manually. Therefore, hackers ask for $6705.02 redemption to be transferred in Bitcoins using the Tor browser and a Bitcoin wallet to get the unique identification numbers necessary for the decryption.
To prove credibility, cybercriminals ask the victim to select a couple of DOCS, XLS, XML or JPG files that do not exceed 2MB in size and send them to them via http://wikisend.com/ channel.
The victim can find the initial information on the Recover your files.html file, which appears by default on each folder and desktop. It contains the instructions on how to download Tor browser and several links redirecting to a Bitcoin purchase website. The text of the note says:
Encrypted files!
All your files are encrypted.Using AES256-bit encryption and RSA-2048-bit encryption.
Making it impossible to recover files without the correct private key.
If you are interested in getting is the key and recover your files
You should proceed with the following steps.
The only way to decrypt your files safely is to buy the Descrypt and Private Key software.
Any attempts to restore your files with the third-party software will be fatal for your files!
Important use Firefox or Chrome browser
To proceed with the purchase you must access one of the link below
https://lylh3uqyzay3lhrd.onion.to/
https://lylh3uqyzay3lhrd.onion.link/
If neither of the links is online for a long period of time, there is another way to open it, you should install the Tor Browser
If your personal page is not available for a long period there is another way to open your personal page – installation and use of Tor Browser, etc.
If your PC has been attacked by this virus, do not fall for paying the ransom note because it's excessive, but also there's no guarantee that hackers won't leave you without a key. The best way to deal with ransomware is to eliminate them and then try to recover data using third-party recovery tools. Therefore, we would strongly encourage you to remove NMCRYPT ransomware using SpyHunter 5Combo Cleaner, or Malwarebytes.
Don't worry if the automatic removal is blocked by some ransomware components. To bypass the interrupter, you should restart the system to the safe environment and then launch the anti-virus. You can find a guide down below this post.
Hackers use multiple distribution channels to spread ransomware
Ransomware virus is a number one cyber threat of 2018. It does not reside in this position for almost a decade and does not seem to shrink in the near future. The increasing number of attacks can be explained by a variety of intricate distribution strategies that hackers exploit. These are the main ransomware distribution channels distinguished by semvirus.pt[3] currently in use:
- Spam email attachments. DOC, DOCX, PDF, PNG, JPG formats. They usually mimic well-known companies or authorities like IRS, Amazon, eBay, etc., and talk over relevant subjects, such as obligations, debts or parcels.
- Exploit kits. Hackers use specific software packs to attack system vulnerabilities. Exploited vulnerability then serves as a gateway to inject ransomware. Exploits might travel along with software updates like Adobe or Flash.
- Unprotected Remote Desktop services. Crooks often manage to reveal RDP passwords open to the Internet and, therefore, can easily enter the system using sysadmin privileges.
- Fake software updates. Crooks might create a phony browser, Windows, Java, Flash Player, or even browser's font updates, and display them on hacked websites. If an unsuspecting netizen clicks on the Download button, he or she executes a ransomware payload.
Although there are many other ways that ransomware developers might exploit, the four mentioned above are most frequently used. Thus, be careful when browsing the Internet and make sure to keep a reputable anti-virus enabled.
A guide on how to remove NMCRYPT ransomware virus
Do not try to remove the virus manually because it's not possible. The malware runs multiple commands and scripts to alter the core system's settings and root deeply to evade elimination. Besides, it installs a package of related files and keeps running malicious processes.
The only way to execute NMCRYPT removal is to download a professional anti-malware or update the one that is already running on the system. Then launch it let the scanner do its job. In case the virus uses helper objects to block a security tool, follow the guide given below.
Getting rid of NMCRYPT virus. Follow these steps
Important steps to take before you begin malware removal
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). However, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works.
IMPORTANT for those without backups! →
If you attempt to use security or recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them.
Before you proceed with the removal instructions below, you should copy the encrypted files onto a separate medium, such as USB flash drive or SSD, and then disconnect them from your computer. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices.
The instructions below might initially seem overwhelming and complicated, but they are not difficult to understand as long as you follow each step in the appropriate order. This comprehensive free guide will help you to handle the malware removal and data recovery process correctly.
If you have any questions, comments, or are having troubles with following the instructions, please do not hesitate to contact us via the Ask Us section.
IMPORTANT! →
It is vital to eliminate malware infection from the computer fully before starting the data recovery process, otherwise ransomware might re-encrypt retrieved files from backups repeatedly.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from NMCRYPT and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Ransomware Still A Top Cybersecurity Threat, Warns Verizon 2018 Data Breach Investigations Report. ISBuzz News. ndependent resource that provides the best in breaking news for the information security community.
- ^ Maria Korolov. Report: Average ransomware demand now over $1,000. CSO. Security decision-makers.
- ^ Semvirus. Semvirus. Virus and spyware news.


































