Tamus.live ads (scam) - Free Instructions
Tamus.live ads Removal Guide
What is Tamus.live ads?
Tamus.live shows fake infection messages to frighten users and make them purchase software
Tamus.live is a malicious website made by scammers for profit. It is unlikely for you to come across it while using the search engine (unless it's unreliable), so the only two other ways of getting here are either during visits to already high-risk websites or due to adware[1] running in the background and redirecting you there.
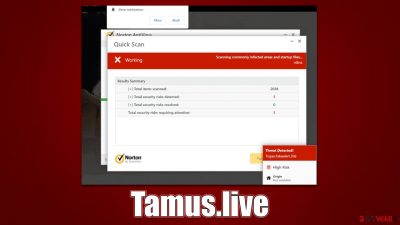
After a redirect to Tamus.live, people are usually presented with an animation of several pop-up messages which imitate a scan performed by McAfee, a popular security software provider. In mere seconds, users are told devastating news – their systems are infected, and they need to do something to fix it as soon as possible. Of course, the solution for this is to download and install security software that would allegedly remove all the found threats.
In reality, Tamus.live is a scam and has nothing to do with the official software from McAfee. People behind it are crooks that operate fake virus alerts in order to frighten users, make them concerned about their system security, and then provide the fake solution of installing security software, paying for its license in the process. In other words, it's just a scheme to make users buy software, where crooks receive a commission every time.
| Name | Tamus.live |
| Type | Scam, fraud, phishing, redirect |
| Infiltration | Redirects from other websites, pop-up ads, potentially unwanted applications |
| Operation | The scam is based on scaring users into believing that their systems are infected and that they need to remove the allegedly found malware with promoted software |
| Dangers | Fake messages usually aim for users to download potentially unwanted or malicious programs, steal their personal information or trick them into subscribing to useless services |
| Removal | You should not interact with any links or ads shown on the scam page and shut it down immediately. Then, perform a full scan with SpyHunter 5Combo Cleaner security software as a precautionary measure |
| Other tips | To prevent data tracking, clear caches and other web data with the FortectIntego repair and maintenance tool. It can also be used to restore damaged system components |
The scan results mention widespread malware
The face scan results are presented to look like they are coming from a reputable security software provider, as it includes the logos and trademarks of McAfee. This is one of the main reasons why some people might be inclined to believe the Tamus.live scam – they think that the warning is coming from a reputable source.
Imitating high-profile companies is common ground among online scammers – they often use the names of Microsoft, Apple, Google, and others. In this case, it's a security vendor name that should convince people of the following:
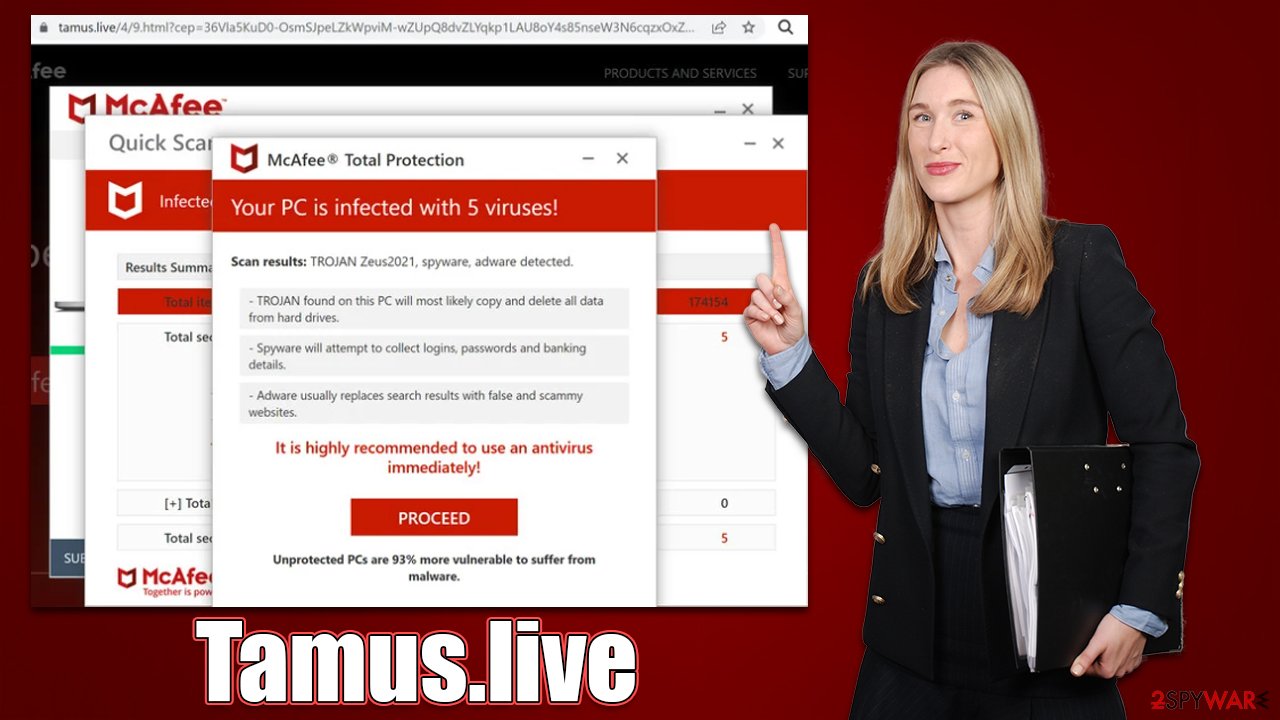
McAfee Total Protection
Your PC is infected with 5 viruses!
Scan results: TROJAN Zeus2021, spyware, adware detected.
- TROJAN found on this PC will most likely copy and delete all data from hard drives.
- Spyware will attempt to collect logins, passwords and banking details.
- Adware usually replaces search results with false and scammy websites.
It is highly recommended to use an antivirus immediately!
PROCEED
Unprotected PCs are 93% more vulnerable to suffer from malware.
Zeus Trojan is among the most notorious malware to strike the population in the 2000s, where hundreds of thousands of PCs were infected by it. It is unlikely to be infected by the real virus nowadays, but scammers adopted the name of the virus over the years, and its usage is prevalent to this day.
It is important to note that the language used in this message is extremely uncommon for any real security software – it would never tell you what it may do and what the consequences are. Real anti-malware detects threats, quarantines them, and deletes all files and other malicious components at once without any further details.
What to do next
Many people might be affected by phishing messages hosted by Tamus.live and similar websites in numerous ways. The first group of people may believe the scam message and click the “Proceed” button. At this time, they are likely to be redirected to a page where they would be asked to purchase and install security software. While it may be a genuine security provider website, redirects may also lead to malicious sites where malware could be downloaded and installed instead. Thus, we do not recommend interacting with these links or downloads.
Some people may believe that their systems might be in danger because of accessing a scam website. However, this is very unlikely to happen unless there are software vulnerabilities[2] on your device (to mitigate, always make sure that all software and the operating system are updated with the latest security patches).
Nonetheless, regardless of how you acted after entering the Tamus.live scam site, you should always make adware checks. Adware may have been installed by you accidentally along with freeware,[3] so you may not even know it's running on your device. Other malware could be even sneakier and access your system without your knowledge.
Thus, employ SpyHunter 5Combo Cleaner or Malwarebytes and proceed with a full system scan. This would ensure that your system is clear from any infections and would also serve as a first security measure when dealing with incoming attacks in the future. If you want to check for adware manually, proceed with the following steps:
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
While moving apps into Trash is usually how you delete most normal applications, adware tends to create additional files for persistence. Thus, you should look for .plist and other files that could be related to the virus. If you are not sure, skip this step entirely.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
You can also check installed extensions on your browser, as adware often spreads as such. You can quickly and easily remove these by clicking the “Extensions” button located to the right of the URL bar/next to the browser menu.
When all undesirable extensions have been deleted, we recommend clearing browser caches to avoid third-party data tracking. Adware may place cookies on your browser and use them to monitor your online behavior. The FortectIntego maintenance software is the simplest way to do this, although a manual approach can also be used:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Internet Explorer
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
![Clear temporary files from Internet Explorer Clear temporary files from Internet Explorer]()
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Adware. Investopedia. Source of financial content on the web.
- ^ Thomas Holt. What Are Software Vulnerabilities, and Why Are There So Many of Them?. Scientific American. Science Magazine.
- ^ What Is Freeware?. Lifewire. Tech News, Reviews, Help & How-Tos.