Searchpoweronline.com browser hijacker (Free Guide)
Searchpoweronline.com browser hijacker Removal Guide
What is Searchpoweronline.com browser hijacker?
Searchpoweronline.com is a deceptive application that won't bring any benefits to your browsing
Searchpoweronline.com is a web address you may not expect to see set as the homepage of your browser. If that is the case, it means that you have a potentially unwanted application installed on your system, and it has taken over your browsing sessions. These types of apps usually slip into users' machines without their knowledge via deceptive methods and then make changes to Chrome's or another browser's preferences, appending their own homepage and new tab and altering the search provider as well.
This way, Searchpoweronline.com can promote various advertisements at the top of the search results and elsewhere. Besides, the alternative search provider might not yield the results one is expecting, as each of the engines works differently. In this case, people can expect to see Bing, Yahoo or searchgenieo.com set as providers.
In the meantime, users would have to deal with an increased number of ads and persistent data tracking, which would take place behind their backs. If you have found that your search preferences have changed, you should remove the browser hijacker from your system in order to regain control of your browsing sessions.
| Name | Searchpoweronline.com |
| Type | Browser hijacker, potentially unwanted application |
| Distribution | Bundled software, third-party websites, misleading ads |
| Symptoms | A browser extension or an application installed on the device; homepage and new tab address set to one of the hijacker's; ads and sponsored links in search results and elsewhere; promotion of other PUPs |
| Risks | Data tracking from various third parties, exposure to malicious ads, redirects to phishing sites |
| Removal | Remove the undesirable browser extension by going to your browser's settings. Using SpyHunter 5Combo Cleaner security software to check the system can also ensure that no malware is running in the background |
| Other tips | After removing all potentially unwanted applications, we recommend you employ the FortectIntego utility to clean your web browsers and repair any damaged system files |
Distribution methods explained
As already mentioned, most users find their browsers hijacked unexpectedly, which automatically brings them to the conclusion that they have never installed anything like Searchpoweronline.com. However, it is not the case, as most of the hijackers and other potentially unwanted applications are installed by users themselves, albeit unintentionally in most cases. This is because PUAs do not spread using sophisticated distribution methods (such as Trojans or ransomware),[1] as their developers choose software bundling[2] or deceptive ads for that instead.
Multiple apps can be distributed simultaneously by websites thanks to software bundling when users are deliberately not shown the full list of what the installer holds inside. In order to profit from pay-per-install operations, third-party websites frequently engage in this behavior. Users may end up with unwanted and perhaps dangerous apps on their PCs as a result of this, though.
Therefore, in order to avoid being tricked by this deceptive practice, you should always be vigilant when installing freeware or other software from the internet. Always pick Advanced/Custom settings and remove all ticks from checkmarks, allowing optional apps to be installed. Also, watch out for fine print text, misleading button placements, and similar.
Keep in mind that official websites or stores usually do not engage in bundling tactics, so it is safest to download apps from these locations instead of third-party distributors. Sites that host illegal software should be avoided at all costs, as malware infections can be very likely when using them.
To consequences of having a browser hijacker running on the system
Although Trojans and ransomware are much more dangerous infestations than browser hijackers are, there are still many reasons why they shouldn't be overlooked. Malware infections from browser hijackers are rare to occur. However, the sponsored links at the top may include advertisements for potentially unwanted programs. You are, therefore, more likely to see advertisements for other browser hijackers or adware if you have the PUP installed.
Not only are the advertisements displayed by Searchpoweronline.com hijacker potentially dangerous, but the program is also known for its data-tracking capabilities. Typically, search queries, visited websites, clicked links, timestamps, technical device info., ISP and similar data are collected thanks to cookies, web beacons,[3] pixels, and other tracking technologies automatically. Undoubtedly this might cause some privacy issues, which you should try to avoid.
Once settled on the browser, the hijacker would keep browser settings, all while guiding users through numerous ads, profiting from the activity. The only way to revert these changes is to remove the application that's causing it.
Remove Searchpoweronline.com from your browser
The browser settings are altered because an unwanted application has altered them. In order to revert these changes, you have to find and remove it. In this particular case, you have to access browser settings and search for an extension you don't recognize, removing it at once.
Keep in mind that the name of the app can be literally anything and may not be related to the homepage your browser is set to. If you aren't sure, simply remove all extensions and then re-implement them back one-by-one, seeing which one is causing the issue.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the window's top-right).
- Select Add-ons.
- Here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Internet Explorer
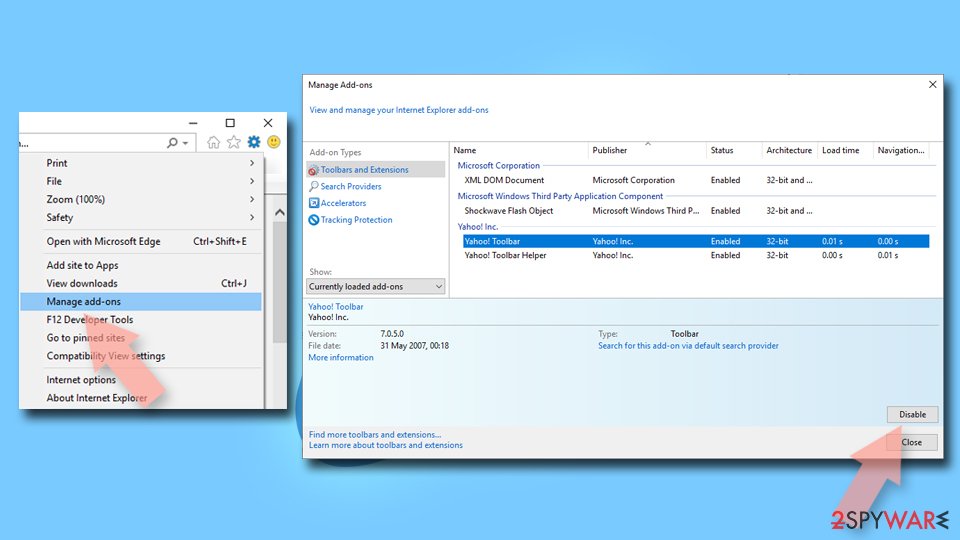
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
![Remove add-ons from Internet Explorer Remove add-ons from Internet Explorer]()
Since there could be other potentially unwanted apps or even malware installed on your device without consent, we recommend you check your system with a reputable anti-malware tool, such as SpyHunter 5Combo Cleaner or Malwarebytes. These apps can quickly and easily find and remove malicious components from your computer at once.
After virus elimination, you should take care of your privacy. The mentioned cookies and other items used for tracking could remain on your system for years once placed on your system, so make sure you remove them regularly (especially after the elimination of potentially unwanted programs). You can choose an automatic solution with FortectIntego or refer to the manual guidelines below:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Internet Explorer
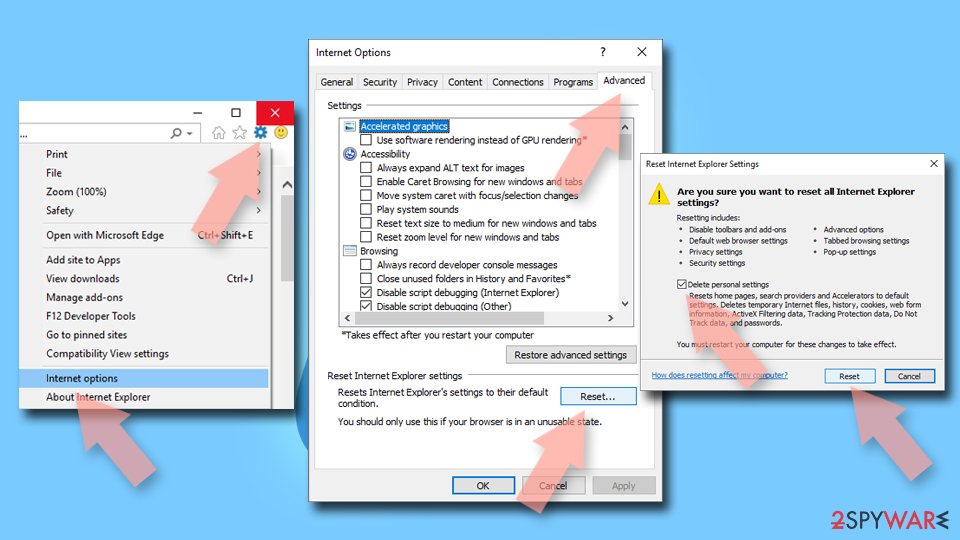
- Click on the Gear icon > Internet options and select the Advanced tab.
- Select Reset.
- In the new window, check Delete personal settings and select Reset.
![Reset Internet Explorer Reset Internet Explorer]()
How to prevent from getting browser hijacker
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Ransomware. Imperva. Application and data protection.
- ^ Bundled software. Computer Hope. Free computer help.
- ^ Cookies and Web Beacons. NTT. NTT Communications.