ProstoStealer (Free Guide) - Removal Instructions
ProstoStealer Removal Guide
What is ProstoStealer?
ProstoStealer is the trojan promoted online as a tool for information stealing and system hacking purposes
ProstoStealer malware can silently infiltrate machine and evade detection, run in the background for a while until any symptoms are noticed. These facts make the malware more dangerous since it operates and is difficult to detect even with AV tools. Fortunately, it is not a widely used threat, so potential hackers are not abusing these functions. It can create significant damage still and wreck targeted devices. Users encountering any symptoms like application malfunctions, CPU usage, software failure, and significant system crashes should take the infection possibility into consideration and check the system immediately, so trojan can get terminated.
| Name | ProstoStealer |
|---|---|
| Type | Trojan/ Info-stealer malware |
| Purposes | Exploiting the machine to steal valuable information like logins, credentials, passwords, or direct files. All the details get stored on C&C[2] server controlled by hackers and possibly later used for scams or fraudulent transactions, purchases |
| Danger | These threats can be set to work as any criminal wants, so it may act as a backdoor for ransomware or steal valuable information, cryptocurrency wallet funds |
| Distribution | Hacked websites, malicious files added to emails, malware scripts from other internet sources or even p2p service packages |
| Elimination | ProstoStealer removal can be difficult when the program runs for a while, but relying on anti-malware tools can be the best solution because this way your device is fully checked and a trojan or other malware can be found and deleted completely |
| Repair | The system gets affected significantly when the trojan or other more powerful malware infects the machine. Various background processes and changes that trojan makes in system folders trigger the damage, so check the machine using FortectIntego or a PC repair tool, so all the affected or corrupted files get fixed |
ProstoStealer is the malware that mainly focuses on stealing information and infecting computers using other malware. This program may be the initial infection, but the main intruder gets installed later on. No matter what functions get set as the primary, this trojan can damage the machine significantly.
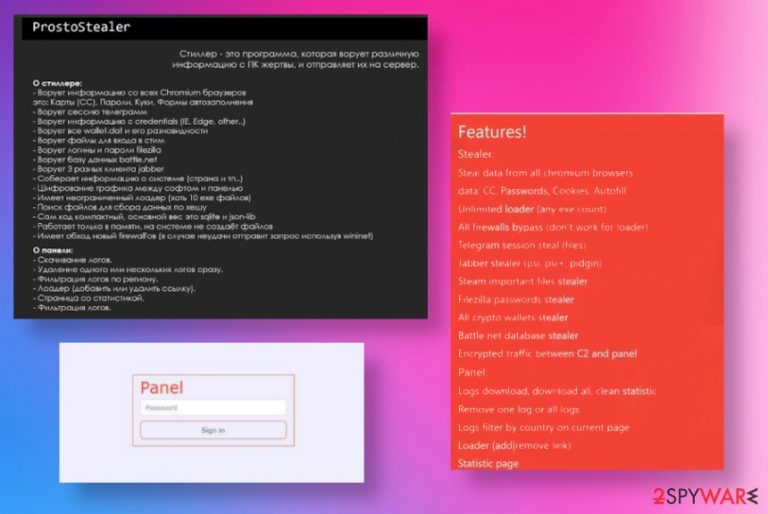
ProstoStealer can steal information from Chromium-based browsers and cookies, autofill information, passwords, saved credit card and other sensitive details can be sent to a remote server that hackers control. There are tons of applications like Telegram, Jabber, Steam, and other sites, cryptocurrency wallets, platforms, social media that can be accessed for such data exfiltration.
ProstoStealer creators, in this case, launchers can infect machines with ransomware and other malware to control more parts of the system, not only steal credentials. This stealer targets stored passwords, cookies, and look for valuable data that can be sent to Command & Control servers of criminals. Such information can help make fraudulent transactions, blackmail people directly, or perform secondary scams.
ProstoStealer malware victims can suffer financial or data losses, experience damage to their devices. Malware controllers can infect computers or even hack accounts on social media, emails. Stolen credentials and login information can lead to serious privacy issues and identity theft. Trojans like this can create serious problems with privacy and machines. Some of the virus damage can be unrepairable. 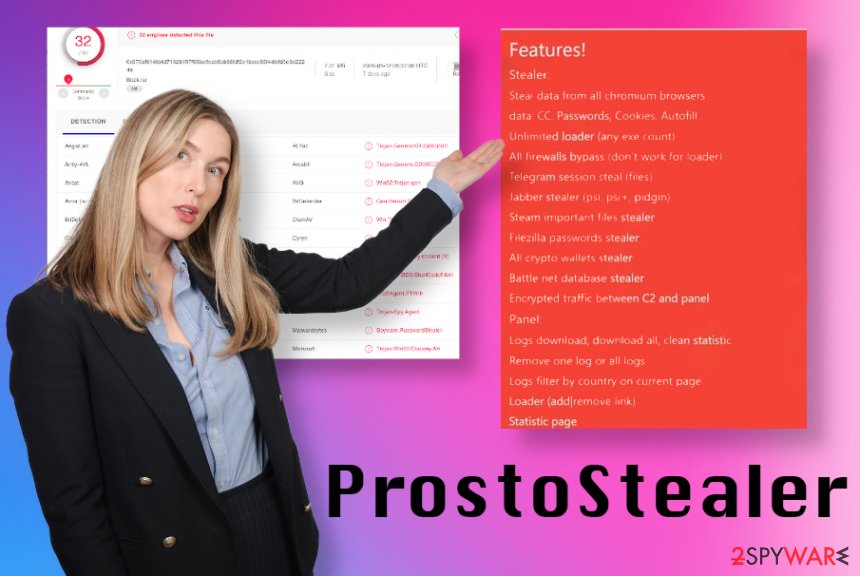
- steal browser-based data;
- execute any commands;
- bypass firewall;
- steal files from applications like Telegram or Steam;
- gather details from cryptocurrency wallet platforms and applications;
- download and run any malware;
- delete data or programs.
You need to think about ProstoStealer removal as soon as you notice any issues with the system or experience sudden losses of some files, or even cryptocurrency wallet funds. This malware type is silent and can even evade detection, but the rate of some sample files[3] shows that anti-malware tools can find this intruder and delete it from the system.
To remove ProstoStealer properly, you need to choose the reliable antivirus detection engine-based program and run a check on the machine. It is extremely important to run a full system scan, so all the parts of this or other threats get found and terminated.
Remember that ProstoStealer malware also runs other files and programs on the system. To do that freely and uninterrupted, trojan relies on changing particular settings and affecting files in the system, like registry or startup. You need to repair that damage if you want to use the machine normally again. File repair programs, PC optimizers like FortectIntego should help you. In such cases, manual interference could create additional issues with startup and other programs, so it is not recommended to alter registry entries yourself. 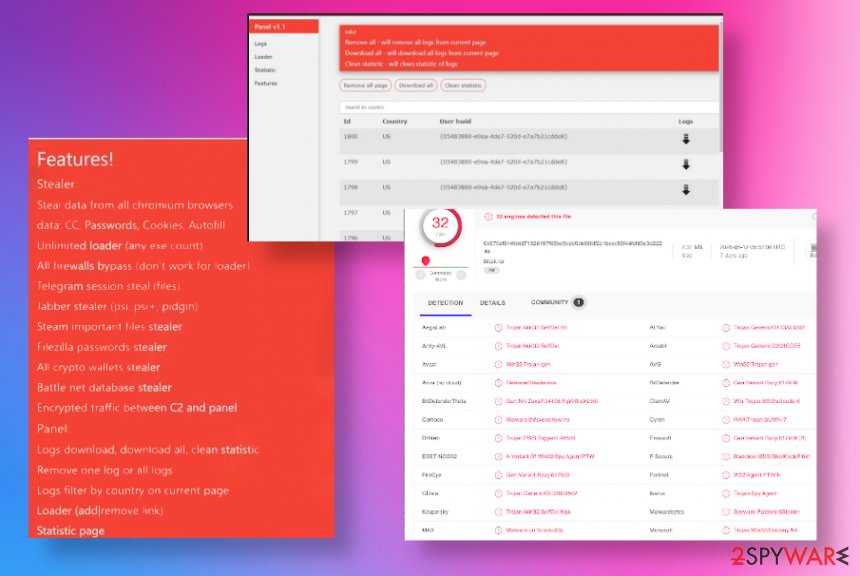
Spam email campaigns and hacked sites spread files with malicious scripts
The most common way to attract such malware like trojans is while surfing on insecure or even malicious sites. Downloading channels, fake software updates, and software cracks can also lead to the infiltration of malware. Websites that resemble official pages or directly copies the interface of some software providers can have malicious scripts running, so interaction, some clicks on the questionable material can trigger a direct drop of the malware payload.
Tha shadiest method that allows malware on the system involves spam email campaigns and notifications stating about financial data, important messages while including malicious files and links. Infectious hyperlinks to malware dropping pages or attachments in the form of MS documents. These files include malicious macro functionalities, so when the user opens a downloaded file and enables the additional content scripts get literally installed on the system without any permissions needed.
The infection can be avoided if you avoid irrelevant and suspicious emails and delete received notifications with file attachments, links, or questionable subject lines. Stay away from shady software download sites and avoid any other source besides official providers and app developers.
ProstoStealer malware termination requires adequate tools for PC protection
Since ProstoStealer virus can be set to perform any functions from the list on promotional pages it can cause damage pretty quickly. Unfortunately, it is not easy to notice the infection in the first place, especially, when the main processes can be launched in the background alone.
ProstoStealer removal has some additional steps that you should take to achieve the best results. The first one is choosing a proper anti-malware tool that can detect the malware and run the system check fully on the affected computer. Once that is done and you have chosen something like SpyHunter 5Combo Cleaner or Malwarebytes, you should reboot the system in a Safe Mode with Networking.
When you remove ProstoStealer using these tips, you can run the AV tool and properly check for malware around the operating system without the interruption. Then the only thing left to do is allow the tool to fully clear those intruders and double-check before repairing system file issues with FortectIntego.
Getting rid of ProstoStealer. Follow these steps
Manual removal using Safe Mode
The Safe Mode with Networking allows the user to run AV tools and remove ProstoStealer without interuption
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove ProstoStealer using System Restore
System restore can act as a malware elimination process because this feature can recover machine in a previous state when ProstoStealer malware was not present
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of ProstoStealer. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from ProstoStealer and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting trojans
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ You are here: Home / News / Crypto Wallet Stealer via Telegram: Masad Stealer Trojan for sale Crypto Wallet Stealer via Telegram: Masad Stealer Trojan for sale. Weplaycoins. Crypto news.
- ^ command-and-control server (C&C server). Techtarget. Search security.
- ^ Malware sample detection rate. VirusTotal. Online malware scanner.







