RekenSom ransomware (Removal Instructions) - Recovery Instructions Included
RekenSom virus Removal Guide
What is RekenSom ransomware?
RekenSom ransomware – a crypto-malware asks for 0.015 BTC for file redemption

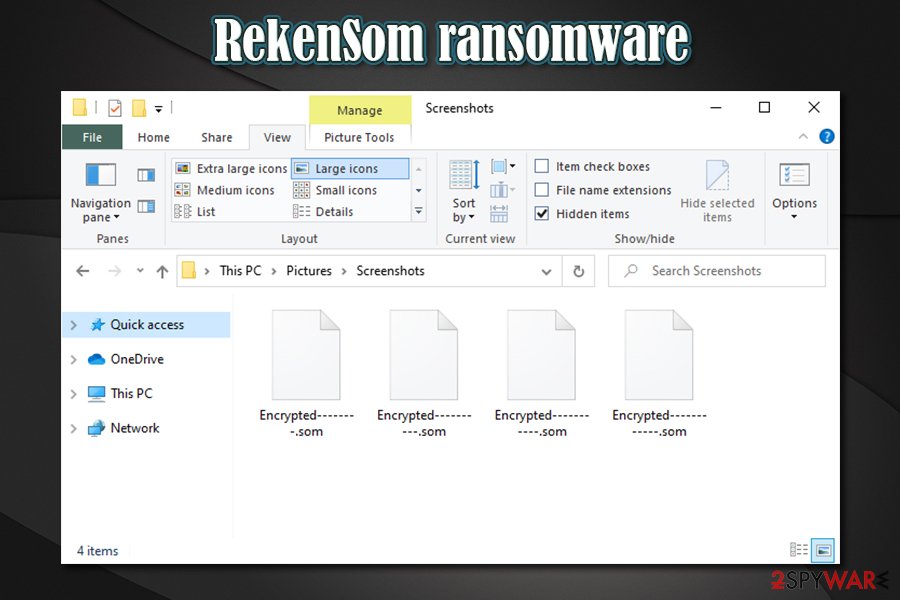
RekenSom ransomware, otherwise known as Ghack ransomware, is a file locking virus that was first spotted by security researchers in mid-March 2020. Just like any other malware of such type, it will encrypt pictures, videos, documents, and other data on the host system with the help of a strong encryption algorithm (AES and RSA)[1] and then demands a ransom for the decryption tool that would allow victims to access it once again. Besides adding an extension, the RekenSom virus also scrambles the names of files, making them unrecognizable.
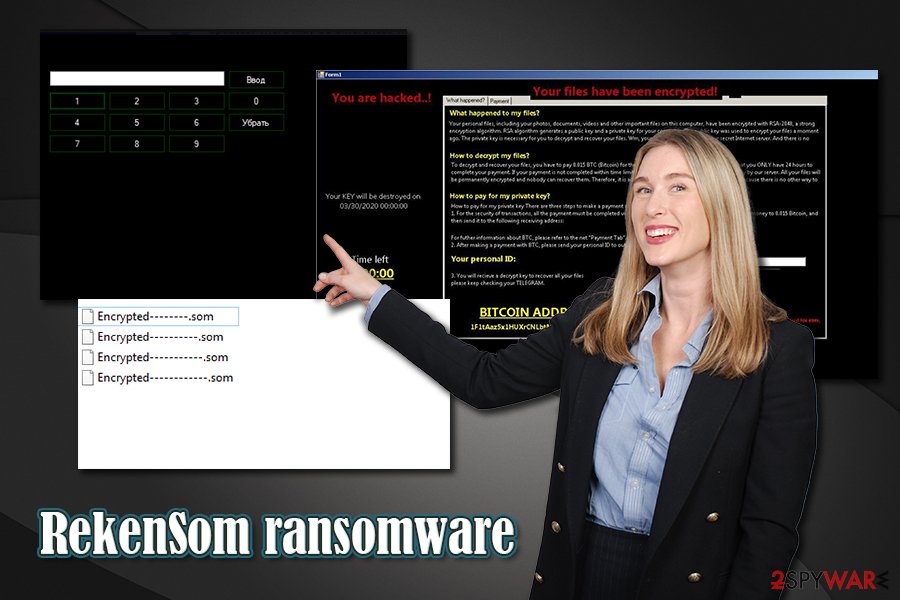
Currently, there are two different versions of RekenSom ransomware – ope appending .RekenSom extension, while the other one – .som (in some cases, the malware will also delete files instead of encrypting them). After the data locking process, it will drop a pop-up window named “Form1,” which informs victims that they need to pay 0.015 Bitcoin in order to recover access to their data. Instead of providing an email address, cybercriminals behind RekenSom ransomware instead use Telegram for communication purposes (@Rekensom).
| Name | RekenSom ransomware |
| Type | File locking virus, crypto-malware |
| Family | Cute/MyLittleRansomware > KRider |
| Encryption method |
All non system files and non executables are appended in different ways, depending on version:
|
| Related files | Reken.exe, FinalReken.exe, GHack.exe, WindowsFormsApplication8.exe, secretAES.txt, secret.txt, sendBack.txt |
| Ransom note | First few samples of malware did not include a ransom note or showed a pop-up including just a numpad. The most recent variant (.som) delivers a pop-up window called “Form1” which explains the situation to victims in detail |
| Contact | In the ransom note, crooks ask users to first pay the ransom and then contact them via Telegram @Rekensom |
| Ransom size | 0.015 Bitcoin. According to crooks, if this payment will not be performed within 24 hours, decryption key will be deleted |
| Bitcoin wallet | 1F1tAaz5x1HUXrCNLbtMDqcw6o5GNn4xqX |
| Data recovery | Without backups, there is not a safe and 100% working method of data recovery. Paying cybercriminals is very risky, as they might never deliver the required decryption tool. You can find alternative approaches that might be able to help you to retrieve access to at least some of your files below. Before you attempt this, ensure you make a copy of all the locked data |
| Malware removal | To get rid of the infection, you should scan the machine with powerful anti-malware software |
| System fix | In case Windows is malfunctioning after you eliminate the malware, repair virus damage with FortectIntego |
While there is no RekenSom ransomware decryptor currently available that would help you recover your files for free, you should not rush to pay the ransom or contact the criminals. It is yet unclear what type of cybercriminals are behind this strain and whether they are willing to provide the required decryption tool after the payment is made. Instead, you should remove RekenSom ransomware and then attempt to retrieve your files using different methods that we list in our recovery section below.
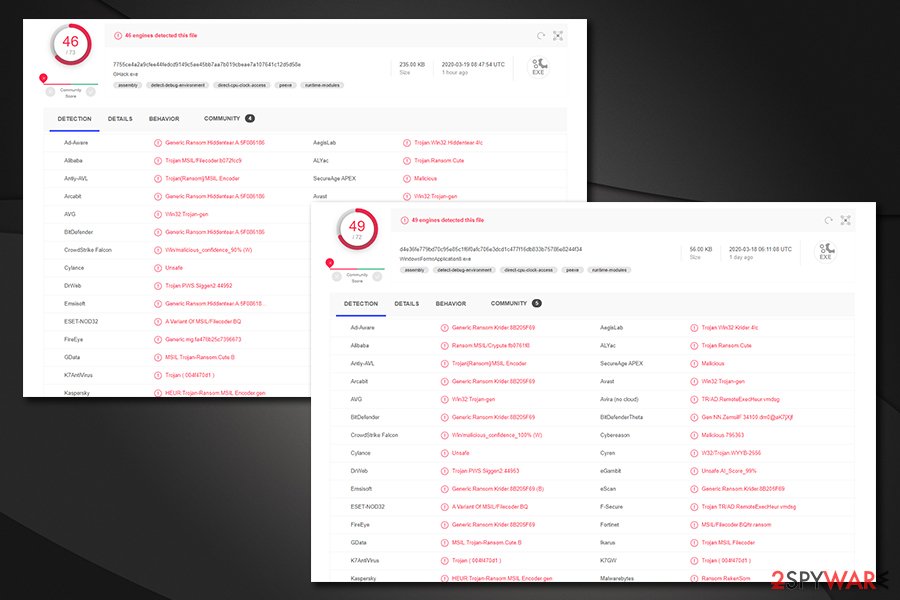
If RekenSom ransomware removal is not performed, your data will be encrypted repeatedly. Nevertheless, it is also important to make a copy of files that were affected by malware first, as any type of action might permanently damage them. As for termination of the virus, you can employ anti-malware tools that recognize the infection under the following names:[2]
- Generic.Ransom.Hiddentear.A.5F086186
- MSIL.Trojan-Ransom.Cute.B
- Ransom:MSIL/Rekensom.AA!MTB
- HEUR:Trojan-Ransom.MSIL.Encoder.gen
- Win32:Trojan-gen
- A Variant Of MSIL/Filecoder.BQ, etc.
In case RekenSom ransomware termination affected your computer in negative ways, and you are experiencing lags, crashes, random reboots, BSODs, and similar issues, use repair software FortectIntego to fix virus damage at once.
RekenSom was still in development
It is believed that RekenSom ransomware stems from an old malware family – KRider, although its initial actions pointed at the fact that it was still under active development. First samples of the malware that were spotted in the wild did not provide any ransom note. Later on, cybercriminals added a lockscreen that would only include a number pad – allegedly where some type of code should be inserted. Nevertheless, no contact info was provided, so there was no way of finding out what the password was. Additionally, the first few samples of the RekenSom virus only encrypted data on the desktop.
Typically, ransomware uses a secure encryption algorithm (either symmetric or asymmetric, or a combination of those) to lock all data on the device, and assigns each victim with a unique ID. This identifier is then sent over to the Command $ Control server, along with the decryption key that is needed to unlock files. RekenSom ransomware failed to contact its servers and deliver the key at first.
Finally, with the .som variant of RekenSom ransomware, a meaningful ransom note was found – named Form1. It informed users that their files have been encrypted with the RSA-2048 algorithm and that users only have 48 hours to deliver the payment of 0.015 BTC to the attackers. The ransom note states:
What happened to my files?
Your personal files, including your photos, documents, videos and other important files on this computer, have been encrypted with RSA-2048, a strong encryption algorithm. RSA algorithm generates a public key and a private key for your computer. The public key was used to encrypt your files a moment ago. The private key is necessary for you to decrypt and recover your files. Wm, your private key is stored on our secret Internet server. And there is no doubt that no one can recover your files without your private key.How to decrypt my files?
To decrypt and recover your files, you have to pay 0.015 BTC (Bitcoin) for the private key and decryption service. Note that you ONLY have 24 hours to complete your payment. If your payment is not completed within time limit, your private key will be deleted automatically by our server. All your files will be permanently encrypted and nobody can recover them. Therefore, it is advised that you'd better not waste your time, because there is no other way to recover your files except making a paymentHow to pay for my private key?
How to pay for my private key There are three steps to make a payment and recover your files.
1. For the security of transactions, all the payment must be completed via Bitcoin network This, you need to exchange some money to 0.015 Bitcoin, and then send it to the following receiving address:For futher information about BTC, please refer to the net “Payment Tab”.
2. After making a payment with BTC, please send your personal ID to out TELEGRAM: @RekensomYour personal ID:
3. You will recieve a decrypt key to recover all your files
please keep checking your TELEGRAM.BITCOIN ADDRESS
1F1tAaz5x1HUXrCNLbtMDqcw6o5GNn4xqX
WARNING: If you close this window your files will be deleted for ever.
just warning you
As evident, crooks claim that the decryption key will be deleted if the demands are not fulfilled in time – this tactic makes users act more quickly rather than think of other methods of retrieving data. Indeed, currently, there is no decryption tool that would recover data locked by RekenSom virus for free, but paying criminals is very risky. Hence, try using alternative methods we provide below instead.
Before encrypting files, RekenSom ransomware also performs a variety of changes to the Windows machine, such as modifications to the registry database, deletion of Shadow Volume Copies, insertion of malicious files, etc. In fact, the malware has a module that allows the attackers to steal information from the computer. Thus, never type anything or visit online banking, social media, or similar sites that require you using your personal details, as they could be stolen by cybercriminals behind RekenSom.
Threat actors can employ multiple different methods to deliver ransomware to victims
Malware delivery methods vary – it highly depends on the business model operated by crooks. For example, one of the most prominent ransomware families Djvu is distributed via software cracks and pirated software installers exclusively – it manages to infect hundreds of users daily. In the meantime, other strains such as Nemty/Nefilim or Dharma use multiple attack vectors[3] to infect victims worldwide.
Since new ransomware samples emerge almost every day, it is not always known what the main distribution tactic is. Therefore, to protect yourself from the most devastating malware type around, keep in mind the following things:
- Watch out for spam emails – attachments or obfuscated hyperlinks may be infectious so ensure that the email is legitimate first;
- Equip your computer and networks with reputable anti-malware software with real-time protection feature;
- Patch your operating system and the installed programs as soon as the updates are released;
- Use strong passwords to protect your accounts – especially Remote Desktop connection (while using it, employ a VPN);
- Never download software cracks/keygens/loaders, etc.;
- Backup your most important files regularly – this could prevent most of the negative consequences of the infection!
Finally, the most important thing is to be careful and act responsibly when browsing the web and checking the email. If in doubt – do not enter the site, do not click on links, and seek help on tech forums or security blogs instead.
Terminate RekenSom virus infection and only them attempt to recover data
Malicious actors behind the RekenSom virus claim that you will not be able to recover data if you close the pop-up window “Form1” that shows the timer. Therefore, it is important not to perform any actions before copying the encrypted data over to a secure environment where the malware will no longer be capable of destroying it. Thus, use a USB flash driver or a virtual drive like Dropbox to make a copy of your files. Then, proceed with RekenSom ransomware removal (note that this is only applicable to victims that do not have backups to recover data from).
To remove RekenSom ransomware from your machine, you should employ a reputable anti-malware program of your choice. In case the virus is tampering with it, access Safe Mode with Networking and perform a scan from there – you can find the instructions on how to do that below. Finally, use alternative methods to recover your data, although keep in mind that they might not always be successful, unfortunately.
Getting rid of RekenSom virus. Follow these steps
Manual removal using Safe Mode
Use Safe Mode with Networking if malware is interfering with your security software:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove RekenSom using System Restore
Safe Mode is another method to get rid of the infection:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of RekenSom. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove RekenSom from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by RekenSom, you can use several methods to restore them:
Make use of Data Recovery Pro software
This third-party tool might be able to retrieve at least some of your files on your hard drive (note that chances diminish upon using your computer more).
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by RekenSom ransomware;
- Restore them.
Windows Previous Versions feature might help you recover .RekenSom or .som files
If you had System Restore enable before the virus attacked, you could try using Windows Previous Versions feature.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer method might be useful
If the RekenSom file virus failed to delete Shadow Volume Copies, this tool should be able to recover your data for free.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryption tool is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from RekenSom and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Encryption. Proofpoint. Security blog.
- ^ 7755ce4a2a9cfee44fedcd9149c5ae45bb7aa7b019cbeae7a107641c12d5d58e. Virus Total. File and URL analysis.
- ^ Ransomware statistics for 2019: Q2 to Q3 report. Emsisoft. Security blog.





















