Requestfor4.com (Virus Removal Guide) - Free Instructions
Requestfor4.com Removal Guide
What is Requestfor4.com?
Requestfor4.com – adware that provides a human verification service to lure users into constant advertising
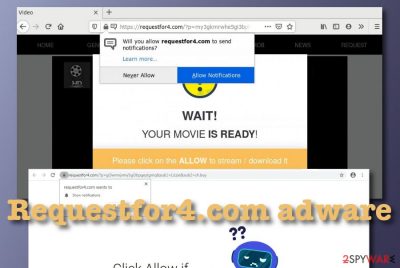
Requestfor4.com is considered to be an ad-supported program[1] that pushes notifications whenever the user is working via the infected web browser. First of all, the bogus domain will throw you a pop-up window claiming that you need to click “Allow” in order to confirm that you are not a robot or watch some type of hidden video. This is where the trick lies. Requestfor4.com tries to gather as many subscribers as possible by stating such false claims and attracting the users near the “Allow” button. Do not give permission to the incoming pop-up ads as it might be hard to get rid of them later on.
Requestfor4.com virus is an initiator of potentially unwanted activities such as advertising, redirecting, and others. This type of product can appear on your computer system due to the lack of proper protection on your machine and web browsers. Throughout this article, we are going to explain the operating principle of this adware, the risks that it can bring to your computer system, how to avoid secret PUP invasion, and how to get rid of the product automatically and manually.
| Name | Requestfor4.com |
|---|---|
| Category | Adware/PUP |
| Signs | When the adware appears on your web browsers, you are likely to find yourself dealing with an excessive amount of advertisements and redirects. Also, you might find some browser changes in the homepage and new tab URL sections, encounter some questionable extensions added |
| Risks | The potentially unwanted program can redirect you to a location that is filled with malware and this way you might get a very dangerous computer infection. Also, the adware might provide you with bogus surveys that ask for entering personal or banking information that can, later on, lead to identity or money theft |
| Termination | If you have been dealing with this unwanted product recently, you should get rid of it right away. We recommend using reliable antimalware software for completing the process. However, if you are likely, you can try out the manual step-by-step guidelines that have been added to the end of this article |
| Fix | Try fixing all compromised system areas with the help of FortectIntego |
Requestfor4.com can attack all types of web browsers and interfere with their settings. Once infected with this adware, you might discover that the homepage and new tab URL section have been modified against your own will. Besides, do not get surprised if the PUP leaves unrecognizable extensions on your browsers too. The computer system might also get a little bit modified by the adware. You might encounter rogue processes operating in the Task Manager.
Once Requestfor4.com has settled in, it will start acting. One of the main signs from which you should be able to recognize the adware is advertising. Loading an excessive amount of ads is the biggest part of the developers' business as these adverts bring them monetary benefits.
Requestfor4.com pop-ups can appear at any time whenever you are using the infected web browser app. This becomes very stressful after a while of time because every time you try to find your desired search results, your computer screen gets covered in questionable-looking offers and deals.
Furthermore, this can affect your computer's and browser's performance level that has a tendency to decrease slightly. If Requestfor4.com pop-up ads start appearing more usual then ever, you are likely to receive constant browser freezes, struggles, and even crashes. The same can happen with your computer system if the adware program tries to run multiple processes at a time and overuses your CPU power.
However, there is more yet to come while dealing with Requestfor4.com. The advertisements that this program provides might aim to collect personal details if they are provided in some types of surveys, fake reward claims, etc. You have to be really careful while dealing with these ads and try not to reveal any sensitive information, especially when it comes to details related to your identity or banking account as you can never know when some hacker might try to misuse the data.
Another issue that you are likely to encounter is redirecting. Requestfor4.com can take you to places that are related to various offers and deals. There you might be encouraged to purchase products and services that you do not need, for example, rogue security software.
However, the worst part about getting redirected is that you cannot know where you will land. Almost all the time the domains that Requestfor4.com takes you to will not be properly secured. Regarding this fact, you might fall to a location where malware developers might be hiding their malicious software.
Requestfor4.com removal is necessary if you do not want to wait for a cyber threat to appear out of nowhere. Nevertheless, the adware itself can be a deliverer of various malware forms as it is a very handy distribution technique for some.
Moreover, Requestfor4.com can bring not only dangerous viruses but also a bunch of other potentially unwanted programs to the computer system such as browser hijackers, adware, scareware, etc. When you are infected with this product, you should search your entire computer system and find out if the PUP[2] has brought other unexpected components.
Another reason why you should remove Requestfor4.com from your computer system is that the adware can record browsing information that is related to your search queries, IP address, saved bookmarks, geolocation, visited websites, and so on. This type of data might be passed to other parties for income or the developers can use the information for gathering attractive-looking adverts.
If you think that Requestfor4.com might have compromised some system areas on your device, you should check out this possibility automatically. If you discover any unusual alterings, you can try fixing the corruption with a tool such as FortectIntego.
Adware deliverers use unfair methods to reach their targets
Cybersecurity specialists from LosVirus.es[3] claim that adware developers are into “software bundling”[4] when the means come to the delivery process. PUPs such as adware often get bundled with other freeware and shareware that the users download from the Internet. Software packages often include additional components and this material is placed on the system whenever the user skips a downloading step or sets the “Recommended” mode as default.
What you have to do is ensure that no downloading step is missed during the process. Deselect all the suspicious components that you see and choose the “Advanced” option that will allow you to do so.
Furthermore, you can receive adware programs as fake software updates while visiting unsafe domains. Always listen to your antimalware if it alerts that the page ahead of you is not safe for proceeding to. Continuously, if you accidentally enter an unknown website, you should close the browser window immediately.
Also, avoid clicking on hyperlinks and advertisements that appear to you while surfing the Internet. Click on such locations only if you really need to and they do not pop out randomly every time you start browsing. Besides, keep your antivirus protection turned on and updated in case a virus tries to sneak into your computer system.
Requestfor4.com elimination guidelines for both Windows and Macs
Below we have provided some instructing steps that should help you to remove Requestfor4.com from your operating system and web browsers such as Google Chrome, Mozilla Firefox, Internet Explorer, and Safari manually. You need to ensure that your browser apps do not hold any extensions, plug-ins, and other suspicious components that can be related to the ad-supported program.
If the manual Requestfor4.com removal appears to be too difficult or time-consuming to you, there always is the automatical option that allows terminating all types of suspicious products with the help of reliable antimalware software. Make sure to choose a reputable tool and the product will do everything for you in a few minutes of time. Keep in mind that if any adware-based content is still left in the system, there is a risk that the adware will return slightly.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Requestfor4.com. Follow these steps
Uninstall from Windows
To eliminate unwanted products from your Windows computer system, employ the below-provided step-by-step guidelines:
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
To get rid of potentially unwanted programs from your macOS computer, you should complete the following instructions:
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
To remove all questionable extensions from Mozilla Firefox and diminish unwanted changes, complete the guide below:
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
[To terminate suspicious content from Google Chrome and reverse all suspicious modifications that were brought by the adware program, you can try using the following instructions:/GI]
[GI=safari]
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Requestfor4.com registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ What is Adware?. Kaspersky. Resource Center.
- ^ Potentially unwanted program. Wikipedia. The free encyclopedia.
- ^ LosVirus.es. LosVirus. Security and spyware news.
- ^ Bundled Software. Computer Hope. Free computer help since 1998.




















