RegretLocker ransomware (Virus Removal Guide) - Virus Removal Instructions
RegretLocker virus Removal Guide
What is RegretLocker ransomware?
RegretLocker ransomware – virus demanding a ransom for computer data decryption

RegretLocker ransomware is a type of malware that encrypts all victims' personal files with military-grade algorithms upon infecting users' computer systems.[1] After the encryption is complete, a ransom note usually appears in contaminated folders. In this case, a “HOW TO RESTORE FILES.txt” file can be found.
RegretLocker ransomware virus appends all non-system files with an extension .mouse. Infected files cannot be opened. The ransom note is very brief. The cybercriminals inform the victim that its files were encrypted, and if they want to retrieve the data, they should contact the perps via email at petro@ctemplar.com. Also, a unique hash is given to be provided upon contact. Further details, like ransom amount, would be delivered after contacting the cyberthieves.
| NAME | RegretLocker virus |
|---|---|
| TYPE | Ransomware |
| APPENDED EXTENSION | .mouse |
| RANSOM NOTE | “HOW TO RESTORE FILES.txt” can be found within infected folders. The note contains cybercriminals' contact information and a unique generated hash, as a form of ID |
| Distribution | Files that contain ransomware payload can be attached to an email or loaded from the malicious link added on such notification. Pirated software platforms and other possibly malicious files can lead to infections like this cryptovirus |
| CONTACT EMAIL | petro@ctemplar.com |
| ISSUES | Users' computer data is encrypted and appended with extension .mouse. Infected files cannot be opened. Additional malware can get installed and system functions corrupted |
| elimination | RegretLocker ransomware removal should be left to professionals. Use SpyHunter 5Combo Cleaner or Malwarebytes to automatically delete the virus from affected devices |
| SYSTEM FIX | Malware possibly altered system data, which may lead to irregular device work, use FortectIntego to restore system health. |
To get in touch with RegretLocker ransomware or any other developers is highly inadvisable. Instead of the decryption tool that the cyber criminals promise they will deliver after payment, victims might be scammed even more. Rather than receiving what was assured, trojans or malware alike could be given to them to infect their devices even more so that the cyber thieves could ask for even more money.
RegretLocker ransomware removal is of utmost importance. Users should do that immediately after the ransom note delivery. Although such viruses' termination won't bring back users' data, eliminating the virus ensures that encryption is not going to be repeated.
If victims don't have backups on different locations, they should extract all contaminated files to an offline removal drive, such as USB, and wait for a decryption key to be released. It is possible in the future but takes a lot of time because researchers need to obtain various files from RegretLocker ransomware developers to provide such tools for victims.
To remove RegretLocker ransomware, we advise using trustworthy anti-malware apps such as SpyHunter 5Combo Cleaner or Malwarebytes, as it will automatically detect[2] the virus and all its allocated files, isolate and remove them. Due to the nature of ransomware, users' system files might have also been edited.
After RegretLocker ransomware removal, use a tool like FortectIntego to fix any damage done to the system registry, power shell and prevent your system from abnormal behavior like crashes and overheating etc.
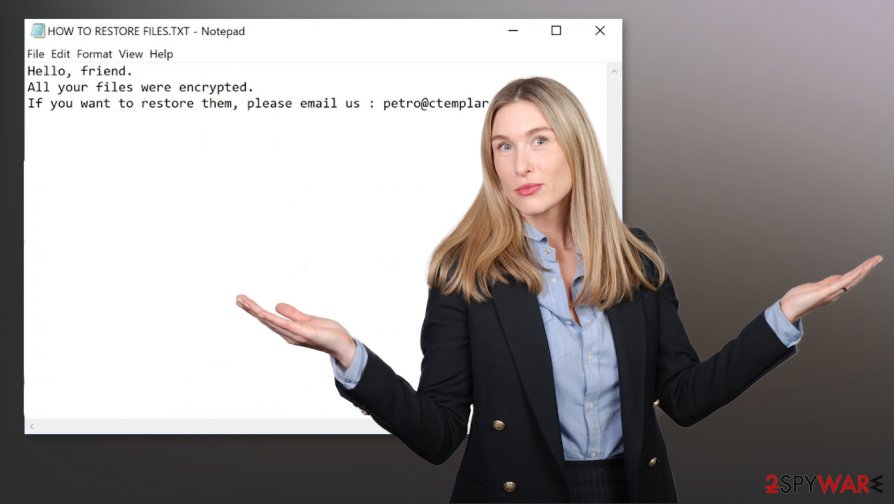
Ransom notes “HOW TO RESTORE FILES.txt” content (with a removed hash):
Hello, friend.
All your files were encrypted.
If you want to restore them, please email us : petro@ctemplar.com
Your hash:
Techniques cybercriminals use to infect computer devices
Cybercriminals have numerous methods at their disposal to infect computer systems. Infected files can be downloaded by opening a deceitful email with malicious content, such as hidden mischievous hyperlinks or contaminated attachments.
Downloading various torrents from their distribution sites (the same applies to social media and other file-sharing platforms) is also an easy way to receive a virus and ruin your day. Perpetrators might camouflage malware as game cheat codes, valid installers, software update tools, illegal software activation kits (also known as “cracks”), to name just a few.
After malware gets in a device, it immediately starts its bidding. Users should be aware of threats and act carefully whilst browsing and opening fishy-looking sites and content in them. The smart thing to do is have a reliable anti-malware tool to stand in-between the user and the cybercriminals. Having backups of all sensitive information adds another layer of security.[3]
RegretLocker ransomware virus removal from infected computer systems
Removing a virus manually might seem a tall task even for proven, highly experienced computer users as this process is challenging and lengthy, requires extensive knowledge. All malware, such as RegretLocker ransomware removal should be left to professionals like SpyHunter 5Combo Cleaner or Malwarebytes to automatically delete the virus and all its files spread throughout the device. Any malware pieces that haven't been deleted might renew the infection.
For malware to work uninterrupted, it usually corrupts system files. That might cause devices to exhibit unusual running symptoms. To remove RegretLocker ransomware aftermath, we strongly advise using the FortectIntego tool to get users' systems to its previous condition, as if nothing ever happened.
Getting rid of RegretLocker virus. Follow these steps
Manual removal using Safe Mode
Reboot the machine in Safe Mode with Networking and run AV tool to remove RegretLocker ransomware
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove RegretLocker using System Restore
System Restore can get employed for the virus removal process
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of RegretLocker. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove RegretLocker from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by RegretLocker, you can use several methods to restore them:
Data Recovery Pro is the tool for file restoring
You can restore files after RegretLocker ransomware encryption or accidentally deletion with a program like Data Recovery Pro
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by RegretLocker ransomware;
- Restore them.
Windows Previous Versions – a feature that helps with users affected files
When System Restore gets enabled, you can rely on Windows Previous Versions and recover those affected files
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer is the program that can trigger the file recovery
Shadow Volume Copies, when left untouched, can be used in file recovery using ShadowExplorer feature
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption tool for RegretLocker ransomware is not availiable
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from RegretLocker and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Josh Fruhlinger. Ransomware explained: How it works and how to remove it. CSOonline. Technology and security news.
- ^ Virus detection rate. VirusTotal. Online malware scanner.
- ^ What Are the Different Types of Data Backups?. TPX. Cybersecurity communications.





















