Peanuts.pro browser hijacker (virus) - Free Guide
Peanuts.pro browser hijacker Removal Guide
What is Peanuts.pro browser hijacker?
Peanuts.pro changes the browser settings to track user activity and generate revenue
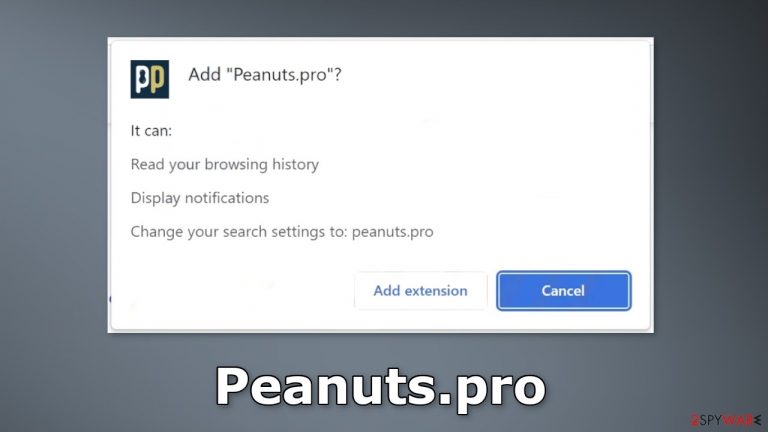
Peanuts.pro is a bogus browser extension that claims to provide users with rewards when they browse. Users are supposed to earn points for every search, site navigation, friend invite, etc. However, it was found that it operates as a browser hijacker instead.
It changes the search engine to peanuts.pro, which should not be trusted. It can also spam users with push notifications. Users can start seeing ads leading to dangerous websites so they can be tricked into providing personal information, downloading PUPs (potentially unwanted programs),[1] and even malware.
Additionally, the application can track users' browsing activity which raises many user privacy and security concerns. There are no clear benefits to having this plugin installed on your device. The reward system is most likely bogus as with many other browser hijackers' promoted functions.
| NAME | Peanuts.pro |
| TYPE | Browser hijacker; potentially unwanted program |
| SYMPTOMS | Changed homepage, search engine, new tab address; redirects to suspicious sites; increased amount of commercial content |
| DISTRIBUTION | Questionable sites, deceptive ads, freeware installations |
| DANGERS | Data gathering about users' browsing activity, links embedded in the search results, and pop-ups can lead to dangerous websites |
| ELIMINATION | You can remove an unwanted extension via browser settings or by scanning your system with anti-malware tools |
| FURTHER STEPS | Use FortectIntego repair tool to fix any remaining damage and optimize the system |
Distribution methods
Most often, people download bogus browser extensions from unsafe sources. We recommend visiting only web pages you know and trust. Do not click on random links and ads. Use official web stores and developer websites instead of Torrent sites or peer-to-peer file-sharing platforms.
You should always do your research no matter what. Read the reviews, look at the ratings, and the number of users. It is best to choose apps that have plenty of positive feedback and thousands of users. However, even then you should be very careful as crooks can post fake reviews. The general rule is – if it is too good to be true, it probably is.
Freeware installations
Many people trust freeware[2] distribution platforms. However, often they include additional programs in the installers without disclosing it clearly. Usually, people do not pay close attention during the installation and do not notice bundled software. To prevent that from happening, you should:
- Always choose the “Custom” or “Advanced” installation methods
- Read the Privacy Policy and Terms of Use
- Inspect the file list and untick the boxes next to any unrelated applications
Bundled software can include PUPs that cause unwanted symptoms. As a result, people can end up with adware,[3] hijackers, crypto miners, and other applications in their machines without knowing. Even though it can get costly, you may save in the long run by installing software from reputable and official sources.
Browser cookies
Web-based applications can use cookies to track users' browsing activity. Cookies are small text files that can store information, like your IP address, geolocation, pages you visit, links you click on, and things you purchase online. Generally, they are used to personalize the user experience but they can also be sold to advertising networks and other third parties to make a profit.
Security experts recommend clearing them regularly. Sometimes, cookies can even be hijacked and used for malicious purposes. You should have a maintenance tool like FortectIntego to take care of this issue. This powerful software can also fix various system errors, corrupted files, and registry issues automatically which is especially useful after a virus infection.
Remove the Peanuts.pro plugin
You can remove browser extensions by going to your browser settings:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Check your system for adware
Eliminating only the extension may not be enough because you might have a PUP installed in your system. If you still experience settings changing, pop-ups, and banners appearing, the best option is to use professional security tools like SpyHunter 5Combo Cleaner or Malwarebytes to make sure you get rid of not only the PUA itself but also all the related files and entries.
The program may not be named the same as the extension, so it can be complicated to identify it. Sometimes developers disguise such apps as system optimizers, antivirus software, or other “handy” tools so users would not suspect them. Anti-malware tools can detect suspicious processes in your machine and eliminate them entirely.
However, if you are sure you know which program is causing the symptoms and manual removal is what you still prefer, we have instructions for Windows and Mac machines:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Chris Hoffman. PUPs Explained: What is a “Potentially Unwanted Program”?. Howtogeek. Technology Magazine.
- ^ Tim Fisher. What Is Freeware?. Lifewire. Internet, Networking and Security.
- ^ Adware. Malwarebytes. Cybersecurity Basics.
