Trojan-IM.Win32.Faker.a (Removal Guide) - 2021 update
Trojan-IM.Win32.Faker.a Removal Guide
What is Trojan-IM.Win32.Faker.a?
Trojan-IM.Win32.Faker.a – a name used by scamware to threaten users
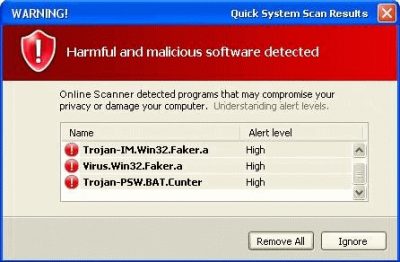
Trojan-IM.Win32.Faker.a is not a real name of a malicious program but rather an invented one by scammers. Rogue antispyware is a type of software that usually gains access to users' machines by using deception and then begins showing fake scan results. The main goal of such applications is to convince users that they need to purchase the full license of the app in order to eliminate alleged viruses from the system. Do not give in to a scam, and do not waste your money.
However, if you saw this name in some type of warning on your PC or a random website while browsing the internet, you should not trust it at all. You should also immediately scan your machine with powerful anti-malware software instead.
| Name | Trojan-IM.Win32.Faker.a |
| Type | Rogue antispyware, scam |
| Distribution | Fake online scanners, drive-by downloads, fake updates, deceptive ads |
| Dangers | When seeing fake infection results, users might be inclined to purchase the “full version” of the rogue antispyware software, resulting in monetary loss. Also, other malware could be installed in the process, and personal information leaked to cybercriminals |
| Removal | Access Safe Mode and run a scan with anti-malware software to eliminate all malware from your PC |
| System fix | Rogue antispyware programs can seriously damage Windows system files in order to perform their malicious actions. As a result, users may suffer from system crashes and errors. To address that, fix virus damage automatically with a repair tool FortectIntego |
It is important to note that Trojan-IM.Win32.Faker.a was a legitimate threat name that was used for malware in around 2006. The virus was a real Trojan designed to steal passwords of MSN instant messenger users and then use that information for malicious deeds.
As evident, this threat is no longer active, and it is very unlikely that this parasite will infect your computer nowadays. If security alerts warn you about this infection, the alerts are most likely loaded by a fraudulent program. Rogue anti-spyware and anti-virus applications often report imaginary trojans and viruses to scare people and push them into paying money to remove non-existent threats.
Many older viruses, such as Zeus, are also used in various scam schemes. If you happen to download fake antivirus software such as PC Antivirus Pro, Smart Guard Protection, or Windows Police Pro, you are likely to see such notifications displayed in various ways, including taskbar alerts or pop-ups on your desktop.
Rogue antispyware apps are known to take over users' computers in various ways; for example, they might block users' access to the internet, meddle with the hosts file, change Windows registry keys, and much more. Due to this, an infected system becomes unstable – victims are bombarded with virus alerts and requests to purchase the full version of the program to allegedly fix everything.
However, you should never trust such programs to remove malware from your device, as they are parasites themselves. The best thing you can do is install a real antivirus, such as SpyHunter 5Combo Cleaner, and perform a full system scan. In case your browsers were compromised, or system files damaged, use FortectIntego.
How to avoid being scammed by fake notifications
Rogue antispyware software still exists today, but it is much less prevalent than it was ten years ago, thanks to various security measures and advanced anti-malware engines that are used today. Nowadays, you are more likely to see fake notifications that claim virus infections upon accessing a scam website after being redirected from somewhere else. Most commonly, such redirects happen on illegal software distribution sites, YouTube video converting sites, and similar high-risk places.
Therefore, if your browsers suddenly took you to a location you did not intend to visit, you should always view the information displayed critically. In the best-case scenario, you could subscribe to unwanted notifications, while in the worst case, software vulnerabilities present on your device could be exploited to install malware on your PC automatically.
To avoid these scenarios, install a security application with a web protection feature – it would warn you about potential danger. Note that not all websites can be detected, however, so you should never trust notifications that claim some software is out of date or that your computer is infected with malware.
Do not ignore fake virus alerts on your device
First of all, you should not panic when you see a notification flashing in red, claiming that your passwords being leaked and your credit card information is stolen. These claims are nothing but fiction, so you should not be too concern about those. The true scope of the infection, however, can only be identified by real anti-malware software.
Thus, although Trojan-IM.Win32.Faker.a is not a real threat to your computer. It indicates that the program warning you about this fake infection is malicious. Remove any program that spawns such fake pop-ups and messages. This trojan is usually “detected” by an Internet Antivirus rogue application, so you should look for that. However, the best way to eliminate rogue antispyware is by performing a full system scan with SpyHunter 5Combo Cleaner or Malwarebytes.
Note that malware might prevent you from launching real security tools. In such a case, access Safe Mode with Networking and perform a scan from there. Once finished, follow up with a scan with FortectIntego to ensure that Windows system files were not damaged by the virus.
Getting rid of Trojan-IM.Win32.Faker.a. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Trojan-IM.Win32.Faker.a and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting trojans
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.














