Prorateer.com browser hijacker (virus) - Free Instructions
Prorateer.com browser hijacker Removal Guide
What is Prorateer.com browser hijacker?
Prorateer.com completely changes the user experience by messing up the browser settings

Prorateer.com is one of the thousands of browser hijackers that are created to track users' browsing activity and generate revenue with pay-per-click advertising.[1] It changes the main settings, like the homepage, new tab address, and search engine to force users to perform searches through its websites.
Because the changes happen rather quickly and unexpectedly, many think that they have been infected with a virus. Although browser hijackers are not that dangerous in themselves, they can lead to more serious problems. The developers of such applications do not care about user privacy or security.
Browser extensions can take over all aspects of your browser and change what you see. You might receive inaccurate search results that lead to misinformation or dangerous pages where you could be tricked into providing your personal information or downloading PUPs and malware.[2] This could even lead to financial losses or identity theft.[3]
| NAME | Prorateer.com |
| TYPE | Browser hijacker, potentially unwanted program |
| SYMPTOMS | Changed browser settings, like the homepage, new tab address, and search engine |
| DISTRIBUTION | Shady websites, deceptive ads, redirects, bundled software |
| DANGERS | Search results can spread misinformation or lead to dangerous websites where users can give away their personal information and suffer from monetary losses or download PUPs and malware |
| ELIMINATION | Remove browser extensions via the settings; scan your machine for PUAs |
| FURTHER STEPS | Use FortectIntego to get rid of any remaining damage and optimize the machine |
Browser plugin distribution techniques
Usually, the appearance of such extensions in the machine is the users' own fault. There is a common misconception among some people that the Internet is a completely safe space and viruses are a thing of the past. People often ignore security expert tips on how to keep yourself safe online and that later leads to problems like these.
So where can you find browser add-ons that hijack users' browsers? The answer is everywhere. That is why it is important to read everything you are given and not rush to click the buttons. We say that people should use only official web stores to get applications, but even they are not free from hijackers.
Most often developers use shady websites, deceptive ads to redirect users to their promotional sites, which then redirect to the chrome web store for example. Having an extension on that store is legitimate and trustworthy, but as we said, you should still read the reviews and see how many users it has. Look at the description and see if it looks true. Sometimes creators use big company names (for example “we partnered with Google to provide you with…”) to create even more trust and desirability.
Another very popular method is spreading software that can perform the changes. These are called potentially unwanted programs.[4] They also can come disguised as handy tools, so users would want to download them. Another way is to have them distributed as bundled software on unofficial freeware[5] sites.
The owners of such websites still need to make money so they include additional programs in the installers without disclosing it in the hopes that most users will not notice them. Unfortunately, that is exactly what happens most of the time, and when they get into the system, they start various processes in the background that can affect the PC.
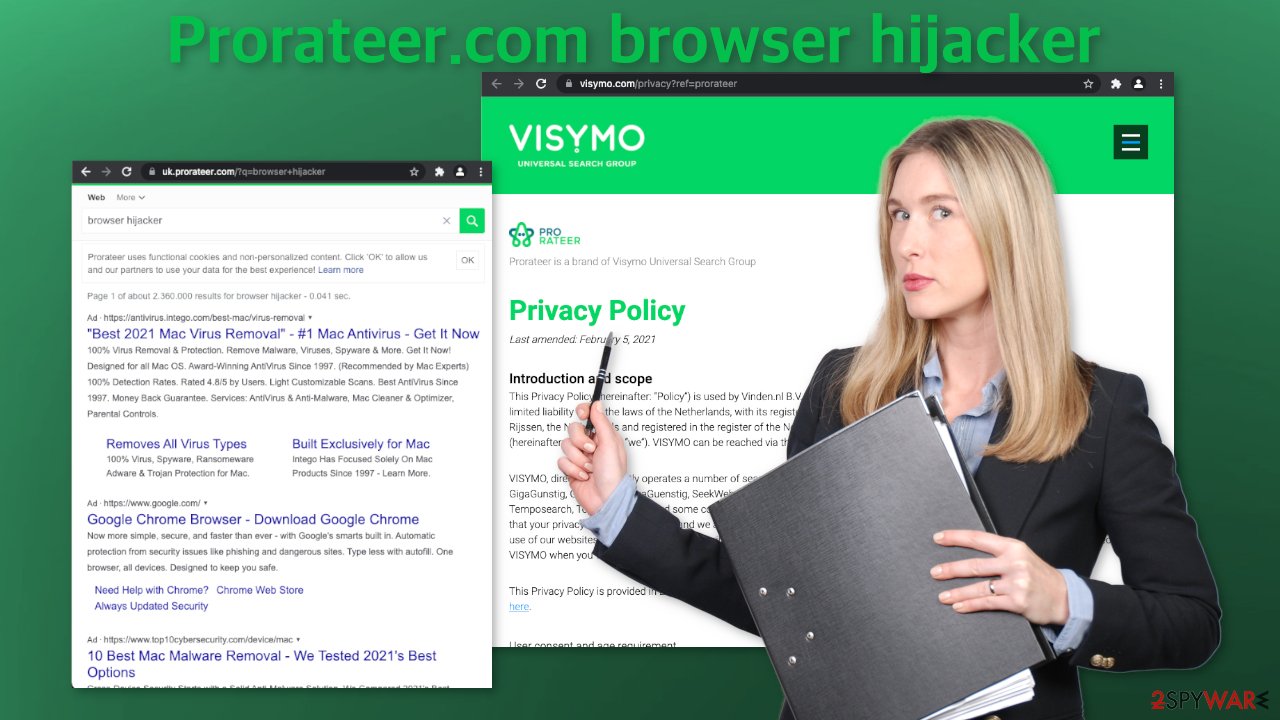
This particular extension sets uk.prorateer.com as the homepage (your URL could differ depending on your location) and adds its own search engine. That is unusual for a browser hijacker as many of them implement already existing ones just to make them functional and serve their purpose. When you type something in the search box and press Enter, a lot of promotional links pop up and it is hard to see how that would be convenient for anyone.
Go to your browser settings
First, let's try to remove the extension, and see if that helps. You can do it via browser settings:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Internet Explorer:
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
Scan your machine with professional security software
If you tried the first removal method, but it did not help and the settings changed back again, this is definitely a sign of a PUA hiding in your system. In that case, the application will keep messing up your browser until you completely remove it from your PC. Identifying the program responsible for hijacking your browser might be difficult if you have never done this before.
The program could be disguised as antivirus, video, or image editing software. If you do not want to risk deleting the wrong files, we suggest using SpyHunter 5Combo Cleaner or Malwarebytes professional security tools that will scan your machine, eliminate it, and prevent such infections in the future by giving you a warning before a PUP can make any changes.
If manual removal is what you still prefer, we have instructions for Windows and Mac machines:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Now that your machine is clear from intruders, you should get rid of all the data that was collected about you, while it was in your machine. For this, you need a different tool – FortectIntego, which is a multi-purpose maintenance software. It will fully clear your browsers from cookies and cache, which will result in better performance of your machine. Besides that, it can be useful in fixing various more complicated system errors that are caused by corrupted files, registry issues, etc.
How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ What Is PPC? Learn the Basics of Pay-Per-Click (PPC) Marketing. WordStream. Advertising Solutions.
- ^ What Is Malware?. Cisco. Security Advice.
- ^ Ben Luthi. What Is Identity Theft?. Experian. Fraud Prevention.
- ^ Wendy Zamora. What is a PUP? – How to avoid potentially unwanted programs. Malwarebytes. Tips, Tricks and How Tos.
- ^ Freeware. Wikipedia. The free encyclopedia.
