RobbinHood ransomware (Virus Removal Instructions) - Oct 2019 update
RobbinHood virus Removal Guide
What is RobbinHood ransomware?
RobbinHood ransomware is file locking malware that cost Baltimore city $4.6 million in recovery costs
RobbinHood ransomware is crypto-extortion based malware that mainly targets large scale corporations and municipalities, encrypting entire networks that are connected to the initial host. Baltimore, as well as Greenville cities, both suffered significant losses due to ransomware attack – hackers initially demanded $76,000 in Bitcoin, claiming that the fee will increase by $10,000 each day.[1] While no ransom was paid, Baltimore put in a staggering $4.6 million in recovery costs, with $5.4 still pending to be invested till the end of the year.
Initially, it was unknown how RobbinHood ransomware spreads, but later experts found out that hackers either proliferate file locking virus via already infected computer or via insecure Remote Desktop connections – a technique that had been gaining popularity in recent years among ransomware developers.
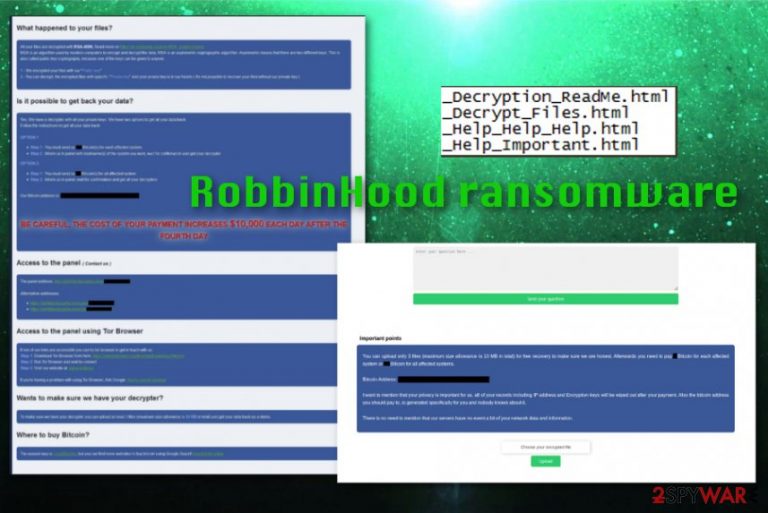
After encrypting files with the RSA + AES encryption algorithms and appending Encrypted_[random 16].Enc_robbinhood extension to files,[2] RobbinHood virus developers demand the ransom payment for the recovery of locked data. The ransom is either 0.8 BTC or 13 BTC, depending on the number of affected devices. Unlike most ransomware viruses, RobbinHood drops four ransom notes under the following names:
- note _Decryption_ReadMe.html
- _Help_Important.html
- _Decrypt_Files.html
- _Help_Help_Help.html
| Name | RobbinHood |
|---|---|
| First spotted | April 2019 – attack on Greenville city was among the first ones seen in the wild |
| Alternative name | Enc_RobbinHood ransomware |
| Type | Cryptovirus |
| Notable targets | Baltimore and Greenville cities |
| File modification | All the files encrypted by RobbinHood get their names completely scrambled in the following pattern: RoEncrypted_[random 16].Enc_robbinhood |
| Encryption method | Ransomware uses AES key to encrypt each file individually and each of those keys are then repeatedly encrypted with RSA public key |
| Ransom amount | Ransom sizes vary. In some instances, hackers demanded 0.8 BTC for a single computer decryption while full network recovery would cost 13 BTC. In other cases, crooks asked for 3 BTC and 7 BTC, respectively |
| Ransom notes | Surprisingly, this malware drops four ransom notes, which is pretty unusual – _Decryption_ReadMe.html, _Help_Important.html; _Decrypt_Files.html; _Help_Help_Help.html |
| Distribution | Ransomware is spread either as a secondary payload on already infected computer or by abusing inadequately protected Remote Desktop connections |
| Elimination tips | Get a reputable anti-malware program for the proper RobbinHood ransomware removal. Use FortectIntego for system cleaning |
Since RobbinHood ransomware is a member of the cryptovirus category, you should be aware of the possible damage for encrypted data or even privacy issues and data or money loss. Especially, if you decide to pay the ransom and contact these virus developers.[3]
While RobbinHood ransomware virus mainly targets large organizations or even governments, health industries, and institutions,[4] it does not mean that home users are safe from this infection. Be aware that malware authors could use various infection means, so the target machine could be selected completely randomly.
RobbinHood ransomware besides the file encryption can:
- install programs, files;
- disable processes and other functions;
- run additional malicious processes;
- alter registry keys or add new ones;
- steal information stored on the machine;
- delete or damage files.
However, the main symptom of this RobbinHood ransomware is data encryption and ransom demand. The changed name can indicate data that got encoded. Once files get unreachable and locked, the ransom note – _Decryption_ReadMe.html delivers the following message:
What happened to your files?
All your files are encrypted with RSA-4096, the Read more on https://en.wikipedia.org/wiki/RSA_(cryptosystem)
the RSA is an algorithm Used by modern computers to the encrypt and decrypt the data the. RSA is an asymmetric cryptographic algorithm. Asymmetric means that there are two different keys. This is also called public key cryptography, because one of the keys can be given to anyone:
1 – We encrypted your files with our ” Public key”
2 – You can decrypt, the encrypted files with specific “Private key” and your private key Our phone hands in is (It's not Possible to recover your files is the private key without Our)
—
is Possible IT to the get back your data?
Yes, we have a private keys. Data back options.
Follow the instructions to get all your data back:
OPTION 1
Step 1: You must send us 0.8 Bitcoin (s) for each affected system
Step 2: Inform us in panel with hostname ( s) of the system you want, wait for confirmation and get your decrypter
OPTION 2
Step 1: You must send us 13 Bitcoin (s) for all affected system
Step 2: Inform us in panel, wait for confirmation and get all your decrypters
Our Bitcoin address is: 132wg6kkJJ4MpNKnuhVoptYPmYHf6C5xHE BE CAREFUL, THE COST OF YOUR PAYMENT INCREASES $ 10,000 EACH DAY AFTER THE FOURTH DAY —The panel to the Access (Contact us)
of The panel address: http://xbt4titax4pzza6w.onion/EvcNuvq4gckb/
Alternative addresses The
https://xbt4titax4pzza6w.onion.pet/EvcNuvq4gckb/
https://xbt4titax4pzza6w.onion.to/EvcNuvq4gckb/
– –
the Access to the panel using the the Tor Browser
the If the non of Our links are accessible Template you CAN tor's browser the try to the get in touch with us:
the Step 1: Download Tor Browser from here: https://www.torproject.org/download/download . html.en
Step 2: Run the Browser Browser and wait for connect
Step 3: Go to the
Google Browser, Ask Google: how to use the browser
—
Wants to make sure we have your decrypter?
You can upload at most 3 files (maximum size allowance is 10 MB in total) and get your data back as a demo.
—
Where to buy bitcoin?
The easiest way is to find bitcoin using Google Search: buy bitcoin online
RobbinHood ransomware developers as any other cybercriminals encourage people to pay the demanded ransom and guarantees the decryption. However, these people are malicious, and the test decryption that may be offered is not a good idea. This is the trick to make developers look more trustworthy.
You need to get a reputable anti-malware tool and remove RobbinHood ransomware instead. This method is recommended by many experts[5] all over the world because ransomware should be removed alongside all the programs and files. A full system scan that antivirus program can offer is the best solution.
RobbinHood ransomware removal using anti-malware tools allows seeing all potential threats and delete them with one program. AV program offers a full system scan and a security check, other features. Employ malware-fighting tool and clean the system entirely. We can also recommend using FortectIntego, a program that helps with virus damage and system issues.
Hackers behind RobbinHood included the Baltimore and Greenville incidents as an examples in the ransom note
One of the newest RobbinHood ransomware variants came with a little bit more extra on its ransom note. It seems like malicious actors are trying to build up a reputation among its victims and the cyberinimal world, as they are eager to mention the most prolific incidents that involved their malware.
The attack on Baltimore occurred on May 7, 2017, and crooks asked for $76,000 to decrypt all the impacted computers and stored data on them. They also noted in the ransom note that, after four days, the ransom will be increased by $10,000 daily. Baltimore did not pay the ransom in the end, but it cost the city $4.6 million in recovery costs so far – officials said that another $5.4 million will be invested soon. According to some sources, RobbinHood attack cost the city $18 million by June.[6] However, the impact this large was not only due to the ransomware attack only – the way it was handled, along with lackluster of security measures prior to the incident.
The colossal losses boasted the confidence of hackers behind RobbinHood ransomware, so much so that they now include the names of the highly publicized incidents in the ransom note. They now claim that the keys that can unlock the compromised files will be deleted within 10 days after the initial infection, although also demand victims to stay away from the FBI and other sources that could help them with the recovery process. According to crooks. the recovery is “impossible”:
In summery, you can't read or work with your files, But with our help you can recover them.
It's impossible to recover your files without private key and our unlocking software (You can google: Baltimore city, Greenville city and RobbinHood ransomware)
While it is true that no decryption tool for RobbinHood ransomware currently exists, security experts are continuously working on ransomware decryptors all the time. However, there is no guarantee that such tool will eventually be made. As of now, the only way to recover data is by using backups, trying third-party recovery software, or paying RobbinHood authors and hoping for a working decryptor. As usual, the latter is highly discouraged.
Unprotected RDP connections and other malware causes ransomware infections
There are many different ways how ransomware developers can infect computers, such as using exploits, fake updates, software cracks, spam emails, etc. However, because this malware strain mainly targets organisations and cities, relying on malicious files placed on the internet is simply ineffective. Therefore, more an more high-profile cybercriminals rely on targeted method of infection, and Remote Desktop insecure connections are among the primary ones.
Therefore, if you are using RDP, you need to make sure that it is adequately protected. Cybercriminals scan the internet for devices that are connected to RDP via the default TCP port 3389. Once found, they use a predetermined (but automated) process that manages to brute-force itself in, allowing malicious actors to connected to the host machine remotely and install malware manually.
Therefore, it is vital to avoid using default port for RDP, use strong passwords, limit who can connect to particular connections and turning the RDP off as soon as it is not needed. Additionally, users are advised to make sure their computers are protected by robust anti-malware software at all times to avoid other malware infections which can carry secondary payloads. Finally, a proper backup systems should be implemented in all firms – the best countermeasure against ransomware attack.
Clean the machine and eliminate RobbinHood ransomware, malicious processes and other malware with one professional AV tool
Get rid of the RobbinHood ransomware virus by cleaning the system entirely. This is a great method because all additional programs can get deleted this way. Also, there is no need to have a degree in IT or any experience.
To remove RobbinHood ransomware properly, you need to get a reputable anti-malware program and scan the machine thoroughly. FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes are the programs that also can help with improving the general performance of your PC.
Make sure to perform a complete RobbinHood ransomware removal and then recover your files with backed up data or using the data recovery software. We have a few suggestions below as well as additional virus elimination tips.
Getting rid of RobbinHood virus. Follow these steps
Manual removal using Safe Mode
RobbinHood ransomware should be removed with AV tools, but enter the Safe Mode with Networking and eliminate this threat fully:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove RobbinHood using System Restore
Try System Restore feature and make the computer virus-free again:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of RobbinHood. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove RobbinHood from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by RobbinHood, you can use several methods to restore them:
Data Recovery Pro should be used for file restoring purposes
Data Recovery Pro can help with RobbinHood ransomware encrypted files or accidentally deleted data
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by RobbinHood ransomware;
- Restore them.
Windows Previous Versions feature is the alternate method when file backups cannot be used
Unfortunately, System Restore should be enabled before, or Windows Previous Versions would not work
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer – method for data recovery
You can restore encrypted files with ShadowExplorer when Shadow Volume Copies are left untouched
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption tool is not available for RobbinHood ransomware
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from RobbinHood and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ GRAHAM CLULEY. RobbinHood ransomware attack brings down parts of City of Baltimore’s computer network. The state of security. News. Trends. Insights.
- ^ RSA. Wikipedia. The free encyclopedia.
- ^ Mark Kaelin. Avoid ransomware payments by establishing a solid data backup plan. Techrepublic. News, tips, and advice.
- ^ Gene Marks. Owners must protect their businesses from ransomware before it's too late. Theguardian. News, sport and opinion.
- ^ Virusi. Virusi. Spyware related news.
- ^ Kimberly Eiten. Baltimore Ransomware Attack | City Inches Closer To Normal Operation. CBS Baltimore. News network.







