Search1.me browser hijacker (virus) - Free Guide
Search1.me browser hijacker Removal Guide
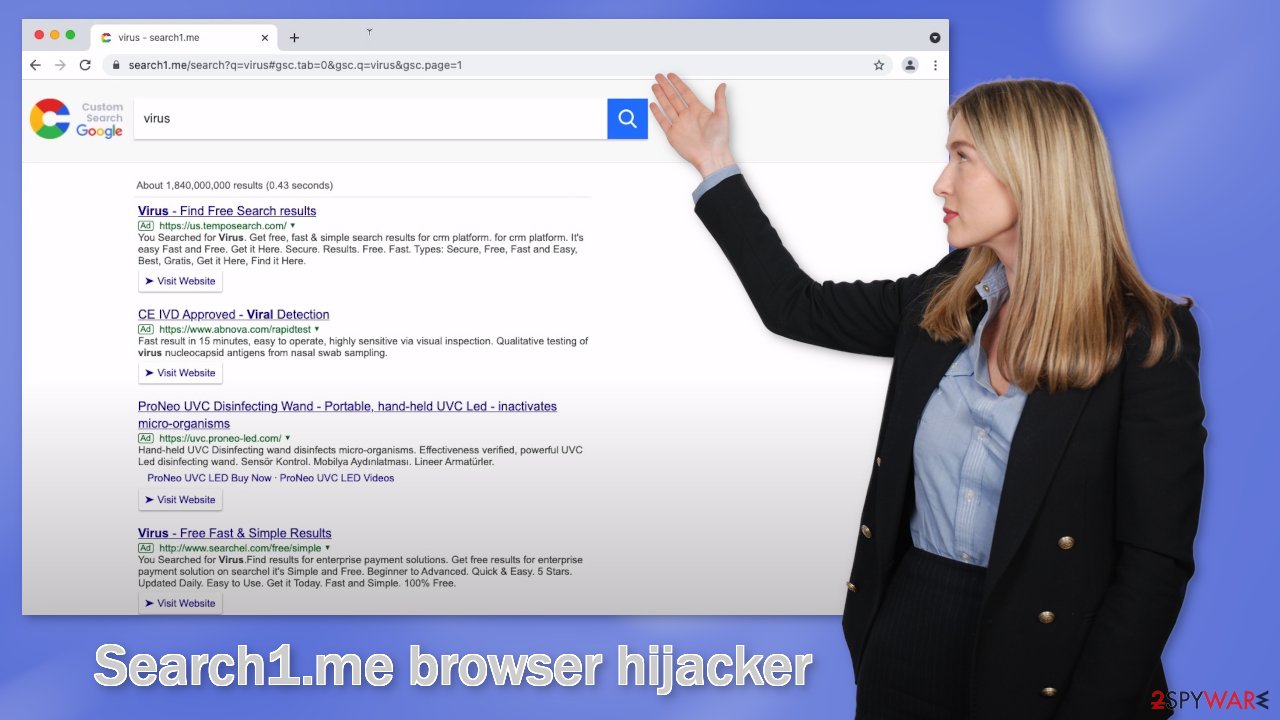
What is Search1.me browser hijacker?
Search1.me adds a fake search engine and changes the homepage to monetize user activity

Search1.me is a browser hijacker that changes the main settings, like the homepage, new tab address, and search engine. Users are forced to use only selected channels for browsing which raises many user privacy and security concerns. Such apps can also read all the browsing history and track user activity.
Normally, browser plugins are meant to provide some kind of benefits that are not available on a default browser. People love add-ons that can block ads or automatically apply coupon codes for the biggest discounts while shopping online. However, downloading plugins from unsafe websites or not doing enough research can introduce problems.
Browser hijackers can lead to dangerous websites that use social engineering to trick people into providing personal information or downloading PUPs (potentially unwanted programs)[1] and malware. The extension can also generate commercial content from rogue advertising networks that lure people into scam sites.
In the past few years, we have seen a rise in hijackers as people download plugins carelessly, sometimes multiple add-ons at once, to test which one is better. Because the settings change seemingly out of nowhere, many think that they have been infected with a virus.
| NAME | Search1.me |
| TYPE | Browser hijacker; potentially unwanted program |
| SYMPTOMS | The main settings of the browser get changed, like the homepage, new tab address, and search engine |
| DISTRIBUTION | Shady websites, deceptive ads, software bundling |
| DANGERS | The extension may lead to dangerous websites; display misinformation, inaccurate search results; track browsing activities |
| ELIMINATION | Remove the extension by going to your browser settings |
| FURTHER STEPS | Use FortectIntego to fix any remaining damage and optimize the machine |
Distribution methods
Usually, people get infected with bogus extensions by browsing through shady websites that engage in illegal activities. They are full of deceptive ads, and sneaky redirects because they are unregulated. People can get redirected to sites that promote browser hijackers and get fooled into downloading them.
Often fraudsters try to make the extensions as attractive as possible by stating that they were created in collaboration with big tech companies like Google. You may also encounter messages like “Recommended by Chrome.” Such statements should not be trusted as they are only used to make the product look legitimate.
It is best to only use official web stores, as they are the safest place you can get add-ons from. Extensions that get listed, go through a lengthy review process, however, you should still do your research. Read the reviews, look at the ratings and how many users they have. It is best to choose extensions that are popular, and have plenty of feedback.
Another way your browser could have been hijacked is by a PUP. Such applications usually get installed from freeware distribution sites that use software bundling[2] to generate revenue. The problem is that often they include programs that are unsafe and can start causing unwanted behavior on the machine.
You should be careful about what you let into your digital bubble as that can have detrimental results. One wrong click and you can be in a lot of trouble. It is important to install software that you fully trust as fraudsters take advantage of every possible opportunity to monetize your activity.
Cookies[3] are used to track your browsing behavior – your IP address, geolocation, websites you visit, links you click on, and things you purchase online. This information can later be sold to rogue advertising networks and other third parties. That is why security experts recommend clearing cookies and cache regularly.
Unfortunately, a lot of users forget about this task so it is good to have a tool that can do it automatically. FortectIntego can clear cookies and catch with a click of a button, as well as fix various system errors, corrupted files, registry issues, which is especially helpful after a virus infection.
Remove the unwanted extension
You can remove browser add-ons by going to your settings. Find the list of extensions installed in your browser and remove Search1.me. We show how to do that in the guide below:
If you want to avoid PUPs in the future, always choose “Custom” or “Advanced” installation methods, read the privacy policy and terms of use to find out what information will be collected and what the application will be allowed to do in your system. The most important part is to check the file list and untick the boxes next to any items that you think are suspicious or unrelated.
How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Potentially unwanted program. Wikipedia. The Free Encyclopedia.
- ^ Will Dormann. Bundled Software and Attack Surface. Cmu. Carnegie Mellon University Software Engineering Institute Blog.
- ^ What are Cookies?. Kaspersky. Home Security Blog.










