Sqoo.co browser hijacker (Free Guide)
Sqoo.co browser hijacker Removal Guide
What is Sqoo.co browser hijacker?
Sqoo.co is a potentially unwanted browser extension that floods your searches with ads

Sqoo.co is a browser hijacker that forcefully takes control of your browser settings and reroutes your homepage, search engine, and new tab settings to its domain. Once installed, it redirects all your search results to Yahoo, but not without inserting numerous intrusive and potentially misleading advertisements within the results.
These constant ad insertions generate revenue for the hijacker developers, a deceptive and illegitimate way of monetizing web traffic. Beyond its inconvenient and invasive nature, Sqoo.co is also concerning because of its potential for data gathering, as it often collects your browsing history, search queries, and other personal data for various purposes, including targeted advertising.
However, it's important to know that these advertisements might not only be irritating, but they can also be harmful, misleading you to potentially unsafe web domains. If your browsing experience has been hijacked by constant redirects to Sqoo.co, it's likely that a malicious browser extension has been installed on your device.
It's imperative to not only remove this extension but also eliminate its traces to avoid further harm or invasion of privacy. This article will provide detailed steps on how to rid your device of this troublesome browser hijacker and safeguard your online presence.
| Name | Sqoo.co |
| Type | Browser hijacker, potentially unwanted application |
| Distribution | Software bundles, third-party websites, misleading ads |
| Symptoms | A browser extension or an application installed on the device; homepage and new tab address set to Sqoo.co; ads and sponsored links in search results and elsewhere; promotes other potentially unwanted apps |
| Risks | Installation of other potentially unwanted programs/malware, personal data disclosure to unknown parties, monetary loss |
| Removal | You can eliminate the browser extension by accessing your browser's settings. A scan with powerful security software SpyHunter 5Combo Cleaner is also recommended |
| Other tips | Once you've eliminated all potentially unwanted applications from your system, we strongly suggest using the FortectIntego tool. This utility not only sanitizes your web browsers, removing residual traces of undesired apps but also repairing any system files that may have been compromised or damaged. |
How browser hijackers spread
The world of the internet teems with numerous browser hijackers, such as Sqoo.co, capable of generating substantial ad revenue for their developers. However, their dubious operational practices and underhanded methods of installation are the primary reasons they are considered unwelcome applications.
These practices often include stealthy installations where users find themselves with these hijackers on their devices unintentionally or as a result of deceptive tactics. Two key examples include fake updates and software bundling:
-
Fake updates. Often, hijackers employ the strategy of masquerading as essential software updates. These misleading prompts are usually encountered on dubious websites with a propensity for unscrupulous practices. For instance, a user might visit a site and be met with a pop-up notification warning of an outdated software component. The unsuspecting user, aiming to keep their device secure and updated, accepts the “update,” inadvertently installing the browser hijacker. These so-called updates can feign system updates, driver updates, or even updates for popular software such as Adobe Flash Player or a browser itself.
-
Software bundling. This is another common tactic used to distribute browser hijackers. Software bundling refers to the inclusion of additional applications with a primary software package, often without the explicit consent or knowledge of the user. The bundled software might be presented as “recommended applications,” and they are often pre-selected for installation. In most cases, the bundled applications are potentially unwanted programs (PUPs), including adware or browser hijackers. Users typically install these unwanted applications by not choosing the custom or advanced installation options, where they could deselect the bundled software.
Both methods play on the lack of attention and knowledge of users. In the case of fake updates, they leverage the user's desire for a secure, up-to-date system, and in the case of software bundling, they rely on the hurried or inexperienced user who may not fully understand the implications of the pre-selected options during software installations.
In essence, the proliferation of browser hijackers like Sqoo.co owes to their deceptive installation practices, which serve to trick users into granting them access to their devices. Thus, it's crucial for users to maintain a high level of vigilance when browsing the web and installing software to guard against these unwanted intrusions.
Are browser hijackers dangerous? What to look out for
Browser hijackers, while annoying and intrusive, are generally not as perilous as other forms of malware, such as viruses, trojans, or ransomware. They don't directly cause damage to system files, steal sensitive information, or encrypt data for ransom. Their primary objective is usually to manipulate browser settings to redirect traffic and display ads, serving a monetary goal rather than a destructive one.
However, it's important not to dismiss browser hijackers as completely benign. If installed from questionable websites or slipped into your system through deceptive practices such as bundling, they might exhibit traits that go beyond mere annoyance. They frequently display skewed search results, which can not only disrupt your online activity but also potentially lead you to unsafe websites. Some of these websites might be riddled with more severe forms of malware or scam attempts.
Moreover, hijackers like Sqoo.co could involve potential privacy concerns as they tend to collect data about your browsing habits, which could be shared with third-party advertisers.
So, while browser hijackers aren't typically the stuff of digital nightmares, they certainly shouldn't be dismissed as harmless. They are a moderate security concern that could compromise your online safety and privacy if not managed properly. It's always best to maintain proactive online habits to prevent their installation and promptly remove them if detected.
Remove Sqoo.co hijacker correctly
Identifying the specific cause behind unexpected alterations in your browser settings can indeed be a daunting task, especially if your device hosts a multitude of applications. Browser hijackers, while typically manageable, can sometimes be hard to pinpoint and eradicate. Further complicating matters, these changes could also signal the presence of a more sinister threat lurking in your system.
For these reasons, the application of comprehensive anti-malware software is highly recommended. Tools such as SpyHunter 5Combo Cleaner or Malwarebytes are equipped with advanced detection capabilities, enabling them to easily uncover and eliminate a range of malicious programs that might be challenging to spot and remove manually for an average user.
These anti-malware tools perform a thorough scan of your system, scrutinizing each file and application to ensure no harmful element is left undetected. By using such software, you not only deal with the immediate concern of the browser hijacker but also safeguard your system from potential threats that might have snuck in.
If, however, you prefer a hands-on approach, there is always the option to manually tackle the problem. Below are detailed steps you can follow to hunt down and remove the browser hijacker from your device.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the window's top-right).
- Select Add-ons.
- Here, select the unwanted plugin and click Remove.

MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Internet Explorer
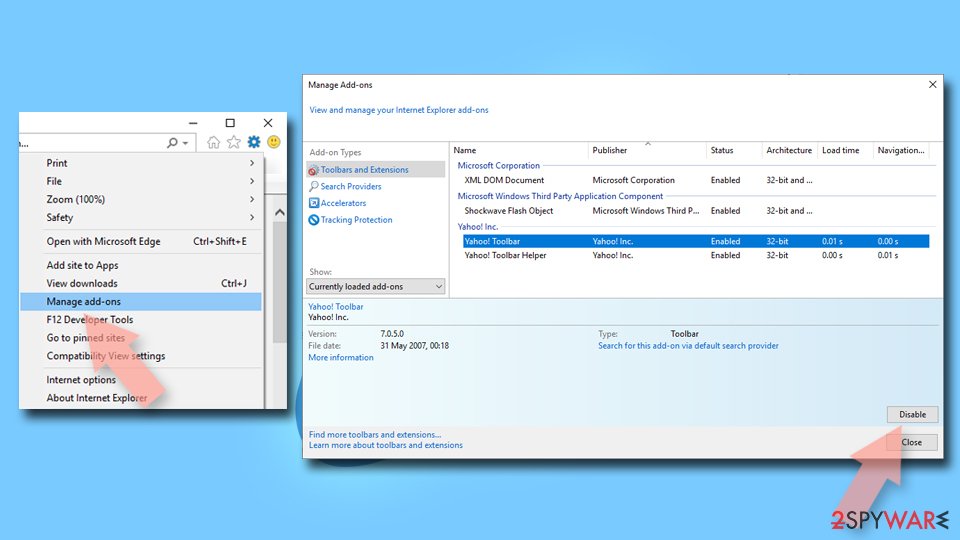
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
Clearing your browser caches is a critical step to take following the removal of potentially unwanted applications (PUAs) such as browser hijackers. Browser caches store information about your browsing history, site preferences, and even login credentials, and these could have been compromised during the hijacker's residency on your device.
Moreover, remnants of the hijacker could still be lurking in your cache, leading to a potential resurgence of the problem. By clearing your browser caches, you're effectively wiping clean any residual traces of the PUA, ensuring a more secure and clutter-free browsing experience.
While this can be done manually, using a comprehensive maintenance tool such as FortectIntego streamlines the process, effectively eliminating any leftover data with minimal user intervention. Nonetheless, for those who prefer a manual approach, detailed steps for cache clearance can be found below.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

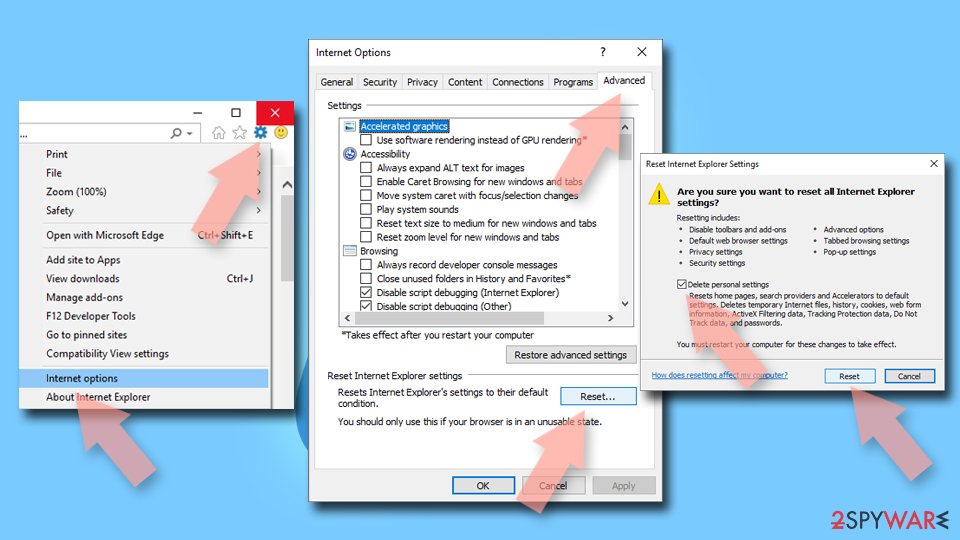
Internet Explorer
- Click on the Gear icon > Internet options and select the Advanced tab.
- Select Reset.
- In the new window, check Delete personal settings and select Reset.
How to prevent from getting browser hijacker
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
