Romeks.live ads (scam) - Free Guide
Romeks.live ads Removal Guide
What is Romeks.live ads?
Romeks.live uses deceitful techniques to persuade individuals into buying software

Romeks.live is among the numerous websites that use fraudulent tactics to mimic well-known security vendors and trick users into clicking on affiliated links to purchase their software. This malevolent website can crop up at any moment when users are browsing the internet on various browsers, such as Chrome, Safari, Edge, Firefox, and others. The malicious redirect is likely triggered when users click on suspicious links found on illicit websites like torrents, illegal video streaming sites, and the like.
Moreover, users may encounter Romeks.live more frequently if they are plagued by adware, which could lead to a surge in unsolicited ads and phishing sites. Thus, it is crucial to eliminate any unwanted software from the system to put a stop to persistent redirects.
| Name | Romeks.live |
| Type | Scam, phishing, redirect, adware |
| Operation | A message claims the subscription for security software has expired and needs to be immediately renewed to remove the allegedly found viruses on the system |
| Distribution | Compromised websites, pop-up ads, potentially unwanted applications |
| Risks | Loss of finances due to fake subscriptions; redirects to other malware-laden, scam websites; installation of potentially unwanted or malicious software |
| Removal | You should not interact with the contents shown by a scam website and check your device with legitimate security software to check for adware |
| Other tips | To make sure that third parties can no longer track your online activities, we suggest clearing browser caches and other leftover PUP files with FortectIntego |
Scammers urge to renew subscription
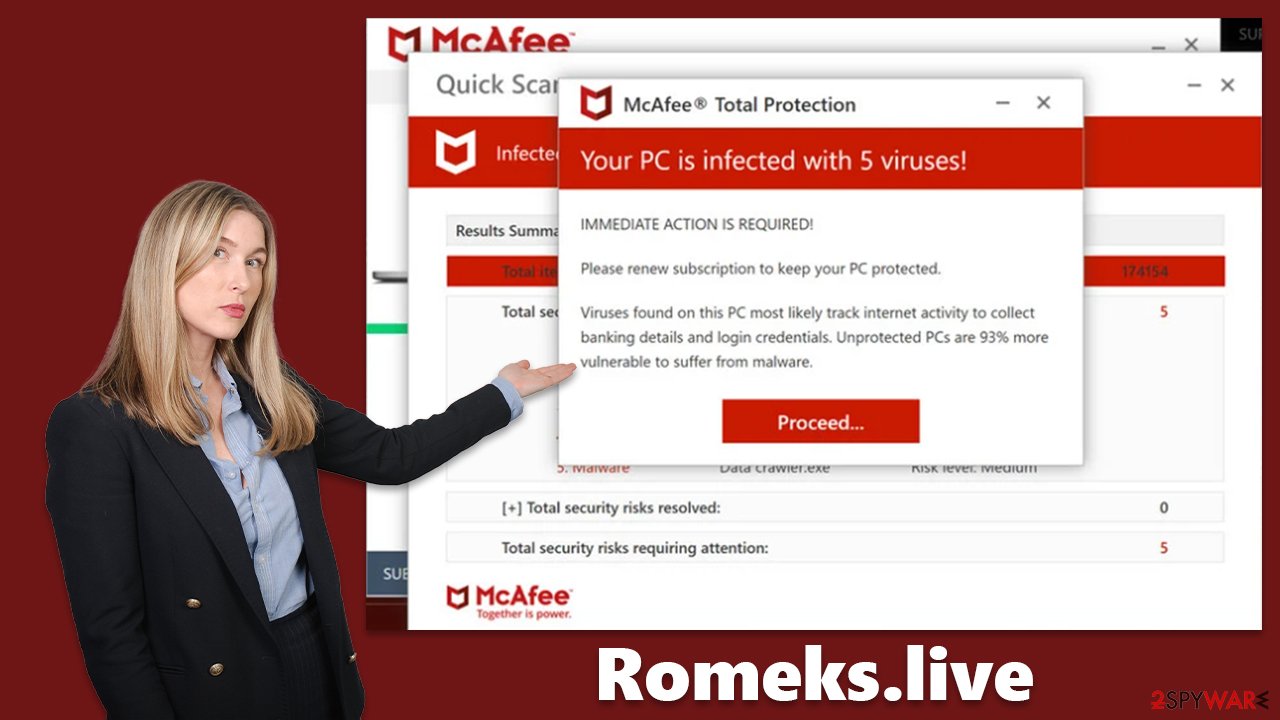
Upon entering the website, users are frequently caught off guard by what they encounter: several windows are displayed, resembling a system scan conducted by McAfee, a well-known and respected security vendor. In just a matter of seconds, users are confronted with a daunting reality – their system is apparently plagued with numerous viruses, and in order to eliminate them, they are prompted to renew their subscription. Here's the message you could expect after entering the Romeks.live scam site:
Your PC is infected with 5 viruses!
IMMEDIATE ACTION REQUIRED!Please renew subscription to keep your PC protected.
Viruses found on this PC most likelt track internet activity to collect baking details and login credentials. Unprotected PCs are 93% more vulnerable to suffer from malware.
However, this is just a ploy to deceive users into purchasing their software. The website is designed to mimic McAfee's interface to make it appear more convincing and legitimate. The scam is aimed at exploiting users' concerns about their computer's security, often preying on their lack of technical knowledge and the desire to keep their systems safe. Legitimate security vendors would never use scare tactics to intimidate users.
Unfortunately, this type of scam is becoming increasingly common. Users must remain vigilant while browsing the internet and ensure that they only purchase security software from reputable vendors. In case of doubt, it is always advisable to do some research and read reviews before making a purchase to avoid falling victim to these fraudulent tactics.
Check your system for adware
To remediate the effects of encountering the malicious Romeks.live website, the first step is to conduct an adware check. The most efficient and hassle-free approach to ensure the system's freedom from adware is to conduct a full system scan with trusted security software such as SpyHunter 5Combo Cleaner or Malwarebytes. This will enable users to swiftly and easily eliminate all malicious components simultaneously.
While manually removing unwanted programs is possible, automatic removal is simpler and quicker. Additionally, removing useful programs may cause more harm than good. Once the device is confirmed to be free of malware and adware, it is essential to promptly clear the browser of cookies and other tracking elements. Users can employ FortectIntego for this task or follow the instructions below to accomplish it manually:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

It is essential to be aware that if you were redirected to another malicious website and provided any personal information, such as passwords, account details, or other sensitive information, your contact data may have been passed on to cybercriminals. This information can be used to target you with phishing emails, phone calls, or other forms of social engineering attacks.
These types of attacks often attempt to deceive users into disclosing additional personal information or downloading malicious software. Thus, it is critical to exercise caution when receiving unexpected emails or phone calls from unknown sources and never provide personal information unless you are certain of the legitimacy of the request.
Furthermore, it is vital to track all your accounts and monitor them for any suspicious activity regularly. Cybercriminals can use the personal information they have acquired to gain access to your accounts, leading to identity theft or financial loss.
Take care of push notifications
Romeks.live doesn't only ask you to go purchase software you might not even need, but it may also request to enable push notifications right after you enter the site.
While many users would avoid engaging with the request, there are some who may accidentally click the “Allow” button. This mistake can result in intrusive pop-ups appearing on their desktops, displaying inappropriate or misleading content that may even contain malicious links.
Interacting with these notifications can be dangerous and compromise your device's security and safety. Therefore, it is crucial to take immediate action to stop these unwanted ads from appearing on your device.
To do this, it is recommended to follow the instructions below carefully. These steps will help you remove any unwanted notifications and protect your device from further harm.
Google Chrome
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.

Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the URL's drop-down menu.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.

Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.

MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.

- Click on More actions and select Block.
How to prevent from getting adware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
