RPC ransomware (virus) - Free Guide
RPC virus Removal Guide
What is RPC ransomware?
RPC ransomware is a type of malicious software designed to cause maximum damage to victims
RPC is a type of malicious computer virus that gains access to a Windows computer illegitimately (for example, via software cracks or malicious spam emails), and then encrypts all files on the system. This includes all personal files, such as pictures, documents, videos, etc. For the process to be effective, a sophisticated encryption algorithm, such as AES, RSA,[1] or DES (or a combination of those) is used – it guarantees that there's no easy way to restore files without applying a unique decryption key, which is only accessible to the attackers.
Malware's main goal is to blackmail users into paying a ransom in bitcoin[2] in exchange for the decryption software. To convey that to victims, RPC ransomware delivers a pop-up window and a text file recinfo.txt, which also includes contact details of cybercriminals – emails pcrec@tuta.io and pcrec@cock.li.
However, we do not recommend communicating with the attackers, as they may never keep their promises, resulting in you losing money along with your files. Instead, follow the instructions below: we explain how to get rid of the virus correctly and then attempt to restore files without using cybercriminals' help.
| Name | RPC virus |
|---|---|
| Type | Ransomware, file-locking malware, cryptovirus |
| Family | Dharma |
| File extension | .RPC, appended to every personal file on the system |
| Ransom note | recinfo.txt and a pop-up window |
| Contact | pcrec@tuta.io and pcrec@cock.li |
| Data Recovery | If no backups are available, recovering data is almost impossible. However, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | Manual virus removal is not recommended, as it might be difficult for regular users. Instead, SpyHunter 5Combo Cleaner or other anti-malware tools should be used |
| System fix | Malware can seriously impact a Windows computer's performance and stability after it is removed. We recommend scanning the system with FortectIntego to remedy it and avoid significant stability issues |
Ransom note
RPC ransomware belongs to a malware family known as Dharma, which has been around for many years now. Versions like Rar, bDAT, or Ash are just a few examples of this malware strain, and they differ little in terms of their functionality – the main goal is to extort money from innocent victims.
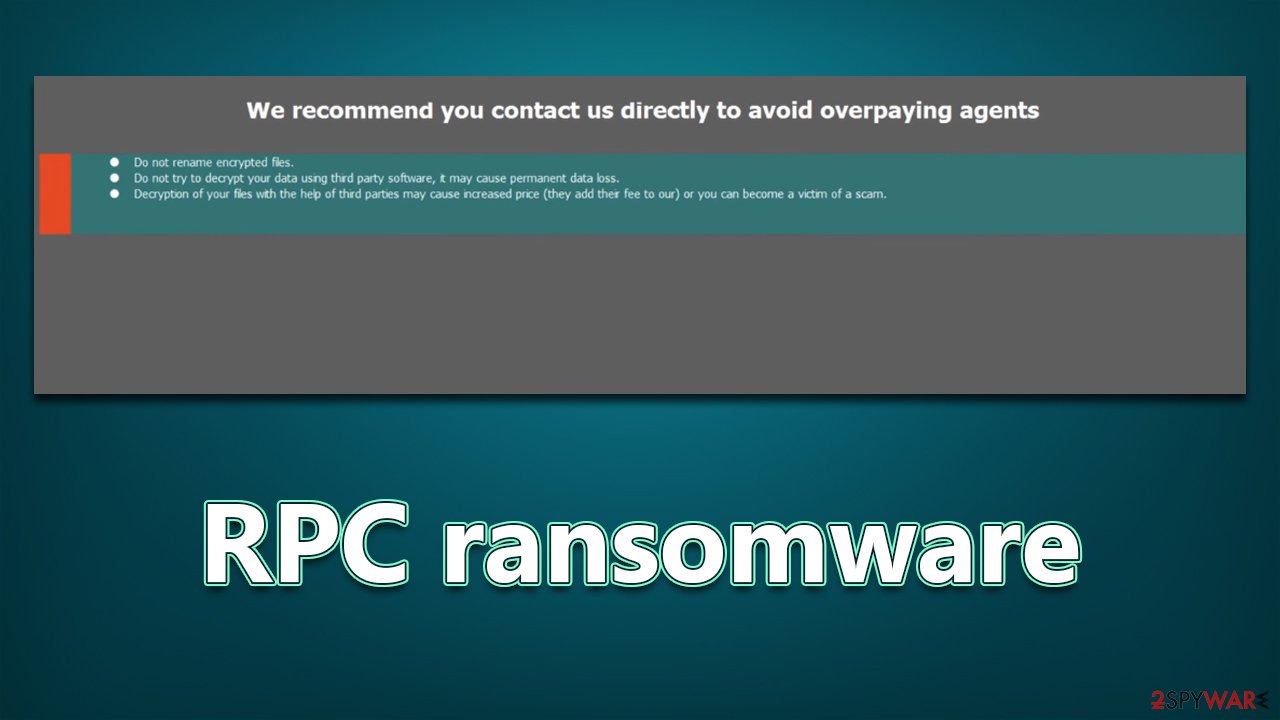
Upon execution, the RPC virus would deliver a ransom note that would serve as a message from the perpetrators. It soon becomes evident that they are not willing to restore users' files for free, as they claim in the pop-up message, which reads:
FILES ENCRYPTED
Don't worry, you can return all your files!
If you want to restore them, write to the mail: pcrec@tuta.io YOUR ID
If you have not answered by mail within 12 hours, write to us by another mail:pcrec@cock.li
ATTENTION
We recommend you contact us directly to avoid overpaying agents
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
The text message can also be viewed by opening it, and it includes a shorter version of the above information:
all your data has been locked us
You want to return?
write email pcrec@tuta.io or pcrec@cock.li
Contacting cybercriminals may be one of the biggest mistakes to make, as they will try to convince you that paying the ransom is the best solution you have. However, we do not recommend trusting cybercriminals, as it is in their best interest to make you pay. It only proves that their illegal schemes work as intended – they may not even deliver a decryptor that would actually work.
1. Perform malware removal correctly
Most people who get infected with ransomware are new to the experience, which unfortunately means they know little about the infection or how to handle it. In fact, performing the steps in the correct order is imperative to avoid further damage to the encrypted files of the operating system.
How those affected by ransomware proceed could also affect their chances of being able to recover their data, so it's crucial how they do it. The users must disconnect their computers from the network and the internet as soon as possible so that the attackers cannot issue commands to the malware via the Command & Control[3] server.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
Ransomware doesn't always stay after it's done encrypting your files- sometimes it leaves as soon as it's finished the job. However, that isn't always the case since ransomware is often bundled with other malware which may continue stealing personal information or deliver additional payloads. Therefore, to be sure you are protected, download and install SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable security software and perform a full system scan.
In some rare cases, the RPC virus may start tampering with the removal process and interfere with the anti-malware job. If that is the case, you can always access Safe Mode, where the virus would be temporarily disabled – this would allow you to tackle the infection easier. Here's how to access the mode:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
2. Attempt to restore data
Many users believe that any encrypted files will be restored after their computer has been scanned by security software. That isn't the case, though, because data encryption is typically permanent—at least up until a special key is used. Additionally, it is false to think that the files are corrupted or damaged because encryption does not actually harm files.
Additionally, contacting criminals is not a good idea. As an alternative, there are other methods that might help you get back at least some of the lost data. Before moving forward, make sure to create a backup of the encrypted files because doing so could make them useless.
Additionally, contacting criminals is not a good idea. As an alternative, there are other methods that can help you get back at least some of the lost data. Before moving forward, make sure to create a backup of the encrypted files because doing so could make them useless.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

There are hundreds of security companies and organizations battling ransomware creators. In some cases, servers containing decryption keys have been seized, which allows the keys to be released to the public. Below you will find the most prominent parties involved in free data decryption services; these services have already helped millions of victims worldwide. Please keep in mind that an alternative decrytpion tool might take a while to create (if possible).
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

3. Fix damaged system files
When a computer's operating system is corrupted with malware, it will need to be changed. For example, damage to bootup or other registry components by an infection, or the destruction of important DLL files can cause problems with performance and stability for users. Antivirus software cannot fix these types of issues, and in some cases, Windows may need to be reinstalled entirely.
We recommend scanning your computer with PC repair software to find any damaged files and repairing them all at the same time. The tool can also clear your computer of junk files and third-party trackers, as well as help with a variety of technical issues that have nothing to do with malware threats.
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Ron Franklin. AES vs. RSA Encryption: What Are the Differences?. Precisely. Data security.
- ^ What is Bitcoin? How to Mine, Buy, and Use It. Investopedia. Source of financial content on the web.
- ^ Command and Control [C&C] Server. Trend Micro. Security blog.
