PassLock ransomware (Virus Removal Instructions) - Improved Guide
PassLock virus Removal Guide
What is PassLock ransomware?
PassLock ransomware – a cyber virus that alters Windows OS settings while seeking to encrypt files
PassLock ransomware, found by S!Ri,[1] is claimed to be a serious cyber infection that targets English-speaking users who employ Windows computers. The malware starts with altering the Windows Registry and Task Manager sections. When new malicious processes and registry keys are added to those locations, including the main PassLock.exe process, the virus is able to lock up all files that are discovered on the infected device. The encryption process begins when launching the AES-256 cipher and targetting all types of files and documents that are found on the infected Windows machine.
When PassLock ransomware finishes the encryption process, it applies the .encrypted appendix to each filename in order to mark its activity. When all files are renamed, the malware loads a pop-up message that provides the victims with information on what has just happened. The note claims that the ransomware virus has locked up all files and you can only restore them from a backup. However, this ransom message is not a regular ransom-demanding note as it does not provide any information on the fee that needs to be paid for receiving the decryption software.
Crooks are likely to scare the victims and leave them with no choice of file recovery. They claim that the files should be deleted from the infected device as they only take space. Also, hackers state that the victims are free to get rid of the virus now. However, if you are ever provided with any type of ransom demand by PassLock virus, you should not agree to pay any monetary fee as there is a big risk of getting scammed by criminals.
| Name | PassLock ransomware |
|---|---|
| Category | Ransomware/malware |
| Encryption | This malicious cyber infection performs the encryption process on all types of files, including photos, audios, videos, databases, word documents, etc. The malware uses the AES-256 cipher to lock up all the data that is found on the infected Windows computer system. Afterward, the .encrypted appendix gets attached to each filename |
| Related file | When the ransomware virus enters the computer system, it brings the PassLock.exe executable that has been detected as malicious and unsafe by 50 different AV tools, according to VirusTotal |
| Message | PassLock ransomware virus provides a pop-up window that introduces the victims to what had just happened. Users are threatened that there is no way to restore the locked files unless they own backups |
| Distribution | The malware often escapes to different computer systems through p2p networks such as The Pirate Bay, hacked RDP that includes weak configuration, and email spam messages that hold malicious attachments or infectious hyperlinks |
| Removal | If you have been dealing with the cyber threat lately, you should get rid of it ASAP. Employ reliable antimalware software that can help you to terminate the virus properly |
| Fix | If you have discovered any compromised or damaged areas on your Windows device, you can try repairing them with the help of FortectIntego |
| Data recovery | Rather than taking any risks and paying demanded ransoms, you should try other data recovery alternatives that have been included to the end of this article |
According to VirusTotal,[2] PassLock ransomware and has been detected through its main malicious payload – the PassLock.exe executable. 50 different types of antivirus programs have spotted this malware string. Some of the detection names include Win32:Malware-gen, Generic.Ransom.Small.00188FAB, Malware@#3881l2isic0n1, Mal/Generic-S, etc.
Even though PassLock ransomware does not provide any particular ransom demands in the ransom message, you still should be aware of any types of payment requests that cybercriminals might still outline later. Crooks can urge for a ransom price starting anywhere from $50 to $2000 or even more. Also, the sum needs to be transferred in cryptocurrency.
Cryptocurrency payments such as Bitcoin,[3] Ethereum, Monero, Litecoin, and others are often required due to the anonymity if the process that is guaranteed while paying in this type of digital currency. If PassLock ransomware developers would urge for a ransom price, they would also want to ensure their anonymity because of illegitimate monetary requirements.
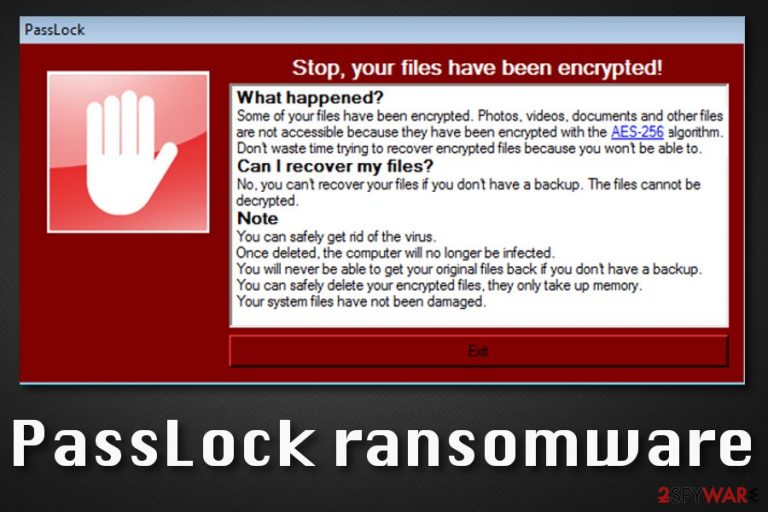
Even though PassLock ransomware does encrypt files and adds the .encrypted extension to the filenames, criminals seem to be more interested in ruing things for the victims by scaring them and not leaving any possibility to get out of this situation. The provided informative message states that there is no way of restoring files if there are no backups available:
PassLock
Stop, your files have been encrypted!
What happened?
Some of your files have been encrypted. Photos, videos, documents and other files
are not accessible because they have been encrypted with the AES-256 algorithm.
Don't waste time trying to recover encrypted files because you won't be able to.
Can I recover my files?
No, you can't recover your files if you don't have a backup. The files cannot be decrypted.
Note
You can safely get rid of the virus.
Once deleted, the computer will no longer be infected.
You will never be able to get your original files back if you don't have a backup.
You can safely delete your encrypted files, they only take up memory.
Your system files have not been damaged.Exit
PassLock ransomware can target any types of files such as videos, audios, photos, powerpoints, word document, excel sheets, etc. When all of these components get locked, criminals often store both encryption and decryption keys on remote servers that are only accessible for the owners themselves.
Some file-encrypting cyber threats seek to harden the data recovery process by eliminating the Shadow Volume Copies of encrypted documents and PassLock ransomware might also not be an exception. It might run specific PowerShell commands and prevent the victims from employing file restoring software that requires safe Shadow Copies.
In addition, PassLock ransomware might be programmed to act as a backdoor for other malware infiltration. The ransomware might be able to disable antivirus protection on the Windows device and let various parasites such as trojans, worms, spyware, bots, or other ransomware virus settle on the vulnerable computer system.
You can avoid this type of consequence by rushing the PassLock ransomware removal. You need to take action against the malware as soon as you see the locked files and spot the criminals' provided message. Beware that using automatic antimalware software is the only proper option that will help you to complete the process safely.
However, if you are having some trouble to remove PassLock ransomware from Windows, you should boot your computer in Safe Mode with Networking to diminish all malicious changes on your devices. Afterward, get rid of the parasite and scan for possible machine damage. If you have spotted any altered areas, try repairing them with software such as FortectIntego.
When PassLock ransomware is gone, it is time to start thinking about your files. Since crooks have left you with no clear possibility of file restoring, there are some alternative techniques that you can try. Go to the end of this page where you will find three different pieces of software that might be capable of recovering some of your files and documents.
Vulnerable RDP configuration is a “game on” for hackers
Technology experts from LesVirus.fr[4] are warning all users to take more care of their passwords that are securing the RDPs. If the person ads a very weak one or none at all, remote hackers can easily misuse them for pushing malware such as ransomware. It is known that cybercriminals are likely to abuse the TCP port 3389.
Also, ransomware viruses are delivered through email spam messages and the attachments that come clipped to them or the hyperlinks that come included in the note's content itself. Developers of the malware pretend to be from reliable healthcare, banking, or shipping organizations and falsely ten to deliver some type of crucial information. A piece of advice would be to stay away from any content that you were not expecting to receive recently.
To continue, malware developers often abuse unsecured downloading sources such as p2p networks, i.e. The Pirate Bay, BitTorrent. These places include cracked games, videos, films, and other types of products. Get all of your software and services only from original developers and trustworthy sources, otherwise, you can accidentally download a virtual parasite to your computer system.
Finally, always take care of automatical protection on every electronical device that you are using for browsing the Internet. This included downloading a reliable and effective antimalware program that is capable of scanning the system, protecting from malware infections, and alerting if something wrong is going on. Of course, you need to keep the tool updated if you want it not to run in various flaws.
Automatical PassLock ransomware removal guidelines
You should take care of the virtual parasite as soon as you find it lurking in the computer system. The first signs of infection are encrypted files and a ransom message that comes provided by cybercriminals. When you get hold of such information, you can start performing PassLock ransomware removal. Our point is that you should take this case seriously and employ only trustworthy antimalware software that would be capable of eliminating the ransomware virus.
Remove PassLock ransomware from all of the infected directories of your Windows device. If you are having any trouble with this process, activate Safe Mode with Networking as shown at the end of this article. Also, try using FortectIntego repair software that might be able to fix all the damage that was done by the cyber threat to your computer system.
When you have wiped out your computer from PassLock ransomware and it is damage-free, you can start thinking about possibilities to recover your files. Below we have provided some restoring software that might be very helpful.
Getting rid of PassLock virus. Follow these steps
Manual removal using Safe Mode
To get rid of malicious changes and deactivate the ransomware infection, turn on Safe Mode with Networking. If you do not know how to opt for this function, take a look at the following instructions.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove PassLock using System Restore
To activate the System Restore feature and diminish all malicious changes on your Windows computer, you should follow the below-provided guidelines.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of PassLock. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove PassLock from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by PassLock, you can use several methods to restore them:
Using Data Recovery Pro might help to save your files.
Try out this piece of software that might help you to repair some of your encrypted components. Make sure to complete each step as required to reach the best results possible.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by PassLock ransomware;
- Restore them.
Windows Previous Versions feature might relate in file restoring.
If you use this piece of software for restoring your files, you might reach great results. However, the technique might not work as required if you have not rebooted your machine in System Restore recently.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Employing Shadow Explorer might allow recovering at least some individual files.
If you have been looking for a tool that would help you to restore your encrypted data, you can try this one. However, keep in mind, that this technique will not work if the ransomware virus has already eliminated or permanently damage the Shadow Volume Copies of your files and documents.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
The official .encrypted files decrypter has not been yet released.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from PassLock and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ S!Ri. #ransomware #wiper PassLock. Twitter. Social platform.
- ^ 50 engines detected this file. VirusTotal. File detections.
- ^ Bitcoin. Wikipedia. The free encyclopedia.
- ^ LesVirus.fr. LesVirus. Security and spyware news.







