Nordteam ransomware (Free Guide) - Recovery Instructions Included
Nordteam virus Removal Guide
What is Nordteam ransomware?
Nordteam ransomware is a dangerous computer virus that may result in personal file loss
Nordteam is a type of malicious software designed for money extortion – ransomware is one of the most dangerous computer threats out there. As soon as it manages to get inside, it infects the systems and begins the preparation for data locking. With the help of a powerful encryption algorithm,[1] all pictures, documents, databases, videos, and other files get appended with four randomly-generated characters.
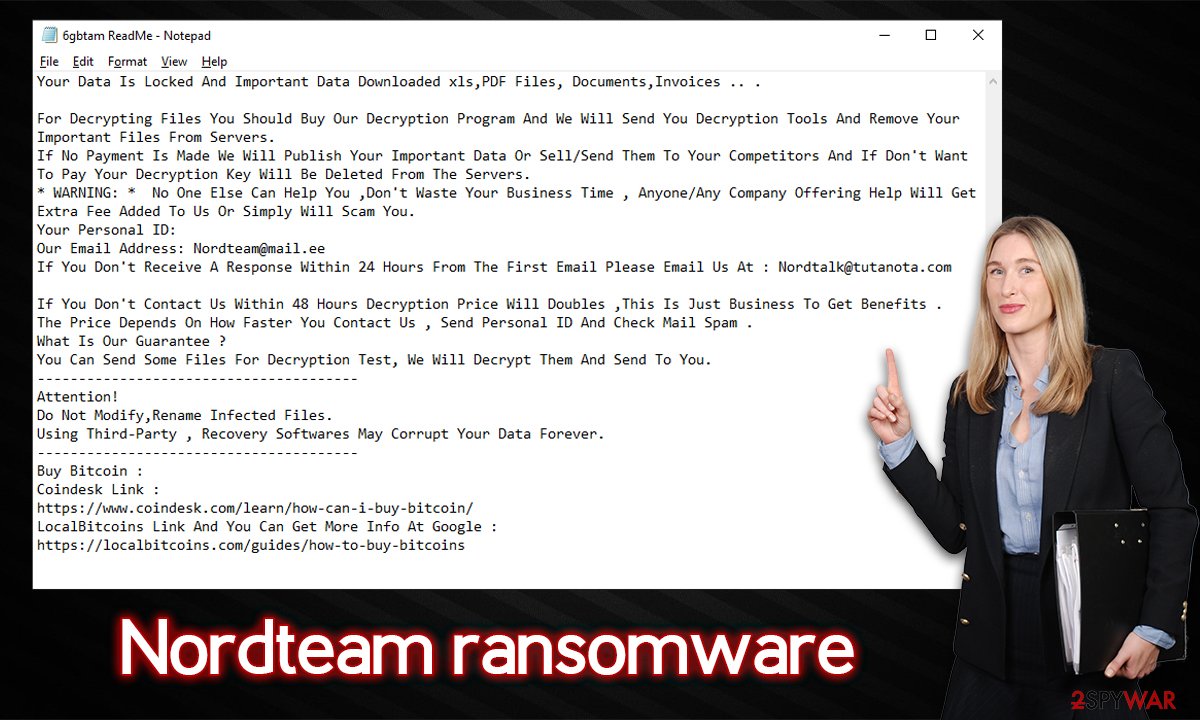
Suchlike data becomes inaccessible to victims immediately; when trying to open files, they would receive an error from Windows, claiming that the file format is not recognized. Those who want to recover access to Nordteam ransomware-encrypted files are asked to pay a ransom within 48 hours, or the price would double. For communication purposes, cybercriminals provide two email addresses – nordteam@mail.ee and nordtalk@tutanota.com.
This information is conveyed in ransom notes delivered right after the encryption is finished, titled ReadMe.hta and [ID]Readme.txt. We do not recommend paying or even contacting hackers, as they might never fulfill their promises. Instead, follow the information below to remove malware from the system and attempt to recover files in alternative ways.
| Name | Nordteam virus |
|---|---|
| Type | Ransomware, file-locking malware |
| malware family | Spora |
| File extension | Four randomly-generated characters, for example, .nsof |
| Ransom note | ReadMe.hta and [ID]Readme.txt |
| Contact | nordteam@mail.ee and nordtalk@tutanota.com |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
More about the Nordteam virus
There are several ways how you could get infected with ransomware; most commonly, cybercriminals employ several distribution methods, although some strains rely on just one (e.g., Djvu variants). Here are a few most common methods by which the virus might be propagated:
- Spam email attachments of hyperlinks
- Software cracks, torrents, repacked installers
- Malicious ads and fake updates
- Software vulnerabilities,[2] etc.
Nordteam belongs to a well-established malware family known as Spora, which has been around for over five years now, with numerous variants released before. It is not the most prevalent ransomware strain, although it seems like the latest variants are targeting companies rather than regular computer users, as this becomes clear when reading the note:
Your Data Is Locked And Important Data Downloaded xls,PDF Files, Documents,Invoices .. .
For Decrypting Files You Should Buy Our Decryption Program And We Will Send You Decryption Tools And Remove Your Important Files From Servers.
If No Payment Is Made We Will Publish Your Important Data Or Sell/Send Them To Your Competitors And If Don't Want To Pay Your Decryption Key Will Be Deleted From The Servers.
* WARNING: * No One Else Can Help You ,Don't Waste Your Business Time , Anyone/Any Company Offering Help Will Get Extra Fee Added To Us Or Simply Will Scam You.
Your Personal ID:
Our Email Address: Nordteam@mail.ee
If You Don't Receive A Response Within 24 Hours From The First Email Please Email Us At : Nordtalk@tutanota.comIf You Don't Contact Us Within 48 Hours Decryption Price Will Doubles ,This Is Just Business To Get Benefits .
The Price Depends On How Faster You Contact Us , Send Personal ID And Check Mail Spam .
What Is Our Guarantee ?
You Can Send Some Files For Decryption Test, We Will Decrypt Them And Send To You.
—————————————
Attention!
Do Not Modify,Rename Infected Files.
Using Third-Party , Recovery Softwares May Corrupt Your Data Forever.
—————————————
Buy Bitcoin :
Coindesk Link :
https://www.coindesk.com/learn/how-can-i-buy-bitcoin/
LocalBitcoins Link And You Can Get More Info At Google :
https://localbitcoins.com/guides/how-to-buy-bitcoins
In addition to locking files, malware authors claim that they might make sensitive stolen information public, which might compromise the company's integrity and cause various damages. This is not a new extortion tactic – it was added by ransomware authors a few years ago, as it makes companies treat ransomware attacks as a data breach, making payments more frequent.
We do not recommend paying the attackers, as they might still publish the stolen information and/or never provide a decryption tool. Instead, advise following the instructions below to remove the Nordteam virus and recover files in alternative ways.
Removal and data recovery
As soon as ransomware finishes data encryption, it immediately connects to a remote server (known as Command and Control). Using it, crooks can send additional commands for malware to execute and sometimes even include additional payloads. Therefore, it is important that all the affected machines would be disconnected from the network and internet. Also, make sure you disconnected from cloud storage[3] services such as OneDrive.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
One of the most important steps is to perform malware removal. Even if the ransomware self-destructs after encrypting your files, malware might still be present and operating in conjunction with other malicious programs. This could lead to further damage and loss of personal information.
To avoid this, we recommend employing SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful anti-malware software to delete all the malicious components from the system at once. If the virus is tampering with this process, access Safe Mode and perform the scan from there:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
![Press F5 to enable Safe Mode with Networking Press F5 to enable Safe Mode with Networking]()
Once malware is removed from the system, you can proceed with the next step – file recovery. If you already have backups of your files, you are free to copy them all over. The matters are much worse if backups were not prepared before the ransomware hit, as restoring files without a decryptor from cybercriminals is almost impossible.
Luckily, specific software specializing in lost data recovery exists – it may help some of the victims of ransomware. Note that it is vital you copy the encrypted files onto another medium prior to proceeding with this step, as data may get corrupted entirely.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Nordteam ransomware Nordteam ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Security experts are known to work on decryption tools for major ransomware strains. In some cases, flaws within the encryption process can be found or criminals' servers seized by the lay authority agencies. In any case, you could look for decryptors on the following pages, although keep in mind it might take a while until there's a working one made.
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Malware attacks are considered a serious felony, and authorities are constantly battling against this criminal activity. By reporting the incident to relevant parties, you can help them catch the culprits. Use the following helpful links:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
Finally, if you experience any computer issues (crashes, shutdowns, BSODs, and similar), ransomware has likely damaged your system files, and they couldn't be restored by security software. Instead of reinstalling the operating system, we recommend employing FortectIntego to replace damaged system components within just a few minutes.
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ What is encryption?. Cloudflare. The Web Performance & Security Company.
- ^ What is a Software Vulnerability?. JFrog. Software Supply Chain.
- ^ Jake Frankenfield. Cloud Storage. Investopedia. Investopedia. Source of financial content on the web.












