SplinterJoke ransomware (virus) - Tutorial
SplinterJoke virus Removal Guide
What is SplinterJoke ransomware?
SplinterJoke ransomware is the threat created by hacker group focused on the direct profit

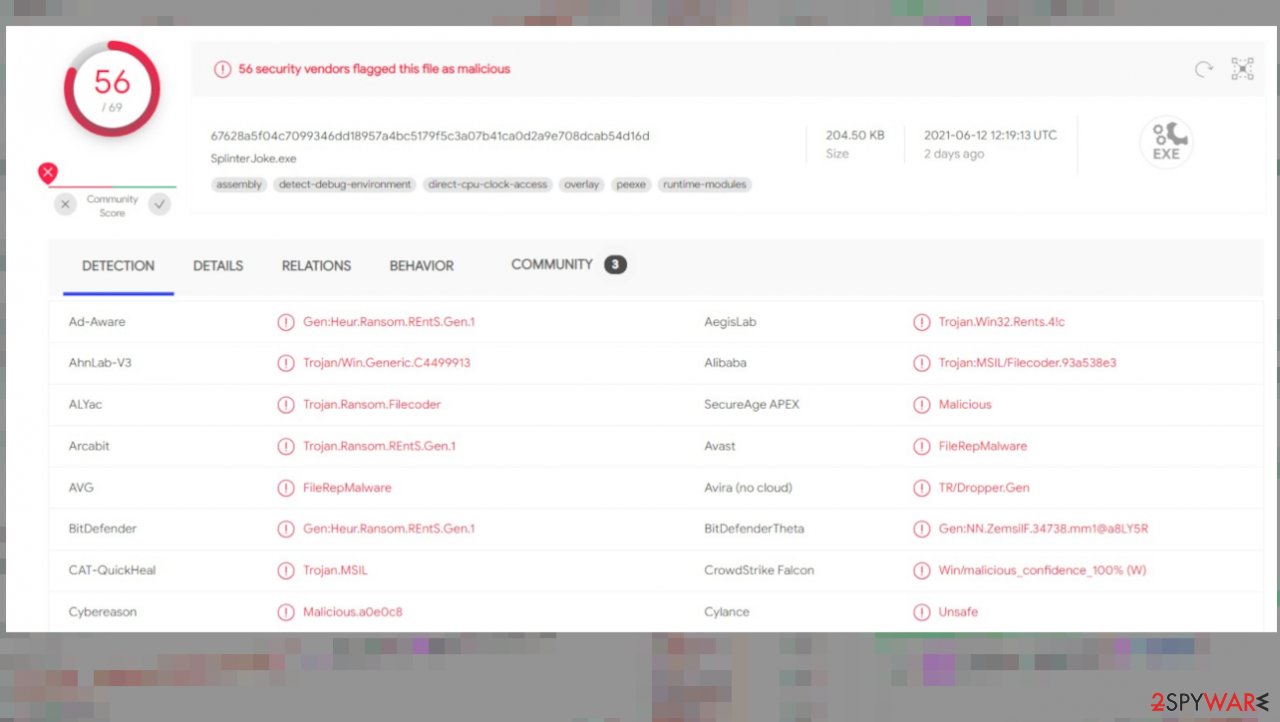
SplinterJoke ransomware is the virus categorized as a cryptocurrency-extortion infection because it locks files found on the machine to have a purpose of payment demands. The threat actors responsible for the infection call their product SetinelOne PoC Demo. The mentioned company is the name of the antivirus solution that finds these malware files malicious.
This indication appears in a text file ransom_note.txt that is delivered to the victim once file encryption is done. However, the name of the company is spelled with an error. This is a common tactic of deception that actors use. Criminals also claim that the only method of getting files back is purchasing the private key from them.
They also present the message about a particular virus infection on the Desktop image:
Pc infected bySplinterJoke RansomwareThis is just a POC forSentinelOne Demo
This virus relies on encryption methods[1], and locks found pieces of data to mark them using the .SplinterJoke appendix. The relation with other threats of the same type is unknown, and the analysis shows that the virus itself was created back in October of 2020. First samples were discovered back in May, but the outbreak of victim reports was reached on June 1st this year. It is believed that the threat is new and might have been under development still. Rsearchers[2] think that the campaign may be renewed later on and with more advanced techniques.
| Name | SplinterJoke ransomware |
|---|---|
| Type | File locker, crypto virus |
| File appendix | .SplinterJoke |
| Ransom note | ransom_note.txt |
| Malicious files | SpinterJoke.exe |
| Created | 2020 October |
| Distribution | File attachments from malicious emails, torrent sites, and pirating platforms |
| Elimination | You need powerful anti-malware tools that detect[3] the virus and can remove it fully |
| Repair | Do not skip through any steps and make sure to repair functions with the help from tools like FortectIntego that can find and recover system data affected by the infection |
SplinterJoke ransomware infection starts with the execution of the malicious code. This is where the executable file comes in handy. Once that file is added to the machine, it can launch the file search and malware activities like encryption, registry editing, and other processes.
The virus encrypts files using RSA and AES algorithm mixture and targets files like photos, documents, music, video data. Once encoded files are not accessible, the appendix comes at the end of every filename. The next step is to inform people about the infection. The ransom note message is delivered exactly for that purpose.
Unfortunately, the infection is happening in stages, and the process of infiltration allows developers to spread the threat without users' knowledge or interference. You may notice the slowness of the machine when the threat is infecting the machine and working in the background.
However, if you are the one that used pirating services, installed cracked software, paid not enough attention to details on the email, you are the one that let the infection on the system. You might not even notice issues with the machine and the encryption ends with the ransom demand on the screen.
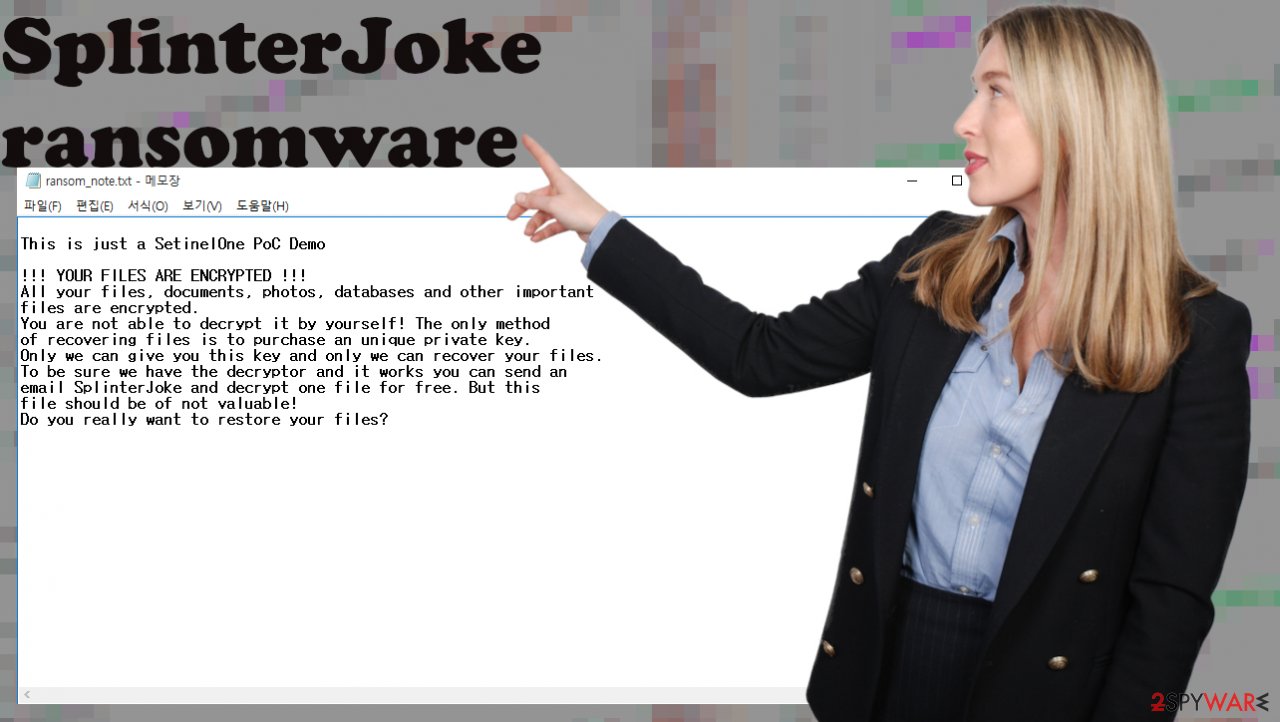
SplinterJoke virus shows the text file with the message:
This is just a SetinelOne PoC Demo!!! YOUR FILES ARE ENCRYPTED !!!All your files, documents, photos, databases and other important files are encrypted.You are not able to decrypt it by yourself! The only method of recovering files is to purchase an unique private key.Only we can give you this key and only we can recover your files.To be sure we have the decryptor and it works you can send an email SplinterJoke and decrypt one file for free. But this file should be of not valuable!Do you really want to restore your files?
File encryption can be repeated when additional files get found on the machine
This virus is one of many threats focused on money demands and data encryption. The process changes file original coding and make it useless, unopenable, locked. The indication is the marker added by the infection at the end of the process. You can see that some of the files get locked, and some of them not. It is because common types only get chosen for the locking.
SplinterJoke ransomware is not affecting system files or program prices this way. However, those files can be altered in a different way to keep the processes from running. Often some programs get disabled, including anti-malware tools. Unfortunately, if your security tool is disabled or damaged, you cannot easily remove the threat.
This is where anti-malware tools come in handy. You can choose a trustworthy program like SpyHunter 5Combo Cleaner and download a program on a different computer. Then run the full system scan using removable media like a USB stick. Make sure to keep other files out of the piece since encryption can be repeated. Keep your backups and other files away until the infection are fully cleared.
Also, tools like Malwarebytes are important since the detection of the threat may show the trojan or a different piece of malware that is responsible for spreading this ransomware. Crypto-extortion-based malware often comes with additional malicious pieces to ensure the damage.
Recovery after SplinterJoke virus infection
Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstallation is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program.
Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another. SplinterJoke ransomware can affect various parts of the system to ensure that encryption runs smoothly, so repairing these parts is crucial if you want to e the computer again.
File decryption is rarely possible, but you can get your data back
The data locking process is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data, .eaning that the key used to lock and unlock files is never the same. Especially when the mixture of bother known algorithms get used, like with SplinterJoke ransomware.
This simple principle is what allows ransomware authors to prosper in this illegal business. However, paying is never an option. Often criminals avoid contacting people, and once the payment is transferred, the virus is deleted, and developers are gone without any traces.
Regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. Often they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Alternate data restoring options
SplinterJoke file virus is a threat that relies on peoples' fear. The ransom note states about all the scary things, so transfer is getting to them quicker. The payment option shouldn't be considered. If you have any file backups, removing the virus and recovering those pieces with a recovery app can be the best fix.
Data recovery software might be able to help you in some situations when the ransomware is using a particular algorithm. In this case, SplinterJoke ransomware might be under development, so the encryption is not that strong. Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Note:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

The importance of the proper SplinterJoke ransomware removal
Since the infection is silent and very dangerous, you do not want to keep those malicious files on the machine for too long. The system gets affected when the payload file is dropped on the computer. Unfortunately, encryption is not the only process criminals can trigger. This virus is dangerous because:
- it involves money extortion;
- leads to data damage;
- can result in more infections when criminals get contacted;
- files get stolen;
- often targets large businesses and industries.
You need to rely on SpyHunter 5Combo Cleaner or Malwarebytes since these are the tools for proper system clearing. Anti-malware pieces like this can fin the virus and locate all the related pieces. When you clean the machine properly you can be sure that encryption is not going to repeat itself and that the SplinterJoke file virus is terminated for good, so your data backups can come in handy. Do not forget about FortectIntego and file damage that this or even related trojans can cause.
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Encryption. Wikipedia. The free encyclopedia.
- ^ Report on new malware. Twitter. Social media platform.
- ^ Virus detection rate. VirusTotal. Online malware scanner.
