Summer Locker ransomware (virus) - Tutorial
Summer Locker virus Removal Guide
What is Summer Locker ransomware?
Summer Locker ransomware holds files hostage until victims pay a ransom
Summer Locker is a ransomware-type virus that targets people and demands money from them. As soon as it enters, it infects the systems and starts to prepare for data-locking using a sophisticated encryption[1] algorithm. This way, all images, documents, databases, videos, and other files are encoded, and the .summer extension is appended to them.
Due to this process, all of the data has become illegible and unavailable to users. They would only get an error message claiming that the file format was not recognized while attempting to open files. Since encryption is a safe means of locking data, even if they tried to access a file using another application, they would still be unsuccessful.
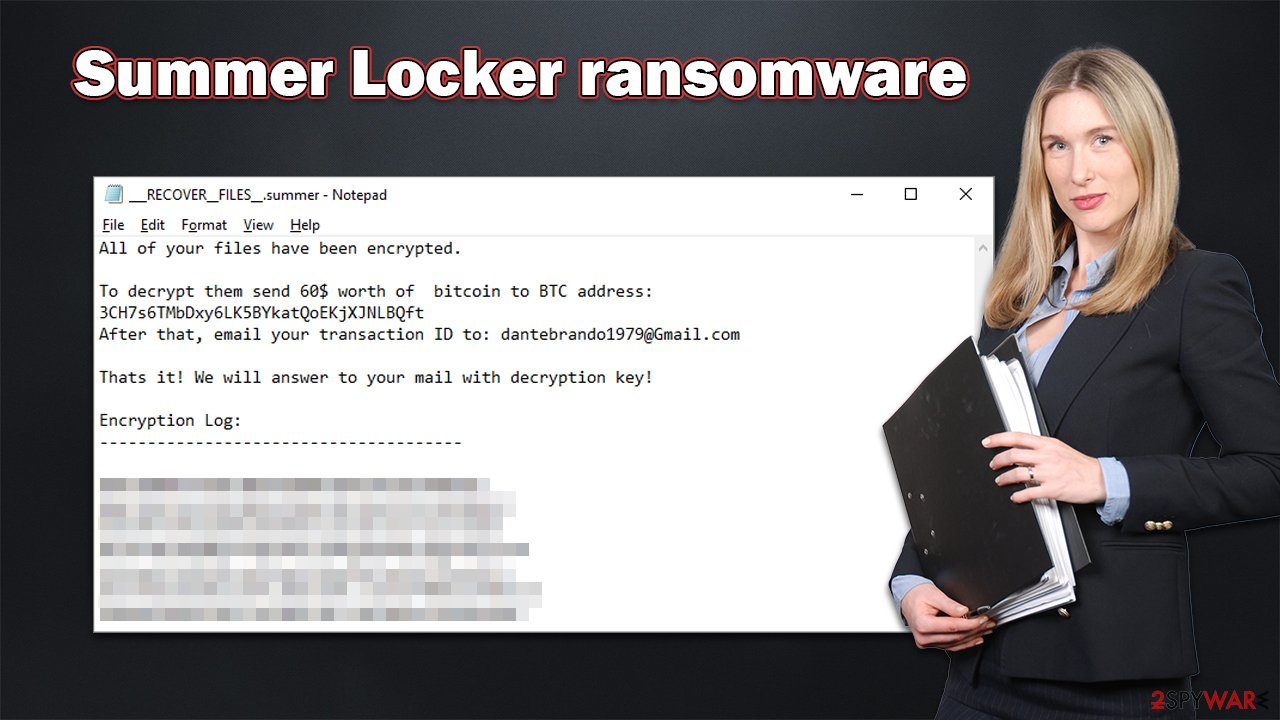
According to the ___RECOVER__FILES__.summer.txt ransom note that is dropped on the device soon after, users have to pay $60 worth of bitcoin to the 3CH7s6TMbDxy6LK5BYkatQoEKjXJNLBQft digital wallet used by cybercriminals. They also inform that after a successful money transfer, victims should contact them via dantebrando1979@gmail.com to arrange the recovery of a decryptor.
| Name | Summer Locker virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .summer appended to all personal files, rendering them useless |
| Ransom note | ___RECOVER__FILES__.summer.txt |
| Contact | dantebrando1979@gmail.com |
| Ransom size | $60 to be paid in bitcoin |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | After disconnecting the computer from the network and the internet, do a complete system scan using the SpyHunter 5Combo Cleaner security program. |
| System fix | As soon as it is installed, malware has the potential to severely harm some system files, causing instability problems, including crashes and errors. Any such damage can be automatically repaired by using FortectIntego PC repair |
Ransom note analysis
Soon after the Summer Locker virus finishes data encryption, it delivers the following ransom note, which serves as a message from the malicious actors:
All of your files have been encrypted.
To decrypt them send 60$ worth of bitcoin to BTC address: 3CH7s6TMbDxy6LK5BYkatQoEKjXJNLBQft
After that, email your transaction ID to: dantebrando1979@Gmail.comThats it! We will answer to your mail with decryption key!
A ransom note serves an important purpose in the illegal ransomware business. Without it, users would not be able to contact cybercriminals when attempting to restore the encrypted files, so the possibility of a successful payment is non-existent. This is why the note is almost always delivered in a TXT format, as it can be accessed on all Windows machines.
Summer Locker ransomware authors do not provide extensive insights on the whole ordeal and stick to important pointers – the crypto wallet, contact email, and the sum that needs to be transferred. While $60 may not seem a lot for many, it may still result in financial losses, as threat actors may never fulfill their promises or even reply to the email.
Besides, paying the demanded ransom would only encourage the attackers to create more malware and infect more people. Thus, we recommend never negotiating with cybercriminals and relying on alternative data recovery solutions instead. Before that, a thorough malware removal should be performed – more details on the process can be found below.
Ransomware removal
When attacked by ransomware, victims are frequently unsure what to do next. The majority of affected people are, in fact, first-time victims, and some of them don't even understand what ransomware is or what it does. In fact, doing malware removal and data recovery properly is crucial; else, the entire recovery might fail and cause much more damage.
Malware may connect to a remote Command & Control server as soon as it has access to the system. This enables thieves to instruct malware to carry out additional tasks, update itself, or even distribute new payloads. Therefore, before starting the Summer locker virus removal process, it is crucial to disconnect your computer from the internet (and the network, if applicable).
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Once the internet connection has been closed off, the infection should be eliminated using SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful protection program. Before continuing, it's crucial to update anti-malware definitions. You may always enter Safe Mode and try the eradication procedure from there in case ransomware is interfering with it:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
Once you are sure that malware is eradicated from your system, you can proceed with the data recovery process.
Data recovery
The processes of data encryption and ransomware infection are independent of one another, even if the former would not have been possible without the latter. Many victims think these two elements aren't exclusive, therefore, they assume that scanning systems with anti-malware software would return files to their original state. That is not the situation here, and that's one of the main reasons why ransomware is such a threat to regular users and businesses alike.
A different key is used for each victim in the complex encryption procedure. It is crucial to remember that files are not destroyed in any way; instead, they are only inaccessible without the decryptor, which means that users cannot open the data without it. While a scan will eliminate the virus, it will not be able to retrieve personal files that have been encrypted by ransomware because security software is simply not designed for this purpose.
Instead, we recommend trying dedicated recovery software, which may be helpful in some cases. Before proceeding, make sure you back up .summer files on a USB or another separate medium.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Summer Locker ransomware Summer Locker ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Thanks to the work of security experts, decryption solutions may eventually be developed for specific ransomware outbreaks. In rare circumstances, law enforcement seizes the servers of criminals,[2] allowing the keys to be made public. Reputable security companies typically provide access to free decryption tools, so you may find the following links useful:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Further tips
Especially when it comes to ransomware, whose effects might persist even after the danger has been removed, malware infestations can be particularly catastrophic. Whether you were successful in retrieving your data or not, we advise you to keep in mind a few pointers in case they come in handy again.
First and foremost, because malware can cause major system harm, we advise maintaining the health of your system. System files may get damaged after becoming infected, and antivirus simply cannot address it. You might get aid from specialized software like FortectIntego, which fixes stability problems, including registry errors and Blue Screen of Death[3] crashes, by replacing damaged files with functional ones.
Malware assaults are taken very seriously by the authorities, who constantly fight against them. You may assist them in capturing the offenders by reporting the incident to responsible parties. The following resources might be useful:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

You should contact the local police department or communications center if your country is not listed above.
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Encryption Algorithm. Techopedia. Professional IT insight.
- ^ Europol takes down VPNLab, a service used by ransomware gangs. The Record. Daily breaking news.
- ^ Blue screen of death. Wikipedia. The free encyclopedia.












