SnakeLocker ransomware / virus (Removal Guide) - Easy Removal Guide
SnakeLocker virus Removal Guide
What is SnakeLocker ransomware virus?
The twisted ways SnakeLocker developers make money
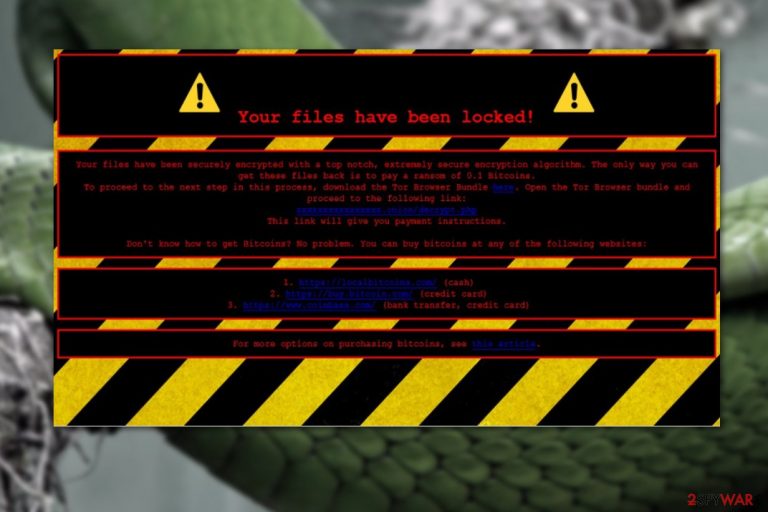
SnakeLocker virus is a ransomware-type[1] infection detected by security experts in mid-2017. Once installed, the malware is known to append .snake and .TGIF extensions to the affected files and display a ransom demanding note called INSTRUCTIONS-README.html. In the note, attackers ask for 0.1 BTC in exchange for a decryption tool.
The malware is Python-based [2] and has an additional version spreading alongside it. Both these variants are still under development, so they have the potential of blowing up in the future. As evident, the main goal of cybercriminals behind this threat is to monetize on victims' anxiety about losing their files forever. In this article, we will explain how to deal with this infection correctly and potentially recover your files for free.
| Name | SnakeLocker |
| Type | Ransomware, crypto-malware |
| File extension | .snake and .TGIF |
| Ransom note | INSTRUCTIONS-README.html |
| Ransom size | 0.1 BTC |
| Malware removal | Use powerful anti-malware software, such as SpyHunter 5Combo Cleaner, to eliminate all the malicious files on your computer |
| System fix | After malware elimination, you should take care of Windows system files to prevent crashes and errors due to the infection – FortectIntego can help you with that |
Indeed, ransomware is one of the most devastating infections out there. Usually, the attackers use an advanced encryption algorithm to lock all personal data on the infected device. The only way to retrieve access to these files is by applying a decryption key that is stored on the hackers' servers. Fortunately, there might be other chances of recovering your data, so do not hurry to pay, as criminals should never be trusted.
If you are already infected, you should remove SnakeLocker from your PC. If not – it is high time you start paying attention to your system’s security. You can start by obtaining acknowledged antivirus software such as SpyHunter 5Combo Cleaner.
Both versions of the parasite encrypt victim’s files and propose a twisted offer – the victims can either pay for the data recovery key or lose their documents forever.

Like in most ransomware cases, victims are demanded to make payments in Bitcoins as it is the quickest and most anonymous way criminals can receive money without being tracked down and prosecuted.
Nevertheless, if you don’t want to risk the thickness of your wallet – you can refuse to make the payment. In fact, it is recommended to avoid any collaboration with the cybercriminals and perform SnakeLocker removal as quickly as possible.
It is currently unclear what particular countries are likely to be most affected by this parasite. China [3], UK, US, and countries anywhere else in the world can become targets.
Decomposing ransomware distribution strategies
Just as much other malware of this type, the virus may slither inside your PC without you noticing. There are several ways stealthy system infiltration can be achieved:
- Through infected emails attachments
- Through fake online ads, download buttons or software update notifications
- Virus can be brought into your PC using exploit kits
You should keep all these SnakeLocker distribution methods in mind the next time you browse online or download suspicious email attachments. Be careful not to fall into traps set up for you by greedy scammers.
SnakeLocker removal instructions and file recovery
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). Likewise, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works.
If you attempt to use security or recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them.
Thus, if you do not have working backups, you should definitely backup your data before your proceed with malware elimination. Encrypted data does not hold any malicious code, so it is safe to transmit to other storage devices.
Once the files are copied, you can perform a full system scan with a reliable security tool. That being said, you should not proceed with data recovery methods before you use security software to ensure that all the ransomware components are deleted from your system.
Getting rid of SnakeLocker virus. Follow these steps
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from SnakeLocker and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Jasper Hamill. These ‘ransomware’ screens on your computer mean you’re in BIG TROUBLE – what to do if you fall victim to cybercriminals. Thesun. News, sport, celebrities and gossip.
- ^ Python (programming language). Wikipedia. The free encyclopedia.
- ^ Wubingdu. Wubingdu. Technology news, reviews and removal tutorials.
