Sodin ransomware (Decryption Methods Included) - Free Guide
Sodin virus Removal Guide
What is Sodin ransomware?
Sodin ransomware is the version of a cryptovirus that supposedly is linked with GandCrab creators
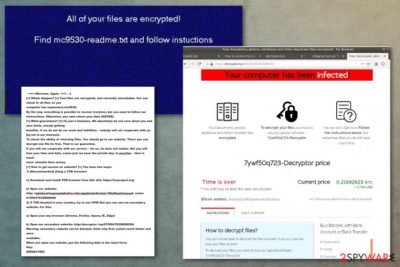
Sodin ransomware is the cryptovirus that encrypts files found on the machine and marks them with .mc9530 marker, so it can also be called .mc9530 virus. However, this is the version of Sodinokibi ransomware that is supposedly related to GandCrab because it was made available on the dark web forums and serves as ransomware-as-a-service.[1]
This ransomware comes to the system by exploiting Windows vulnerabilities like CVE-2018-8453[2] and then Sodin ransomware virus aims to change the default file extension to a .mc9530 appendix and make data useless this way. The purpose of this encryption is to have a reason for a ransom demand that can go up to thousands of dollars in the form of cryptocurrency like Bitcoin. The main area that this virus target is Asia, Taiwan, Hong Kong, and South Korea in particular, but there is a risk to get affected by this cryptovirus for anyone in the world. This is a dangerous threat that can lead to permanent data damage or even money loss because the lowest amount of ransom demand is $2500 in Bitcoin.
| Name | Sodin |
|---|---|
| Type | Ransomware |
| Family | Sodinokibi ransomware |
| File marker | .mc9530 |
| Distribution | Exploiting system vulnerabilities, infected spam email attachments |
| Ransom note | mc9530-readme.txt |
| Ransom amount | May differ from $2000 to $5000 in Bitcoin |
| Elimination | Get a reliable anti-malware tool and remove Sodin ransomware. Clean virus damage with FortectIntego |
Sodin ransomware infects the system and extorts money from the victim that wants to have files working normally again. The encryption process changes the original code of data in various formats. Photos, documents, videos, audio files, PDFs, and even archives get affected by this virus. The only type of data that ransomware is not encrypting is system files.
However, Sodin ransomware affects various system files and general settings of the machine to make needed changes and ensure the persistence of this malware. Malicious files or programs get installed on the machine to run processes of blocking the antivirus tools and security tools or features.
Also, Sodin ransomware can delete Shadow Volume Copies to keep the user from recovering the encrypted files and create new or alter existing registry keys to make the malware run every time your computer gets rebooted. You need a thorough system check to end those additional processes and terminate the ransomware entirely.
Nevertheless, all those changes happen after the primary Sodin ransomware attack – file encryption. The virus may start with a system check to make sure that the machine was not encrypted before. Then files get selected and encrypted immediately. Once that is done, the mc9530-readme.txt file appears on the desktop and in every folder containing the encoded data.
Sodin ransomware ransom message reads the following:
—=== Welcome. Again. ===— a
[+] Whats Happen? [+] Your files are encrypted, and currently unavailable. You can check it: all files on you
computer has expansion] mc953@.
By the way, everything is possible to recover (restore), but you need to follow our
instructions. Otherwise, you cant return your data (NEVER).
[+] What guarantees? [+] Its just a business. We absolutely do not care about you and your deals, except getting
benefits. If we do not do our work and liabilities – nobody will not cooperate with us.
Its not in our interests.
To check the ability of returning files, You should go to our website. There you can
decrypt one file for free. That is our guarantee.
If you will not cooperate with our service – for us, its does not matter. But you will
lose your time and data, cause just we have the private key. In practise – time is much
more valuable than money.
[+] How to get access on website? [+] You have two ways:
1) [Recommended] Using a TOR browser!a) Download and install TOR browser from this site: https://torproject.org/
b) Open our website:
http: //aplebzu4/wgazapdqks6vrcv6zcnjppkbxbr6éwket f56nf6aq2nmyoyd. onion/6750647830BDB096
2) If TOR blocked in your country, try to use VPN! But you can use our secondary
website. For this:a) Open your any browser (Chrome, Firefox, Opera, IE, Edge)
b) Open our secondary website: http://decryptor. top/6750647830BDBO96
Warning: secondary website can be blocked, thats why first variant much better and more
available.
When you open our website, put the following data in the input form:
Key:
[REDACTED]
Sodin ransomware developers shouldn't be trusted, so avoid contacting them, especially for the file recovery. This is a false promise that can lead to a more damaged device than encrypted files in the first place. Remember that these people are cybercriminals and experts[3] note now malicious these extortionists are.

We know how important these files that got encrypted are for you but focus on Sodin ransomware removal first, before worrying about data recovery. If you try to restore files with backups, you can damage your data permanently when ransomware encrypts files on the external device through the still affected system.
Get the anti-malware tool and scan the machine thoroughly. Then remove Sodin ransomware once it gets detected by the program and indicated as malicious alongside other applications or files. A thorough check on the computer should show various issues besides the malicious programs, so after the virus elimination, your machine runs better.
For additional check and insurance, we recommend rechecking the machine with a tool like FortectIntego that can delete Sodin ransomware virus damage and fix corrupted Windows files, for example. For data recovery, later on, we have a few suggestions below the article.
Sodin ransomware can be related to GandCrab developers, and even cybersecurity researchers expect a rise in attacks from this threat, so beware and clean the machine as soon possible, keep the system virus-free to avoid damage or other malware. Kaspersky officials even stated:
We expect a rise in the number of attacks involving the Sodin encryptor, since the amount of resources that are required to build such malware is significant. Those who invested in its development definitely expect it to pay off handsomely.
Vulnerable servers and other system flaws get exploited by the virus to get on the computer
The most common method or ransomware distribution is file attachments containing various malicious files like PDFs, documents or links to a direct download of the payload. Such emails come to email boxes and trick people into the opening and downloading the attachment by showing legitimate names of companies and services like DHL, FedEx.
This ransomware, in particular, is not that common when it comes to the distribution of this threat because the common method is to require interaction with a malicious file to open the document attached to the email, so malicious macros get triggered and launch the cryptovirus script. In this case, the executable file that is downloaded to launch the ransomware comes when the virus exploits system or server flaws.
Check the system and remove Sodin ransomware files from the system with anti-malware tools
To avoid falling victim to Sodin ransomware virus, you should ensure that your software is patched and updated regularly and the Windows operating system flaws cannot get exploited. You can do so by updating all the programs yourself or keeping system tools which help to optimize the machine automatically.
Another automatic process that we recommend relying on is the initial Sodin ransomware removal. You should get the professional anti-malware program and scan the system entirely to eliminate all the associated files, applications, and disable suspicious processes.
Programs like [d1[, SpyHunter 5Combo Cleaner, or Malwarebytes can remove Sodin ransomware completely, clean virus damage and indicate all the corrupted files, useless programs or data that may be malicious. Running an occasional system scan with such programs can improve the performance of your PC significantly.
Getting rid of Sodin virus. Follow these steps
Manual removal using Safe Mode
You should restart your machine and get to Safe Mode with Networking before eliminating Sodin ransomware. This way you can be sure that AV tool that you use works as supposed to
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Sodin using System Restore
System Restore is a method to fight Sodin ransomware virus because this feature allows recovering the system in a previous state
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Sodin. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Sodin from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Sodin, you can use several methods to restore them:
When you need to recover files affected by Sodin ransomware, Data Recovery Pro can help
Try Data Recovery Pro for accidentally deleted files or data that got encrypted in the ransomware attack
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Sodin ransomware;
- Restore them.
Windows Previous Versions as an alternate method for restoring encrypted files
When System Restore gets enabled, Windows Previous Versions can be used in data recovery
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer as a feature helpful after Sodin ransomware attack
When threats like Sodin ransomware leave Shadow Volume Copies untouched, you can Rely on ShadowExplorer for file recovery purposes
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption is not possible
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Sodin and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Bradley Barth. Report suggests GandCrab’s developers may have created Sodinokibi ransomware. SCmagazine. IT security source for news.
- ^ Orkhan Mamedov, Artur Pakulov, Fedor Sinitsyn. Sodin ransomware exploits Windows vulnerability and processor architecture. Securelist. Cybersecurity research and reports.
- ^ Virukset. Virukset. Spyware related news.





















