Search.remakovell.com (Removal Guide) - Free Instructions
Search.remakovell.com Removal Guide
What is Search.remakovell.com?
Search.remakovell.com is a browser hijacker that takes over Safari, Google Chrome, or other browsers installed on Mac operating systems
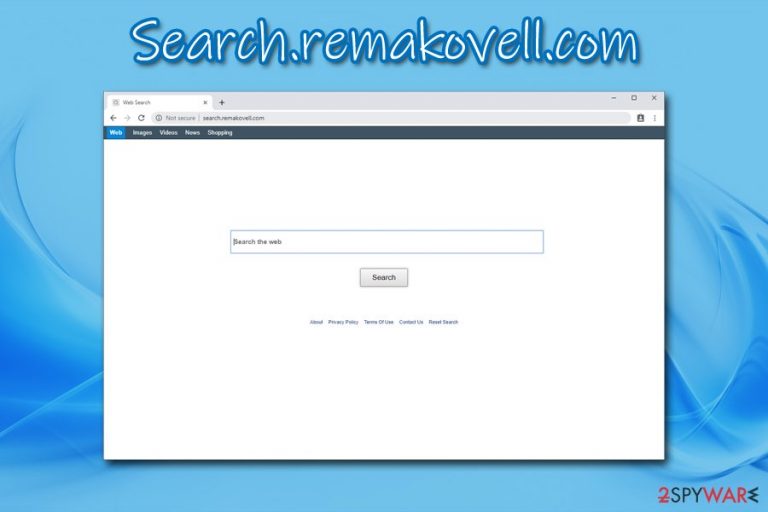
Search.remakovell.com is a webpage that users might unexpectedly see as their homepage after the installation of a third-party application (usually Remakovell). This is because potentially unwanted programs are spread with the help of software bundling – a questionable marketing technique that allows freeware developers to mask optional components within the software installation packages. Thus, users rarely notice how the unwanted application entered their computers, although changes to Safari, Google Chrome, Mozilla Firefox are visible immediately.
As soon as Search.remakovell.com hijack[1] occurs, the user browsers' search engine is replaced with a customized one, and the functionality of the new tab is altered. While users still can reach the most commonly used search providers like Google.com, their homepage always redirects them to hxxps://search.remakovell.com. Unfortunately, some people do not pay attention to the change and start internet browsing activities without taking any actions to remove Search.remakovell.com from their Macs.
| Name | Search.remakovell.com |
| Type | Browser hijacker, potentially unwanted program |
| Associated browser extension | Remakovell |
| Targeted systems | macOS/Mac OS X |
| Infiltration | Browser hijackers are usually installed together with other programs downloaded from third-party sites; users may also install the PUP after seeing an attractive advertisement on some website |
| Symptoms | The homepage, new tab, and search engine of the web browser is altered, increased amount of ads, redirects to unknown sites, etc. |
| Risk factors | While browser hijackers are not dangerous on their own, they might help to create circumstances where users might end up installing other unwanted software or even malware, or provide details to unknown parties (potentially cybercriminals) |
| Termination | To get rid of the hijacker, scan your Mac with anti-malware software like FortectIntego or make use of our manual removal guide below |
While, mostly, browser hijackers are not considered to be a major security risk, they should still not be ignored. Upon installation, these unwanted programs usually initiate changes to browsers that are unsolicited. Luckily, most of the modern browsers now warn about these modifications, so users might decline them in the first place. However, this is not the end of Search.remakovell.com removal.
Even though all the Remakovell searchers are directed to Yahoo, the top results are always covered with sponsored links. Besides, the affected will most likely see an increased amount of all types of ads on all the sites that they visit. The commercial activity is also accompanied by user browser habit monitoring, which allows the PUP developers to monetize on targeted advertisements.
In most of the cases, users infected with Search.remakovell.com browser hijacker will not experience major changes to their operating systems, the way they browse will change. And, while the sponsored links are usually harmless, the chain of clicks may lead them to phishing, tech support scam, or even malware-laden websites. In such a way, users might infect their computers with a Trojan or other virus, disclose sensitive information to unknown parties, or lose money after being tricked into subscribing to some useless service.
Besides, Search.remakovell.com does not provide any details regarding users' privacy or the terms and conditions for using the application. Nevertheless, most of the PUPs track users and collect the following data (which sometimes might include personal information):
- IP address;
- Technical information of the device used;
- Browser cookies;
- Links clicked;
- Search queries;
- Sites visited;
- Bookmarks added;
- Installed applications, etc.
If you frequently download apps from third-party sites and noticed that Search.remakovell.com taken over your browser, you should scan your computer with anti-malware software – we suggest using FortectIntego. Be aware that genuinely malicious software would usually show no signs and symptoms of infections.
Software bundling is the most probable cause for PUA infection
Mac users were ignoring online safety for a while, claiming that “Macs cannot get infected.” While a virus infection is practically impossible (it needs to be able to spread laterally while attaching itself to other applications), Mac malware has been on the rise for many years now, and potentially unwanted programs are one of the biggest problems that macOS users encounter nowadays.
The vast majority of infections occur when users act carelessly – download pirated software, visit high-risk sites, fall victim of fake updates,[2] etc. All these infection methods are also applied to adware and browser hijackers, as they are mostly spread through software packages as an optional component.
Thus, experts[3] advise users to be careful online:
- When possible, download software from App Store or other official sources;
- Before installing an unknown app, read up on it online – reviews and forum posts are good indicators if the program can be trusted;
- Always opt for Advanced/Custom installation mode;
- Check if Terms and Conditions and Privacy Policy is provided;
- Decline all the deals or offers;
- Pay attention to small print text;
- Remove all the marks from pre-ticked boxes.
Get rid of the PUP and reset your browsers to revert changes made by Search.remakovell.com
Search.remakovell.com removal should not be complicated, generally speaking. As we previously mentioned, browser hijackers are considered to be minor threats and usually are relatively easy to eliminate. In most of the cases, simply moving the app into Trash is enough, as well as getting rid of the extension embedded into the web browser. For more details instructions, please check the instructions below.
Nevertheless, it is also possible that your machine has more than one PUP installed on it. In such a case, you should remove Search.remakovell.com along with all the other unwanted software using anti-malware software. Security software can locate and get rid of all the hijacker components automatically. Besides, checking your system with an anti-malware application is always a good idea to make sure no stealthy malware is hidden on your Mac.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Search.remakovell.com. Follow these steps
Delete from macOS
To remove Search.remakovell.com components from your macOS/Mac OS X, perform the following actions:
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
Browser hijackers change the settings of the installed web browsers. Therefore, refresh Mozilla Firefox in order to revert the settings changed by the hijacker
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Delete from Safari
Safari still might suffer from unwanted behavior until its reset is performed:
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Search.remakovell.com registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting browser hijacker
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Browser hijacking. Wikipedia. The Free Encyclopedia.
- ^ Ben Lovejoy. PSA: There’s a new fake Flash Player installer for Macs, and it’s nastier than usual. 9to5Mac. Apple News & Mac Rumors Breaking All Day.
- ^ NoVirus. NoVirus. Cybersecurity advice from the UK.
