Tidings adware (virus) - Free Instructions
Tidings adware Removal Guide
What is Tidings adware?
Tidings is a malicious Windows app that redirects you to fake websites and shows you disruptive ads

Tidings is an adware-type infection that you might find installed on your device one day unexpectedly – this is mainly because this type of software spreads using deceptive methods, including bundled software or deceptive links on suspicious websites online. Once installed on your computer, it might start leading you to suspicious websites and show intrusive ads on websites that you visit, as well as track your data.
The advertisements stemming from Tidings adware can be hazardous as they frequently contain erroneous information regarding your computer's well-being and may attempt to persuade you to click on fraudulent gift cards and other phishing material. We advise against engaging with these ads and urge you to promptly eliminate the adware from your computer.
| Name | Tidings adware |
| Type | Adware, potentially unwanted application |
| Distribution | Software bundling, third-party websites, misleading ads |
| Symptoms | Shows intrusive advertisements, phishing material, and promotes other potentially unwanted applications |
| Risks | Ads may redirect to potentially harmful or even malicious websites, resulting in malware infection, personal information exposure, and financial losses |
| Removal | The simplest way to remove malicious software from Windows is to use SpyHunter 5Combo Cleaner security software and then clean web browsers. |
| Other steps | After you eliminate all PUPs and malware, you should clean your browsers of cookies and other data to protect your privacy – you can use FortectIntego for that |
How Tidings adware is distributed
Adware is commonly disseminated through questionable download pages, often encountered through redirects from dubious sites, mistyped URLs, or existing adware. Therefore, finding adware through search results is unlikely. It is crucial to exercise caution when accessing unfamiliar websites, particularly those involved in illegal activities such as illegal streaming platforms.
Another possibility is Tidings adware infiltrating the system as bundled software. This occurs when freeware distribution platforms include additional programs in the installers to monetize user activity. Many users unknowingly install additional programs as they rush through the installation process without carefully examining each step.
To avoid such scenarios, consider following these steps:
- Choose the “Custom” or “Advanced” installation methods.
- Read the Privacy Policy and Terms of Use.
- Check the file list and untick boxes next to any unrelated apps.
It is best to avoid third-party download pages entirely, as they cannot be trusted. Instead, use official web stores and developer websites to install software. Apps listed in stores undergo an extensive review process.
Regardless of the method used to install software, it is crucial to conduct research by reading reviews, analyzing ratings, and assessing the number of users an application has. Choose programs with positive feedback and thousands of users. Remember, being mindful and diligent is key to avoiding adware and other malicious software.
Tidings virus infection symptoms
Adware is a crafty program, and its presence may not always be immediately obvious. Non-users of ad-blockers may encounter numerous intrusive ads when browsing websites, making it difficult to identify malicious activity.

However, there are several symptoms that may indicate this adware infection:
- Display of advertisements outside of your browser, often in the form of pop-ups
- Clicking on links redirects you to potentially dangerous phishing websites
- Advertisements requesting the installation of fake Adobe Flash Player or other phony software updates. Pop-ups warning about a virus on your system may also be frequent
- Presence of the “Tidings” application on your system, with the processes “Tidings app” and “Tidings tech Copyright All rights reserved.”
If you notice any of these symptoms, it is critical to take immediate action to remove the adware from your system.
Removal instructions
Adware can be particularly harmful when it is installed as a system-level program. This enables it to establish deeper roots within the system and conduct more destructive activities. For instance, it may establish background connections with insecure domains or transfer data that can leave users vulnerable to cyberattacks.
While adware may be challenging to detect, it poses a more significant threat since it persists on the system even after uninstalling the primary application. The infection may even resurface later, as its files remain in the “AppData” folder.
To eliminate all potential threats to your system, the most straightforward approach is to scan it with reliable security software, such as SpyHunter 5Combo Cleaner or Malwarebytes. This way, you can avoid accidentally leaving any malicious files running on the system. Alternatively, you can follow the manual steps outlined below:
Windows 10/8
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Windows 7/XP
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
After the elimination of the main program, you should also make sure to remove its remnants that would reside in the AppData folder as follows:
- Press Win + E to open File Explorer
- At the top, go to the View tab
- Mark the Hidden items checkbox
- Next, go to your main drive (usually drive C) and enter the following path:
C:\Users\YOURUSERNAME\AppData\Roaming - Locate the Tidings folder and delete it by pressing Shift + Del on your keyboard.
Taking care of trackers
To prevent unwanted data tracking, it's essential to delete cookies and other web data from your browser. Adware often employs cookies as a tracking tool, and Tidings is no exception. It stores cookies locally on the victim's computer, enabling continuous monitoring of their online activities, such as browsing history, search terms, viewed ads, device information, unique identifiers, and more. The easiest way to clear browsing data is by employing maintenance utility FortectIntego, although manual steps are available below if that's your preference.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

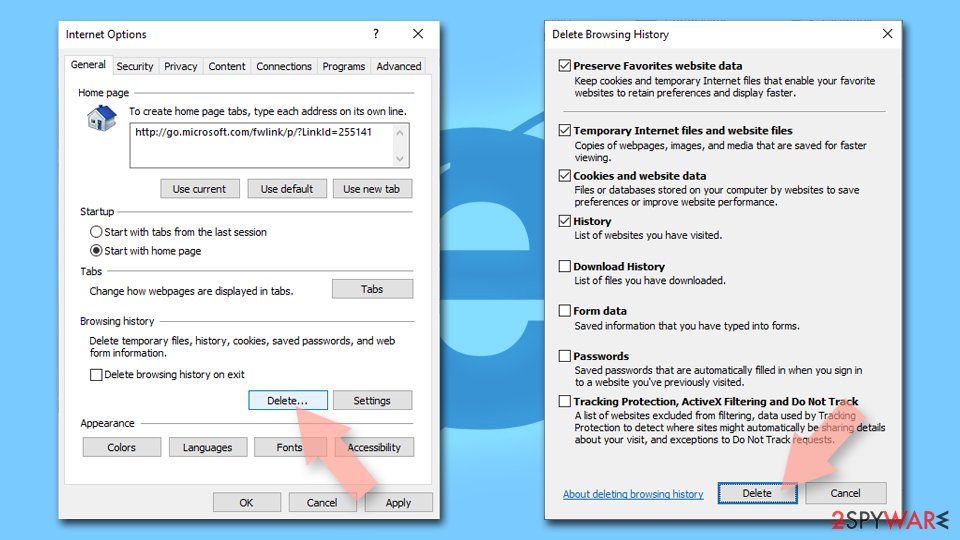
Internet Explorer
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
