Rabel ransomware (Tutorial) - Recovery Instructions Included
Rabel virus Removal Guide
What is Rabel ransomware?
Rabel ransomware is a typical file-encrypting malware that demands ransom from its victims
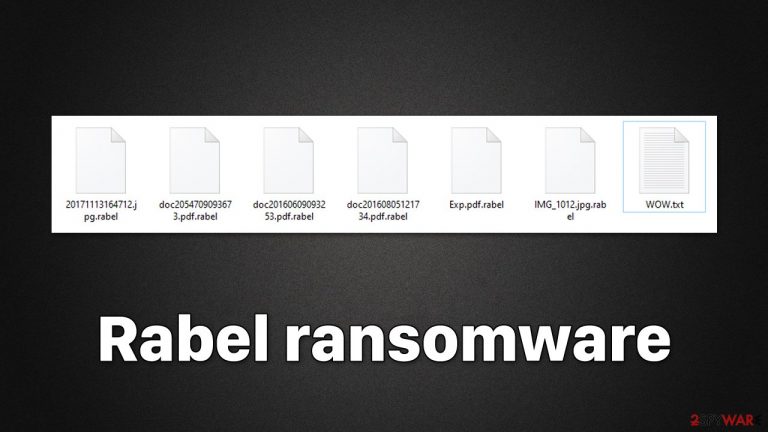
Rabel is a type of Windows computer virus developed by cybercriminals to misappropriate victims' funds via bitcoin digital currency. The principle of malware is rather simple: upon entering the computer using various deceptive techniques (spam emails, torrents, repacked software, malicious ads, etc.), it immediately looks for personal files, such as pictures or documents, to encrypt. With the help of a strong encryption algorithm,[1] the virus encrypts all non-system files located on all connected storage devices, which attaches an appendix .rabel to each of them.
Suchlike data can no longer be accessed by victims – this is when many people start to panic. While it is true that files are not corrupted but rather locked behind a unique encryption key, it is also true that the key is held on cybercriminals' servers, accessible only to them. Using this ploy, hackers can demand a ransom for the return of users' files, resulting in them profiting financially.
The information about what has happened to users' files can be found on a ransom note WOW.txt, which is dropped soon after the data encryption is finished. It also contains contact details and other useful info that could make the payment go through smoothly.
However, we do not recommend communicating with the attackers, as they may never fulfill their promises, and you may get scammed. Instead, we recommend you follow the guide below on how to deal with Rabel ransomware infection and how to attempt to restore files without paying the attackers.
| Name | Rabel ransomware |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| File extension | .rabel |
| Ransom note | WOW.txt |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| removal | Perform a full system scan with SpyHunter 5Combo Cleaner or another reputable security software |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
How ransomware spreads
For years, spam email campaigns have been one of the most successful ways to distribute malware. However, because users are now constantly reminded not to open attachments from inside email spam, this tactic has become much less effective as more users simply delete unsolicited emails without opening them. Likewise, security scanners employed by email providers have become much more effective, resulting in malspam ending up in the Junk folder instead of an Inbox.
Despite this, tactics like social engineering[2] and email spoofing can be used to make fake emails look more authentic. As a result, it's important to always be vigilant when checking your Inbox, as some dangerous emails might not get filtered into the Junk folder.
Ransomware developers often use several distribution techniques, which may include software vulnerabilities, malicious ads (drive-by downloads),[3] malicious websites such as torrents, and similar methods. Please make sure your system and installed software is always patched with the latest security updates and anti-malware is continuously running in the background to prevent infections.

Start with Rabel ransomware removal
While many ransomware viruses delete themselves after completing the encryption process, this may not always be the case. Furthermore, because ransomware is frequently spread with other harmful programs, it's critical to get rid of it correctly. The first step is to disconnect your PC from any networked connection.
Before you attempt to remove the virus and recover your data, make sure to cut off your computer's internet connection so it can't communicate with the remote server that the attackers are using. This is where a decryption tool is held, and various commands can be executed remotely.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
When the network connection is cut off, it's the perfect opportunity to start Rabel ransomware removal. The only guaranteed way to get rid of all malicious files and infections from your system is by doing a full system scan with tough anti-malware software like SpyHunter 5Combo Cleaner or Malwarebytes.
Data recovery process and other useful tips
When it comes to ransomware-encrypted file recovery, there are a variety of variables that can have an impact on the outcome in your specific case. Malware may be unable to encrypt all files or freeze when attempting to remove Shadow Volume Copies, making a recovery much easier. You may also nearly entirely negate the harmful effects of ransomware infection by maintaining backups of your most critical data.
These technicalities are often not known to the affected users, however, and some believe that their files are permanently damaged, while others think that they will be able to restore .rabel files as soon they finish scanning the device with anti-malware software. Neither of these perspectives is true.
As soon as ransomware finishes its job, its encryption is usually unbreakable, although, as mentioned above, failures do occur due to bugs or other reasons. If encryption is secure, it is unlikely that you will be able to restore all your files easily, although e strongly encourage you to try it instead of paying cybercriminals.
If you have backups ready, you should not worry about this at all, as you will be able to recover all your files – although please make sure that your system is clear from malware before you reintroduce your files. Unfortunately, most users who get infected with ransomware have no working backups available. If this is true for you, you should follow the detailed instructions we provide below.
First of all, you should make sure you make a copy of your encrypted files – transfer them over to a separate medium, such as a USB stick or SSD. If you don't do that and proceed with the steps below, you may end up corrupting all your files in a way that they wouldn't be recoverable, even with a working decryptor. After that, you can start by using dedicated data recovery software:
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
If this method does not work for you, you should keep an eye on free decryptors that are released by security experts on a regular basis. These may or may not be created for this particular Rabel ransomware, but we recommend keeping an eye on it (there are many factors that determine whether or not ransomware gets a free decryptor). Below you will find useful links to various security vendor websites and independent projects:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Finally, as the last step to recovery, you should resort to repairing your system that could have been caused by malware infection. If you don't address this, you may soon start suffering from system crashes, program errors, launch failures, Blue Screen of Death crashes, and more stability issues. The easiest way to tackle malware-related and even unrelated technical issues is by employing a powerful security tool:
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ What is encryption? | Types of encryption. Cloudflare. The Web Performance & Security Company.
- ^ Josh Fruhlinger. Social engineering: Definition, examples, and techniques. CSO Online. Business continuity and data protection.
- ^ Drive-by download. Wikipedia. The free encyclopedia.
