Salma ransomware (virus) - Free Instructions
Salma virus Removal Guide
What is Salma ransomware?
Salma ransomware prevents access to your personal files to extort money from you
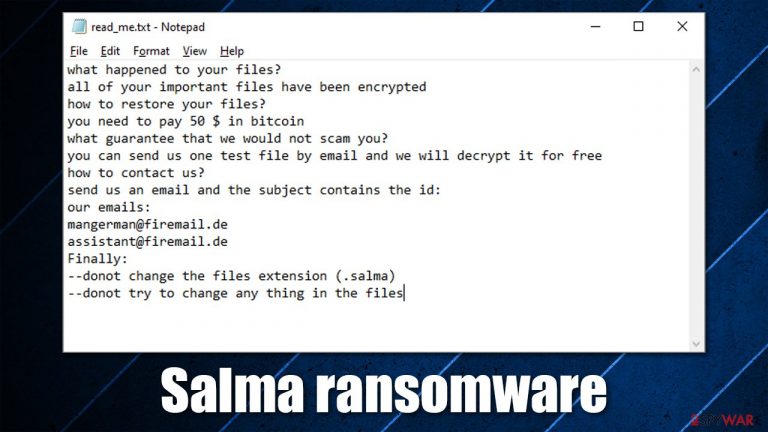
If your files have suddenly lost their regular icons and been appended with the .salma extension, your computer has been infected with ransomware. Ransomware is one of the most devastating malware infections among PC users, as its aftermath can result in a full loss of personal data that was located on the computer during the attack.
Salma virus uses a combination of sophisticated encryption algorithms AES and RSA[1] to lock pictures, videos, documents, databases, and other files located on a Windows computer. As soon as the data-locking process is complete, malware puts a ransom note titled read_me.txt into each of the folders where encrypted files are located, as well as the desktop. This ensures that victims can access the information about what happened to them rather quickly.
Inside the file, there is a message from the cybercriminals behind the virus. According to it, users are meant to send an email to mangerman@firemail.de or assistant@firemail.de and pay $50-worth of Bitcoin in order to receive the decryption tool and restore files back to normal.
| Name | Salma ransomware |
|---|---|
| Type | Cryptovirus, ransomware |
| Encryption method | AES + RSA |
| File extension | .salma |
| Ransom note | read_me.txt |
| Contact | mangerman@firemail.de and assistant@firemail.de |
| Ransom demand | $50 to be delivered as bitcoin to a specified Bitcoin wallet |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | Perform a full system scan with powerful security software, such as SpyHunter 5Combo Cleaner |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
A ransom note is the first communication line between the attackers and victims. Almost all file locking malware delivers this note as soon as the encryption of files is complete. In rare cases, the note might be missing due to poor coding or a bug; some ransomware is also used to destroy files, hence no note is sent.
Usually, the main goal of threat actors is not to somehow damage your computer or steal sensitive information (although there are plenty of examples where ransomware includes additional modules that are perfectly capable of additional actions).[2] Therefore, delivering the contact information of criminals and the ransom demands is imperative to the success of the illegal business of ransomware.
The full message of the ransom note reads:
what happened to your files?
all of your important files have been encrypted
how to restore your files?
you need to pay 50 $ in bitcoin
what guarantee that we would not scam you?
you can send us one test file by email and we will decrypt it for free
how to contact us?
send us an email and the subject contains the id: XXXXXXXXXXXXXXXXXX
our emails:
mangerman@firemail.de
assistant@firemail.de
Finally:
–donot change the files extension (.salma)
–donot try to change any thing in the files
Hackers are asking for your personal ID to recognize your computer and separate it from others. This is because each of the infected machines receives a unique key to prevent users from sharing it. Likewise, running anti-malware software will not restore .salma files. This is one of the reasons why ransomware is so destructive.
As it is typical, threat actors also offer test decryption services in order to convince users to pay – it simply serves as proof that they indeed have a working decryptor, and all you have to do is pay the money. That being said, keep in mind that cybercriminals are not your friends, and they are not obligated to do anything positive (they already broke into your machine and locked all files without asking).
There have been plenty of events where victims paid ransoms and never received the decryption tool. Besides, this malware strain is relatively new, hence it is difficult to know whether cybercriminals can keep their promises. This is why you should refrain from paying and only use it as an absolute last option.
Instead, we recommend you remove malware with SpyHunter 5Combo Cleaner or another reputable anti-malware and then fix damaged system files with the help of FortectIntego. We also provide alternative file recovery methods below.
How ransomware got into your computer
Salma virus is a threat that was spotted in mid-August 2021. So far, security experts did not manage to find any similarities to any other prominent ransomware families such as Dharma. The limited number of victims also prevents a more detailed examination of malware.
Nonetheless, the malicious file that belongs to ransomware (ConsoleApplication1.exe)[3] was found on Github under the “school design.gz” file, which suggests that it could be spread through the site by using outside phishing links. According to some victims, they received suspicious links in the Discord app, which lead them to the malicious file download page.[4]
Besides this, many other ways could be used for ransomware distribution, including:
- Spam email attachments and hyperlinks;
- Software vulnerabilities;
- Hacked or malicious websites;
- Fake updates;
- Software cracks and pirated program installers, etc.
In order to protect yourself from ransomware attacks, you should always rely on powerful security software and be extra careful when browsing the web, clicking links on social media, opening emails, or downloading software.
Step 1. Remove ransomware efficiently
As we already explained, scanning your computer with anti-malware will not restore your files – they will remain locked. This is because ransomware infection and data encryption are two independent processes, although the latter would not be possible without the former.
Likewise, it is important to remove Salma ransomware from your system first. Otherwise, the encryption process could be applied to all your incoming files, and even if you manage to restore some of them, they would be encrypted right away.
To do that, you need to scan your device with anti-malware software. If malware is tampering with its operation or you are unable to launch it, access Safe Mode with Networking and perform the scan from there:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

Once you reach Safe Mode, launch SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable antivirus, update it with the latest definitions and perform a full system scan to eradicate malware and all its malicious components.
Tip 2. Restore your files without paying the attackers
Indeed, $50 might not seem like much (depending on where you live), especially if you have important data on your computer. However, this does not guarantee that you will retrieve the needed decryptor. Paying criminals only motivates them to proceed with their malicious actions and proves to them that the illegal scheme works as intended.
If you already removed ransomware by scanning your device with security software, you should now make some backups of your locked files. If you try to restore them without making copies, they could get permanently corrupted; simply use a USB flash or another storage device (cloud storage can also work).
Once that is done, you can look for decryption software provided by third parties and security experts. Lists are updated constantly, so never give up the search. Keep in mind that creating a working tool that would restore your files for free is not always possible, although bugs within the code of ransomware allow breaching it.
Here are a few links that could help you find encryption software:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors
Also, you could try using third-party data recovery tools. These do not always work for ransomware-affected files, but it might be possible to recover at least a portion of data.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ AES and RSA Encryption. Boxcryptor. Cloud encryption services.
- ^ Nearly 40% of new ransomware families use both data encryption and data theft in attacks. Help Net Security. Information Security News.
- ^ ConsoleApplication1.exe. Virus Total. File and URL analysis.
- ^ Amigo-A. A new #Salma #Ransomware. Twitter. Social network.
