“Pirated Windows Software detected in this Computer” scam (fake) - Free Guide
“Pirated Windows Software detected in this Computer” scam Removal Guide
What is “Pirated Windows Software detected in this Computer” scam?
“Pirated Windows Software detected in this Computer” is a fake alert that threatens users with account bans
“Pirated Windows Software detected in this Computer” is a social engineering[1] attack created by scammers. Once on the page, users are shown multiple pop-up messages claiming that pirated Windows software has been detected on the system and is now blocked from being used. There are plenty of other bogus claims, like virus infections, fake malware scan results, that data is being leaked, etc.
According to the “Pirated Windows Software detected in this Computer” scam message, the only way to remediate the situation is to call “Windows support” via the provided number – this would be the biggest mistake, as users would be tricked into paying money for fake support services, or malware could be installed on their devices.
Undoubtedly, all these claims are fake and should not be trusted. At the same time, we strongly recommend checking the system thoroughly for adware and other infections – we explain how below.
| Name | Pirated Windows Software detected in this Computer |
| Type | Scam, phishing, fraud, fake alert |
| Operation | Mimicks Microsoft website and its attributes: claims that all personal accounts have been locked and Windows blocked. Asks to call a fake support number to remediate the situation |
| Risks | Fake messages usually aim for users to download potentially unwanted or malicious programs, steal their personal information or trick them into subscribing to useless services |
| Removal | You should not interact with the content shown by a scam website. Instead, check your system for adware or malware infections with SpyHunter 5Combo Cleaner security software |
| Other tips | After removal of adware and other PUPs, you should take your time to clean your browser from cookies, and other trackers – FortectIntego can help you with that |
What is the “Pirated Windows Software detected in this Computer” scam?
Online scams are relatively common – they bring good results to scammers due to the techniques used to trick users. While most of these are relatively obvious, some users may not be aware of how scams operate or what the shown messages actually mean. We're here to explain.
In the case of the “Pirated Windows Software detected in this Computer” scam, it is your typical Microsoft scam that uses fake virus scans and then threatens various consequences. It is almost identical to “Pornographic virus alert from Microsoft,” “Trojan Spyware Alert – Error Code: #0x564897,” “Pornographic_Spyware Alert – Error Code #0x268d3(00×7),” and many others.
There are plenty of messages that can be used to frighten users. One of the examples is as follows:
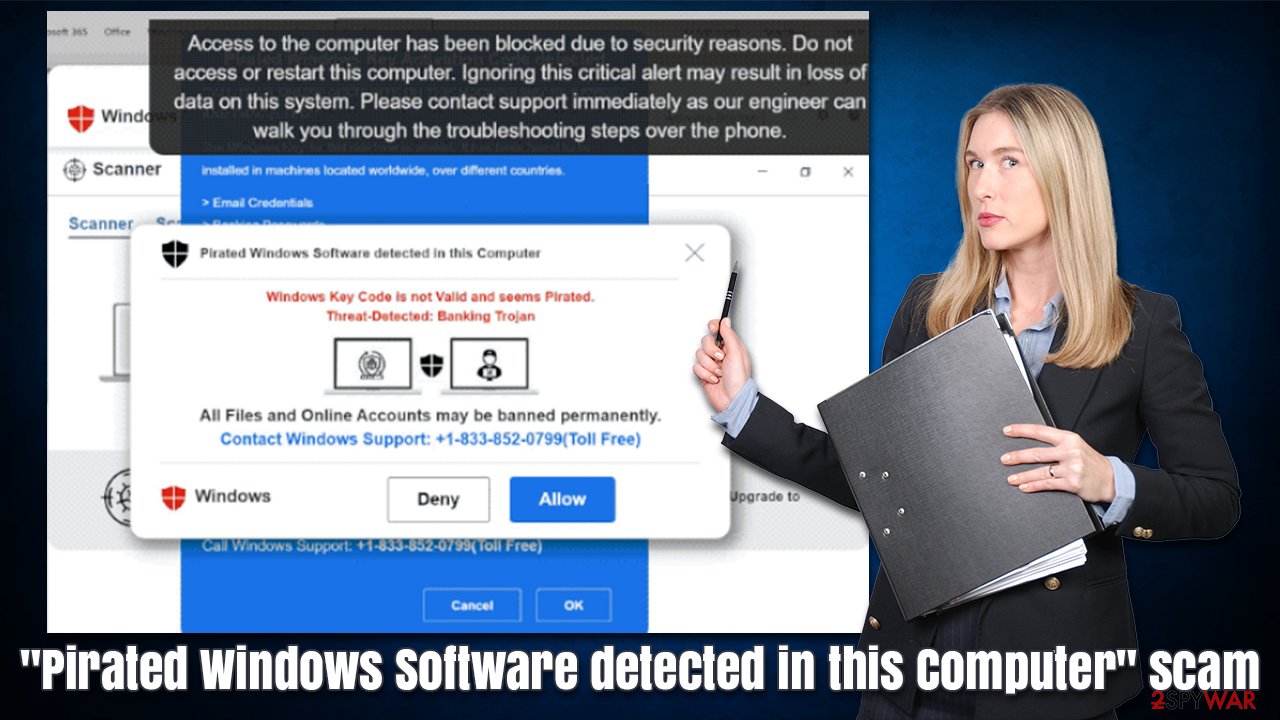
Pirated Windows Software detected in this Computer
Windows Key Code is not Valid and seems Pirated.
Threat-Detected: Banking Trojan
All Files and Online Accounts may be banned permanently.
Contact Windows Support: +1-833-852-0799(TollFree)
Users are bombarded with tons of fake information that is meant to frighten them and make them call the provided number. You should never do that, and instead, close down the page showing the scam immediately.
The “Pirated Windows Software detected in this Computer” scam can be hosted by numerous websites, for example, jpakdjd.tk. When dealing with suspicious messages, you should check the URL – the site implies the message is coming from Microsoft, yet the web address has nothing to do with it. It is one of the easiest and most effective ways of recognizing an online scam. Also, Microsoft never provides contact information in its legitimate messages.
Is my system in danger?
There are plenty of fake messages that malicious websites show to users, and when it comes to the “Pirated Windows Software detected in this Computer” scam, they may be bombarded with several pop-up windows or even taken into the full-screen mode to dramatize the situation even more.
Due to these unusual circumstances, many users may assume that there's actually something bad happened to their computers. Luckily, as long as the scam content is not interacted with, there is no imminent danger to visitors or their computers. In other words, all the claims about blocked accounts and pirated software are fake – this message is shown to every person who ends up on one of the malicious websites that propagate the scam.
While everything said on the scam site is fake, you should not completely dismiss the possibility of the adware infection, as it is one of the main reasons why users end up on phishing websites in the first place. Besides, cleaning the system if anything was installed from the site or during the call with crooks is extremely important.
Remediation steps
Calls to scammers can be particularly damaging, as they usually proceed to convince victims that their systems are extremely damaged, demand remote access, and may even plant malware on healthy computers. If you have called scammers and paid money for their fake services, contact your bank and explain what happened, the money might be reinstated. Also, if you have provided your personal details, expect scammers to contact you again via email or phone.
Here are a few tips on how to deal with the immediate scam message:
- If you were put into the full-screen mode, try pressing F11 to exit it
- If you are unable to close down the tab, call up the Task Manager (Ctrl + Shift + Esc), and shut down your browser.
You should be relatively secure if you have not interacted with any of the promoted “Pirated Windows Software detected in this Computer” scam site's components. We strongly recommend you employ SpyHunter 5Combo Cleaner or Malwarebytes security software to check the system for underlying infections that might not be initially visible to you. For those who installed software, this step is particularly important, as malware could be running on their systems already.
We also recommend clearing browser caches after a full system scan with anti-malware. Some cached files, along with cookies,[2] may remain on the device and cause ads and redirect to the scam sites showing scams once again. Likewise, deleting browser caches from time to time is recommended as a security measure against dangerous session hijacking[3] attacks.
You can quickly and easily clear browser caches and repair damaged system files (if such damage has occurred due to one reason or another) with the FortectIntego repair and maintenance tool. If you would rather do this manually, you should proceed with the following instructions:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
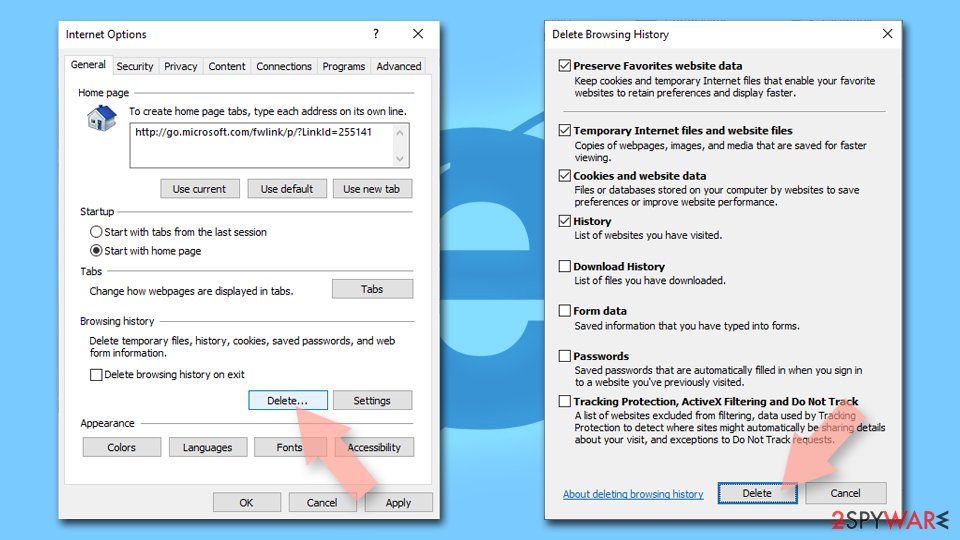
Internet Explorer
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
![Clear temporary files from Internet Explorer Clear temporary files from Internet Explorer]()
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Social Engineering. Imperva. Application and data security.
- ^ What are cookies? | Cookies definition. Cloudflare. The Web Performance & Security Company.
- ^ Allie Johnson. Session hijacking: What is a session hijacking and how does it work?. Norton. Security research blog.