Search.surfharvest.xyz browser hijacker (Free Instructions) - Chrome, Firefox, IE, Edge
Search.surfharvest.xyz browser hijacker Removal Guide
What is Search.surfharvest.xyz browser hijacker?
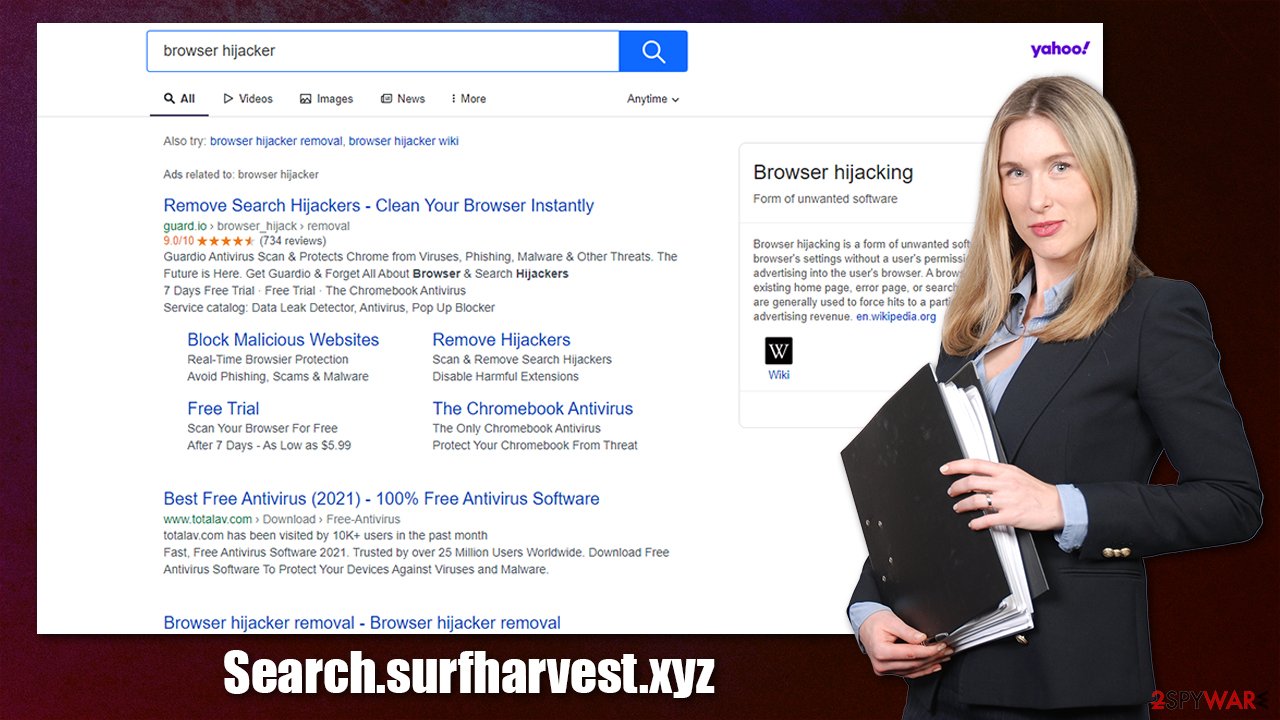
Search.surfharvest.xyz is a browser hijacker that replaces genuine search results with ads
If you have noticed that your homepage is changed to Search.surfharvest.xyz web address, you have a browser hijacker installed on your device, which is likely to be an extension for Google Chrome, Mozilla Firefox, MS Edge, or another compatible browser. Once installed, the app also replaces the search bar with its own, which can redirect results to a different provider and insert ads and sponsored links at the top of the search results.
Clicks on ads is one of the main monetization methods for browser hijacker authors, hence those infected might experience the intrusive ad activity more often than not. The results produced by the app should not be trusted, as they might be inaccurate or misleading.
Due to this, some users might be led to insecure websites and be tricked into installing other potentially unwanted programs or even malware.[1] All in all, you see suspicious changes to your browser, you should never ignore them and investigate immediately. In this article, we will explain how to do that in the most efficient way.
| Name | Search.surfharvest.xyz |
|---|---|
| Type | Browser hijacker |
| Distribution | Software bundle packages, deceptive ads, fake update prompts |
| Symptoms | A new extension is installed on the browser; homepage and new tab address are swapped to the hijacker's URL; a customized search engine is appended to the homepage; search results are filled with sponsored links and ads |
| Risks | Users are more likely to be exposed to links that offer to download suspicious software; data tracking can be a risk to privacy |
| Elimination | You can uninstall potentially unwanted programs by following the manual guide below or by scanning the computer with powerful anti-malware |
| Additional steps | Cleaning web browsers can stop tracking activities and ensure that ads do not return. FortectIntego can be used to do that automatically |
More about browser hijackers
Browser hijackers have a very long history behind them. At some point in internet history, they even used to be dubbed spyware due to inadequate data gathering practices and persistence mechanists they would establish upon installation. Due to various important security regulations from tech giants such as Google or Microsoft and various law enforcement agencies, applications are now much more regulated and branded appropriately.
Today, most browser hijackers are not malicious per se, although they have plenty of undesirable/suspicious features that rarely anyone would be fond of. Let's dive into more details about how these potentially unwanted programs operate.
Distribution
As evident, most people who are at least a little familiar with PUPs would not install them on purpose. However, it is sometimes difficult to tell whether an application is useful, especially when the developers present the functionality as something that does not actually exist.
To spread their creations, developers of potentially unwanted programs commonly rely on rather deceptive distribution techniques, software bundling[2] being the most common one. While initially, this distribution method has no evil intent, some installers are designed to hide optional components within it.
For example, users who rush through the installation steps of freeware might not notice the following message next to a checkbox that is pre-ticked:
By pressing “Next”, you agree to install XXX on your computer.
Thus, be very attentive when installing software from third-party websites – always read through the installation instructions carefully, pick Advanced/Custom mode if prompted, watch out for pre-ticked checkboxes and misleading button placements for the offers.
Another popular method to spread hijackers is to advertise them on various shady websites. For example, you might encounter a scam website that tells you that your privacy is in danger and that you need to install a VPN program to protect it. While there is some truth in this statement (legitimate VPNs such as Private Internet Access could surely help your anonymity and prevent some cyberattacks),[3] no legitimate service provider would advertise their products in such a deceptive way.
Therefore, if you find warnings that something is missing, some software needs to be updated, or that your system is infected with a virus, straight out ignore these messages and never download offered software.
Operation
By no means are browser hijackers as malicious as Trojans or ransomware, although their presence should definitely be ignored – especially if they showed up on your browser seemingly out of nowhere. This might also be an indication that there are other potentially unwanted programs installed on your system, and you should be concerned.
Search.surfharvest.xyz is a typical browser hijacker that changes the settings of a browser in order to take over users' online activities. For example, search results are commonly redirected to a different provider, such as Yahoo, and then also filtered accordingly. The top results are never genuine but instead littered with ads, which can be easily confused with legitimate links.
While most links are relatively secure, some of them might be misleading. It is not recommended to click on ads and exploring pages promoted by the hijacker, as it does not have any responsibility for the damages that such links may cause. Combine this with background data tracking in order to profit from
To make matters worse, hijackers rarely produce anything useful when it comes to their functionality. The developers often claim that they “improve search results,” but these alleged improvements are nothing but ads.
Remove unwanted browser extensions
Previously, potentially unwanted applications such as Wajam were installed on the system level (hence were difficult to eliminate). In the past decade, many application developers shifted to browser extensions, as they are much easier to produce and maintain. In fact, some PUP authors simply rebrand the same extension and release it as something new, hence increasing the chances of users installing it, all while avoiding detection by security software – MovieSearchOnline and ClickPDFSearch are great examples of such practice.
If installed as an extension, Search.surfharvest.xyz removal can be performed via browser settings. Below you will find all the details needed to perform elimination on all modern browsers.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
MS Edge (legacy)
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.
![Remove extensions from Edge Remove extensions from Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Keep in mind that the name of the extension might not always match the URL that you see once you open your browser. However, you should look for an app under the name of Surf Harvest or something similar – remove it immediately. Also, you should check if there are additional unknown add-ons installed and remove them at once.
Clean your browser accordingly and check for other PUPs
If you have followed the steps in the previous section of the article, you should have successfully uninstalled the browser hijacker from your browser. However, there are instances when not everything is so straightforward, and people run into difficulties when trying to get rid of potentially unwanted programs from their systems.
One of the best examples is how recently browser hijacker creators started implementing the “Managed by your organization” feature on users' browsers, which prevents them from removing the extension. This behavior is rather malicious and should be treated as such.
If such is the case, you could run a full system scan with powerful security software, for example, SpyHunter 5Combo Cleaner or Malwarebytes. Keep in mind that it can not only remove malicious, invisible components from your system but also prevent their entrance in the future. It is important to keep your security software updated and have it running at all times.
Additionally, we recommend using FortectIntego to clean your browsers thoroughly – this would prevent third parties from tracking you, improving your online privacy, and sometimes can be beneficial for PUP removal as well. If you rather opt for the manual option, follow these steps:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.
![Clear Edge browsing data Clear Edge browsing data]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Getting rid of Search.surfharvest.xyz browser hijacker. Follow these steps
Uninstall from Windows
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

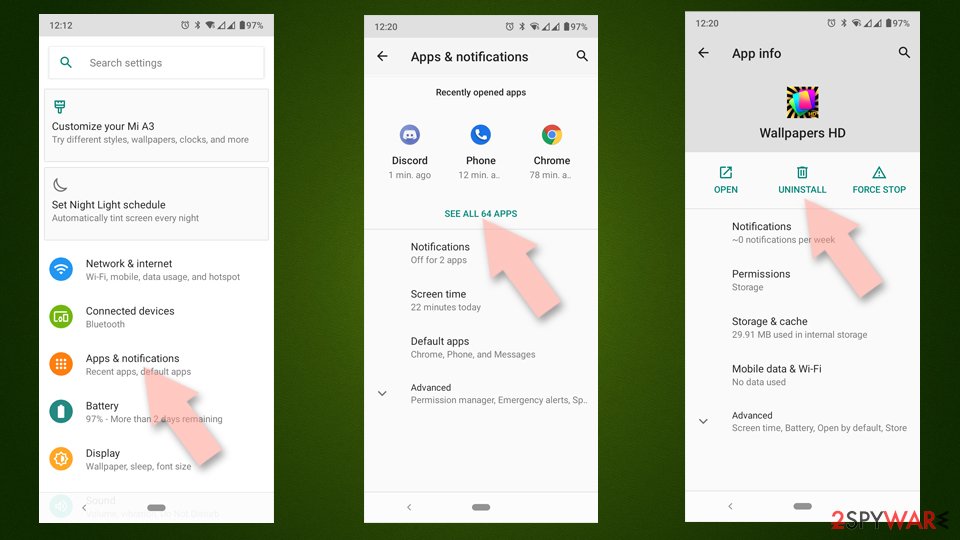
Uninstall from Android
Uninstall unwanted programs from Android device:
- Go to Settings -> Apps/Applications.
- Expand the full list of the installed apps.
- Scroll through the list and tap on a suspicious application once.
- Tap on it and select Uninstall.

- Reboot the device.
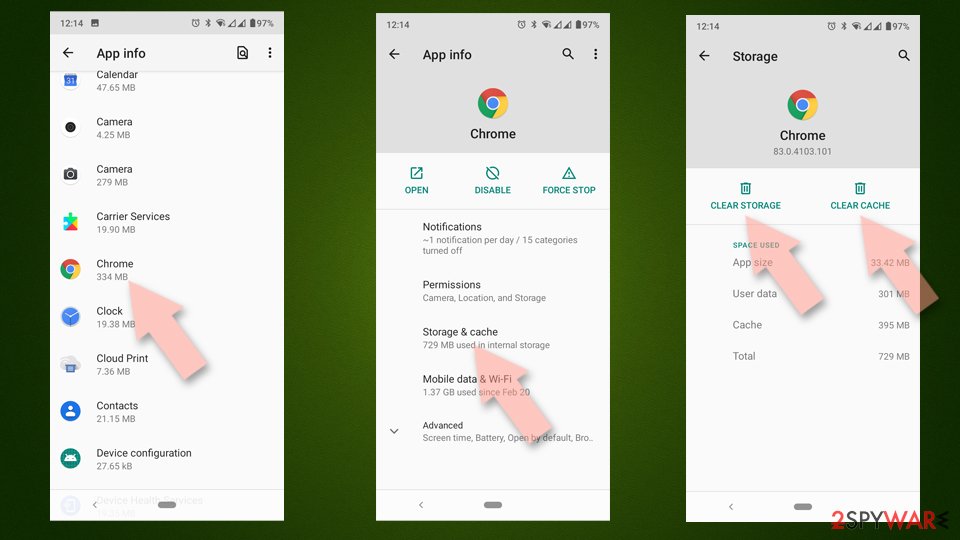
Clear Storage and data files on Android from Google Chrome or other apps:
- Go to Settings > Apps/Applications.
- Expand the full list of the installed apps.
- Tap on Chrome and select Storage & cache.
- Clear storage and clear cache of the app.

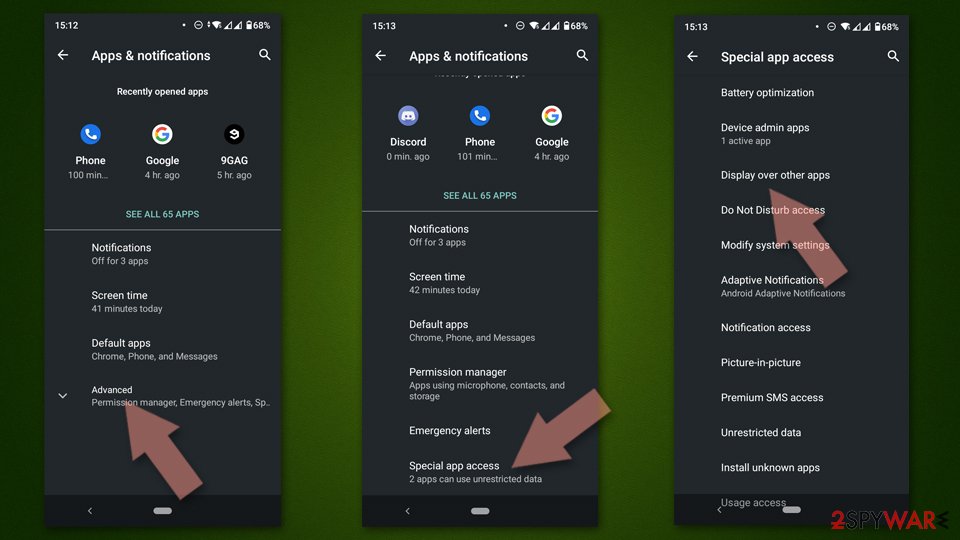
If you are seeing ads on top of other apps but are not sure what is causing it, perform the following steps:
- Go to Apps/Applications.
- Tap Advanced.
- Select Special App access.
- Tap on Display over other apps.

- Eliminate apps with these access rights enabled.
How to prevent from getting browser hijacker
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ What is malware?. Myra Security. German technology manufacturer.
- ^ Bundled Software. Techopedia. Professional IT insight.
- ^ Max Eddy. What Is a VPN, and Why You Need One. PC Mag. The Latest Technology Product Reviews, News, Tips.