Parad1gm ransomware (Recovery Instructions Included) - Virus Removal Guide
Parad1gm virus Removal Guide
What is Parad1gm ransomware?
Parad1gm ransomware – malware that demands to email the developers for receiving information about the ransom price
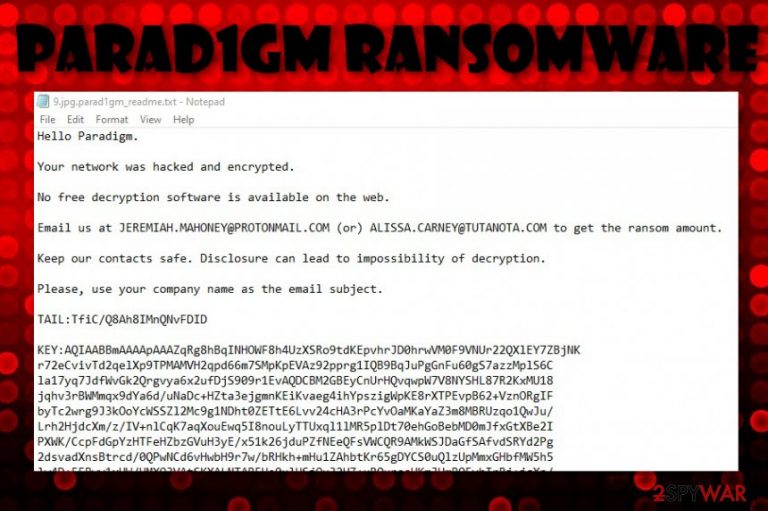
Parad1gm ransomware is a malicious string that comes from DopplePaymer ransomware. The operation principle of this parasite is the same as its siblings – encrypting data and demanding money in exchange for the decryption software. Discovered by a cybersecurity researcher known as GrujaRS,[1] Parad1gm ransomware has emerged at the end of December 2019 and has been targetting English-speaking users. When files are locked with symmetric or asymmetric keys, all of the filenames get the .parad1gm appendix added.
Later on, the ransomware includes a ransom note in each encrypted file. These files end up being renamed with the .parad1gm extension added to the original filename and the _readme.txt title next to it. For example, if you have a file named cat.png, then it would be renamed cat.png.parad1gm_readme.txt. Parad1gm ransomware does not provide any particular ransom demands but encourages to write the crooks via JEREMIAH.MAHONEY@PROTONMAIL.COM or ALISSA.CARNEY@TUTANOTA.COM and discuss all the matters about the price via email.
| Name | Parad1gm ransomware |
|---|---|
| Type | Ransomware/malware |
| Family | This malicious string belongs to the DopplePaymer ransomware family |
| Founder | GrujaRS is a cybersecurity researcher that first announced his findings on the Twitter social platform |
| Appendix | Once all of the files and documents are locked with unique keys, the ransomware virus adds the .parad1gm extension next to each filename |
| Ransom demands | The malware displays a note in each encrypted file that requires contacting the criminals via JEREMIAH.MAHONEY@PROTONMAIL.COM or ALISSA.CARNEY@TUTANOTA.COM email addresses and discussing all the matters about the ransom price |
| Processes | Parad1gm ransomware fills the Windows Task Manager with bogus processes so that it could operate without struggles. The malware can disguise as a legitimate executable and aim to trick people about its appearance |
| Distribution | Ransomware infections are most commonly spread through phishing messages and their malicious attachments. Also, such cyber threats travel through cracked software, malvertising, and vulnerable RDP |
| Removal | You can get rid of the ransomware virus if you employ proper software |
| Fix tip | If your Windows computer system has experienced some type of damage during the cyber attack, you can try repairing things with the help of software such as FortectIntego |
Parad1gm ransomware is a notorious cyber threat that modifies various entries in the Windows Registry in order to place itself on the system. This way the ransomware assures that its module is launched every time when the computer is booted and the encryption process happens successfully. Besides that, the malware might be programmed to evade some type of antimalware detection so that it could operate properly and silently.
Continuously, Parad1gm ransomware alters the Task Manager[2] section too. It places a random executable in this location that also activates the malicious module. If the ransomware virus has taken place in your Windows computer system, you might spot multiple unknown processes running in the Task Manager that is a clear sign of an infection. However, the malware can also disguise as a legitimate executable of some type of program to confuse the victim.
Parad1gm ransomware can also try to harden the decryption and removal process for you. The malware might be capable of damaging the Windows hosts file to prevent you from accessing security-related networks where you might find valuable information on virus removal and file recovery. Additionally, the parasite might be able to delete the Shadow Volume Copies of encrypted data by running PowerShell commands to decrease your chances of successful recovery.
Afterward, Parad1gm ransomware runs the encryption module and starts locking all of the files that are found on the infected Windows computer system. The data can come in any type of format such as image, audio, video, excel, database, powerpoint, notepad, word document, etc. Then, the criminals try to scare their victims by claiming that they hacked their network and safe contacting is required for successfully receiving the decryption tool:
Hello Paradigm.
Your network was hacked and encrypted.
No free decryption software is available on the web.
Email us at JEREMIAH.MAHONEY@PROTONMAIL.COM (or) ALISSA.CARNEY@TUTANOTA.COM to get the ransom amount.
Keep our contacts safe. Disclosure can lead to impossibility of decryption.
Please, use your company name as the email subject.
TAIL:-
KEY:-
Parad1gm virus does not provide any accurate information on the ransom demands and tells the victims to contact them via email to know all the details. However, criminals are most likely to urge some price between $50 and $2000. These people almost always ask for anonymous cryptocurrency transfers as this is a way to stay untracked. Regarding the fact that BTC cryptocurrency is a worldwide used one, crooks are very likely to ask for it.
Parad1gm ransomware stores both encryption and decryption keys on remote servers which are reachable only for the cybercriminals themselves. Every key comes different for every victim and decrypting files by guessing the key is impossible. However, you still should not rush to pay the criminals as you can easily get scammed. Go to the end of this article and try some data recovery methods that are placed there as an alternative.
Furthermore, Parad1gm ransomware can be even more dangerous than just holding your files as hostages. This malicious string can be capable of bringing other malware into your Windows computer system. Ransomware infections make the machine vulnerable to other potential threats and it becomes easy to open backdoors for viruses such as trojans that aim to steal private information, swindle money from bank accounts, damage system software, and corrupt the machine.
The only way to keep yourself safe from all of these risks is to remove Parad1gm ransomware as soon as you spot the infection on your Windows device. For this purpose, you should employ only reliable antimalware software that is capable of detecting and dealing with the cyber threat. According to VirusTotal information,[3] the ransomware virus has been discovered by 45 antivirus engines out of the total 72 programs.
After Parad1gm ransomware removal, you can take a look at the end of this page where you will find some data recovery possibilities. Keep in mind that you have a big chance of getting scammed if you decide to pay the cybercrooks their demanded ransom price. Additionally, if your computer system has experienced any type of damage during the cyber attack, we recommend trying software such as FortectIntego that might be able to repair your device.
The most common spreading ways of ransomware threats
Technology specialists from LesVirus.fr[4] claim that malicious actors often deliver their cyber threats through phishing email messages and their dangerous attachments. The crooks pretend to come from reputable agencies, companies, and institutions in order to create an official look.
Our point would be that you should always carefully manage your email. Do not open any letters that you were not expecting to receive and look suspicious to you. Continuously, always identify the sender, look for grammar mistakes throughout the entire text.
To add, ransomware viruses are also distributed through software cracks that are planted on piracy networks. These types of sources offer to download various products and services for free but they often lack recommended security and can be easily manipulated by various bad actors.
You should get all of your software from reliable developers and official sources, avoid downloading cracks. Also, always make sure that an antivirus product is running on your computer system. This way you will receive warning alerts if something suspicious/malicious is trying to sneak into your device.
Last but not least, cybercriminals know how to manipulate weak RDP[5] configuration. These people search for ports that are protected with weak passwords or include none. Afterward, the hackers can remotely connect to your PC. Remember, always think of complex and strong passwords.
Parad1gm ransomware removal guidelines for victims
If the ransomware virus has hit you and you have been wondering how to remove Parad1gm ransomware from your Windows machine, we are here to help you. First of all, we want to warn you that you should not take any actions of your own towards the elimination process as you might make damaging mistakes. Better, download and install reliable antimalware software that is capable of dealing with the malware safely and effectively.
If you are having some trouble with detecting Parad1gm ransomware or removing the cyber threat, the infection might be running specific commands that are trying to prevent you from spotting or deleting it. To disable malicious processes and activities, you should boot your Windows machine in Safe Mode with Networking or apply the System Restore feature. Both steps are described and displayed at the end of this article.
When you perform the Parad1gm ransomware removal, you should scan your computer system for possible damage with software such as SpyHunter 5Combo Cleaner or Malwarebytes. If these tools find some damaged locations, you can try fixing them with FortectIntego. Continuously, we have provided some data recovery methods at the end of this page that might let you restore at least some files and are definitely a better option than paying the cybercriminals.
Getting rid of Parad1gm virus. Follow these steps
Manual removal using Safe Mode
Diminish malicious changes and processes on your computer system by booting it in Safe Mode with Networking. You can use the below-provided guidelines if you do not know how to do it:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Parad1gm using System Restore
Disable the cyber threat by using the below-provided instructions that will show you how to activate the System Restore feature on your Windows computer:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Parad1gm. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Parad1gm from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Spotting files with the .parad1gm appendix is definitely a sign of a ransomware infection residing on your device. Rather than risking to get scammed by transferring money to the crooks, you can try other data recovery alternatives that we have provided below.
If your files are encrypted by Parad1gm, you can use several methods to restore them:
Employ Data Recovery Pro for file restoring purposes.
If your files have been locked by the ransomware, you might have a chance of restoring your data by employing this type of software.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Parad1gm ransomware;
- Restore them.
Windows Previous Versions feature might help you with data recovery.
This technique might allow you to restore some of the locked components if you have booted your computer in System Restore already.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Using Shadow Explorer can help you with file recovery.
You can try using this tool if your data got encrypted by a ransomware infection. However, this particular method might not work if the ransomware virus managed to destroy Shadow Copies of encrypted data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Cybersecurity specialists are currently working on the official decryptor.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Parad1gm and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ GrujaRS. #DopplePaymer(Paradigm)#Ransomware extension .parad1gm!. Twitter. Social Platform.
- ^ Task Manager. Computer hope. Free computer help since 1998.
- ^ 45 engines detected this file. Virus Total. File Information.
- ^ LesVirus.fr. LesVirus. Security and spyware news.
- ^ Remote Desktop Protocol. Wikipedia. The free encyclopedia.







