Troldesh virus (Removal Guide) - updated Jun 2019
Troldesh virus Removal Guide
What is Troldesh virus?
Troldesh is the cryptovirus that keeps on encrypting users' files since 2014 and remains active in 2019
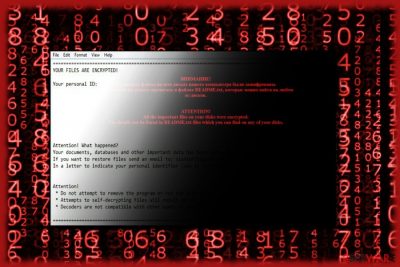
Troldesh ransomware – a dangerous virus that hails from Russia. The virus was recently spotted spreading new campaigns all over Russia, Mexico, and the U.S. The security software developers and malware researchers Avast discovered more than 100 000 attacks in 2019 by this particular strain of the cryptovirus.[1] Various phishing email campaigns and social media messaging platforms knowingly help to deliver the ransomware with malicious links and infected files.
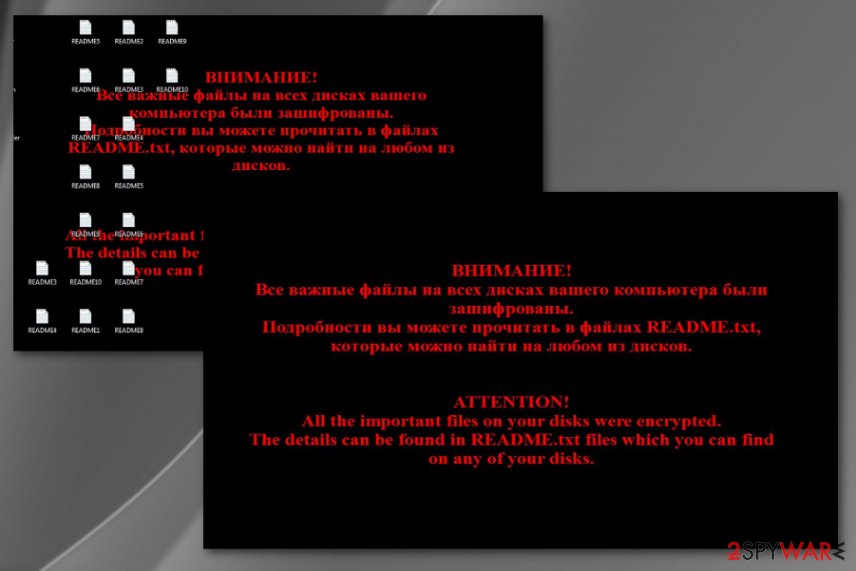
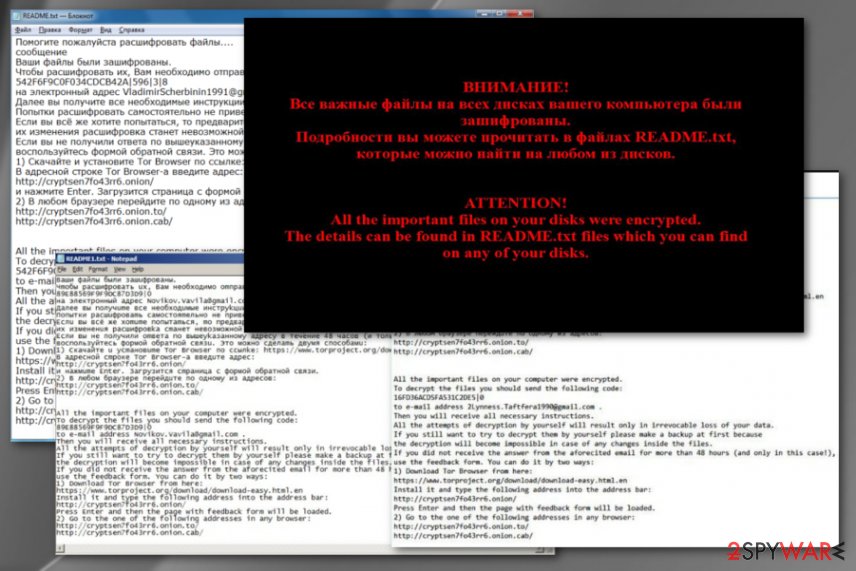
With the help of the asymmetric algorithm, Troldesh virus is capable of encrypting a broad range of audio, video, excel, and similar files. After it finishes this procedure, it appends .xtbl, .crypted000007, .dexter, .da_vinci_code, .no_more_ransom and .magic_software_syndicate file extensions to damaged data.[2] Also, it changes the wallpaper into the ransom note filled with links to Tor addresses. The ransom note can be written either in English or in Russian.
| Name | Troldesh |
|---|---|
| Type | Ransomware |
| File marker | .xbtl or .cbtl |
| Versions | Shade ransomware and No_more_ransom virus |
| Malicious files added on the system | csrss.exe, state.tmp |
| Ransom note | README.txt |
| Known since | 2014 |
| Known to install | Pony, teamspy RAT, banking trojans and other malware |
| Distribution | Phishing emails, spam campaigns, other malware |
| Elimination | Use anti-malware tool to remove Troldesh ransomware and clean the machine with FortectIntego to eliminate virus damage |
Alternatively, Troldesh ransomware is known as CrySis ransomware, xtbl, Shade, Virus Encoder, Green_Ray, Ecovector, and gerkaman@aol.com.xtbl. All its versions function as file-encrypting threats: they encrypt victim's files and request to pay a ransom. First signs of this virus were noticed back in 2015. Two years later, security experts find it as one of the most productive ransomware viruses.[3]
The ransom which is required by Troldesh virus varies from 0.5 to 1.5 BTC. However, having in mind that ransomware has started using such movement tools as Mimikatz, the ransom can increase and, in most cases, is based on the value of the victims' data.
According to Troldesh ransomware developers, Russian hackers, making this ransom payment is the only way to acquire two different keys, public and private, and recover lost data, so there is no surprise that users keep paying. As a result, the ransomware business is now considered to generate $2 billion per year.[4]
Needless to say, you should not give in to the pressure of hackers and pay a required ransom because it does not guarantee the retrieval of encrypted information. Instead, opt for Troldesh ransomware removal to prevent the further loss of your files. For that purpose, we recommend using FortectIntego.

Troldesh uses private and public keys that are mathematically interrelated, so files that are encrypted with a public key can only be decoded with the private key. You can feel safer if you have an extra copy of each of your file. In this case, you can avoid making the required payment. However, note that you have to remove Troldesh ransomware first before proceeding to the data recovery procedure.
While the requirement to pay the ransom is given in Russian and English, it is believed that Russia and English-speaking countries are the main targets. In the beginning, the virus tended to use the TOR browser to monitor the payments received from the victims.
Recently, it has been observed that it switched to another way of communication. In the README.txt file, Troldesh presents an email address. Thus, when victims contact them, cybercriminals indicate the amount of ransom. Surprisingly, after contacting the hackers directly, some users even managed to negotiate with hackers and succeeded in receiving a discount!
If you have never been infected with ransomware, we highly recommend thinking about backups of your files right now! Keep in mind that ransomware business is booming and one of six email messages is set to infect users and block their files. To keep them protected, you can choose from several options. More information about them is given in this post: Why do I need backup and what options do I have for that?
It may seem that making the payment is the easiest way to remove Troldesh, you should never do that because it is likely that you will end up with lost money and no recovered data at all. In addition, you will support hackers and their future crimes in this way.
Troldesh ransomware 2019 attacks
June 2019 came with new reports about Troldesh files virus and the recent attacks that show the spikes on cryptovirus attacks in Russia, Mexico, and the United States. Researchers blocked hundreds of thousands of virus attacks that started the most active in January and lasted up until June 24th.
These campaigns also show the new distribution technique – social network campaigns, during which the malicious links get delivered via messaging applications and phishing emails. In the report researchers state that the malware seems to be dangerous and possibly will stay prevalent in the future:
We see a spike in the number of its attacks that is probably more to do with Troldesh operators trying to push this strain harder and more effectively than any kind of significant code update.
Troldesh versions:
Shade ransomware. It is known that these two ransomware viruses are related. To encrypt victim's files, it uses identical AES-256 encryption and generates two different keys for the user. Shade is also known to use .7h9r, .xtbl, .ytbl, .da_vinci_code, no_more_ransom, .better_call_saul, .heisenberg, .breaking_bad, and .windows10 file extensions to mark encrypted files. The ransom note is saved in README.txt file.
Virus Encoder uses AES encryption keys to lock out the target information. Moreover, the virus has a distinctive feature – it hides a decryption key in its command and control server. The virus attaches .xtbl extension to all corrupted files and asks paying a ransom in the same “README.txt” file. The ransom note is written in Russian and English.
The distribution method of the ransomware
Troldesh ransomware or any other similar threat spreads through several means. The main of them is considered spam. Security experts have already warned users about misleading emails that claim to be important messages from governmental authorities, reputable companies, etc. It seems that one out of six emails is filled with infected email attachments.
If you have recently received an email informing of a delivered package or urging you to review invoice details, do not make any reckless actions. Before opening such emails or attachments, contact the company directly. If you believe that an email is fake and could be related to spammers or hackers, you should never click on its attachment.
Besides, cybercriminals use corrupted websites that barely differ from the original and legitimate websites. If you found yourself on a website that seems too good to be true, you need to leave it without wasting your time. Additionally, make sure you stay away from suspicious pop-up ads which might be offering free updates, unbelievable prizes, and similar things. If you click on such ads or visit the mentioned websites, you might let ransomware to your system. Cybersecurity specialists report that this virus infects systems in a form of trojan-Ransom.Win32.Shade.
Update on ransomware distribution
Current samples of Troldesh are detected as fake TPVCGateway.exe files. It belongs to ThinPrint Virtual Channel Gateway command developed by a mobile software manufacturer Cortado AG. Crooks employ the same technique as other ransomware. By disguising the malware under the name of popular programs or files, they expect victims to execute them without any suspicions.
The recent analysis also reveals that the malware is detected as Gen:Variant.Razy.167623, Gen:Variant.Razy.167623, or Ransom:Win32/Troldesh.A[5]. It suggests that the malware is related to another well-known virtual threat – Razy ransomware.
The latter threat has released its updated version under the name of Salsa virus. It implies that the same gang of felons might be behind these threats. Furthermore, it has been revealed that Kelihos botnet is responsible for the cyber campaign of this threat. Therefore, you should stay vigilant and strengthen the protection of the device by keeping your system applications up-to-date.
Troldesh ransomware removal tips
To remove Troldesh from the system, you need to scan your computer with updated anti-spyware. Keep in mind that closing a huge black warning message, claiming that your files are blocked, is not enough to eliminate this ransomware. Otherwise, it can initiate the second encryption of your files.
For a successful Troldesh removal, we recommend using FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. The software will reveal each of malicious files, their location, and will remove all these components with only one click, so it will greatly speed up the elimination process.
After that, you should start thinking about all the possible alternatives for file recovery. If you have their extra copies saves somewhere in portable hard drives, clouds or even simple CDs, you can recover these files with their help. Otherwise, please, follow the data recovery tips presented by our experts.
Speaking of ransomware prevention means, you should restrain from opening spam emails which contain suspicious attachments, avoid visiting insecure file sharing domains, and update your security programs regularly.
If you encountered problems related to Troldesh virus removal, use instructions provided below.
Getting rid of Troldesh virus. Follow these steps
Manual removal using Safe Mode
To eliminate this virus with the help of Safe Mode, use these steps before launching the anti-spyware tool.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Troldesh using System Restore
To remove Troldesh ransomware with System Restore, you need to use the following rules.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Troldesh. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Troldesh from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Troldesh, you can use several methods to restore them:
Using Data Recovery Pro to recover encrypted files
Data Recovery Pro is considered one of the options for you to recover files. Nonetheless, the program cannot assure that all of tyour files will be decrypted since it was originally designed to restore lost data after a system crash.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Troldesh ransomware;
- Restore them.
Make use of Shadow Expplorer
This tool works on the basis of shadow volume copies, so there are high chances that you may restore encoded documents and files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Troldesh and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Jeff Elder. Ransomware strain Troldesh spikes again – Avast tracks new attacks. Avast. Security blog.
- ^ Jakub Kroustek . A lot of #Troldesh #ransomware samples with a '.crypted000007' extension spreading during the last week. Twitter. What's Happening?.
- ^ Tara Seals. Troldesh Nabs Top Ransomware Spot. infosecurity group magazine.
- ^ Patrick Howell O'Neill. Ransomware is now a $2 billion-per-year criminal industry. cyberscoop. Financial news .
- ^ TPVCGateway. Virustotal. A free service for analyzing suspicious URLs and files.





















