TurkStatik ransomware (Virus Removal Guide) - Decryption Methods Included
TurkStatik virus Removal Guide
What is TurkStatik ransomware?
TurkStatik ransomware is the Turkish victims targeting virus that is now decryptable
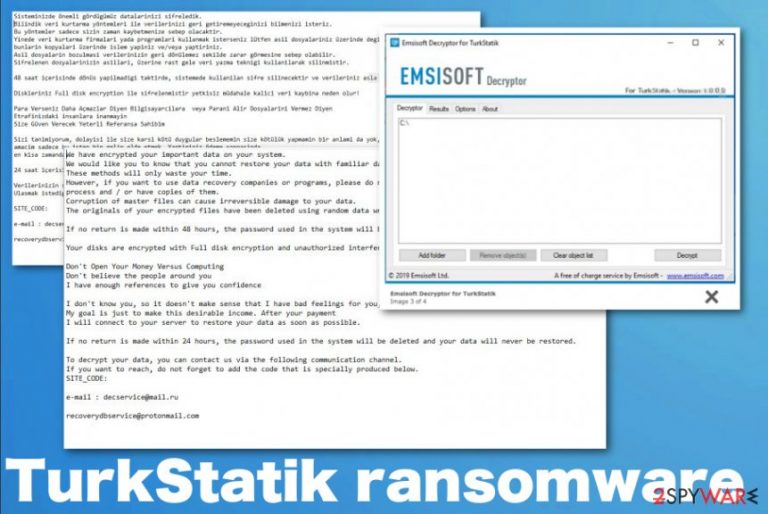
Luckily for those people in Turkey and other Turkish-speaking victims, TurkStatik ransomware virus is decryptable thanks to Emsisoft Decryptor for TurkStatik virus that is free and can help you get those files recovered. You need to remove malware from the system first because it can repeatedly encrypt files on the system, so you will need to recover files over and over again that may not be even possible. The decryptor requires access to a file pair consisting of one encrypted file and the original that is not encrypted so the keys of the affected file can be reconstructed, and the rest of those files can be decrypted this way. Other in-depth instructions can be found on the page where you can download the tool, but you should continue reading the article and proceed with the system cleaning first, to ensure the best recovery results.
| Name | TurkStatik ransomware |
|---|---|
| File marker | .cipher is the extension that appears at the end of every file after the file type extension and marks encrypted data on the machine |
| Ransom note | README_DONT_DELETE.txt is the file that shows a ransom demand message and provides further instructions, contact information |
| Targets | Turkish-speaking victims |
| Contact emails | decservice@mail.ru and recoverydbservice@protonmail.com |
| Distribution | Files with infectious script get attached to spam emails appearing as legitimate messages from known companies or services. Torrent sites, pirated software distributors also deliver pre-packed payload droppers to unexpected users. Encryption starts immediately after the payload drop and infiltration |
| Related file | JavaEmbededLibrary.exe is the executable containing a malicious script for the ransomware infection |
| Elimination | TurkStatik ransomware removal requires professional anti-malware tools, so all the associated programs and malicious files can get deleted |
| Decryption | You can recover your files using Emsisoft Decryptor for TurkStatik virus |
| System file repair | As for the proper system cleaning before your data recovery, you should repair the affected parts of the machine, including registry, directories, and other settings. The best way to do that is PC optimization tools like FortectIntego that might find, indicate and fix the issues with your computer |
As any other data-locker TurkStatik ransomware aims to blackmail victims into paying for the decryption and file recovery that is useless, in this case, since the malware is decryptable. We never recommend paying the hackers because cybercriminals are not trustworthy, and instead of decryption keys, people often get additional malware after contacting virus developers.
TurkStatik ransomware ransom note file README_DONT_DELETE.txt appears on the Desktop after file encryption and contact emails, given time for the ransom payment, additional information get delivered. The message from the malicious actors states the following (in the original language):
Sisteminizde önemli gördügümüz datalarinizi sifreledik. Bilindik veri kurtarma yöntemleri ile verilerinizi geri getiremeyeceginizi bilmenizi isteriz.
Bu yöntemler sadece sizin zaman kaybetmenize sebep olacaktir.
Yinede veri kurtarma firmalari yada programlari kullanmak isterseniz lütfen asil dosyalariniz üzerinde degil,
bunlarin kopyalari üzerinde islem yapiniz ve/veya yaptiriniz.
Asil dosyalarin bozulmasi verilerinizin geri dönülemez sekilde zarar görmesine sebep olabilir.
Sifrelenen dosyalarinizin asillari, üzerine rast gele veri yazma teknigi kullanilarak silinmistir.48 saat içerisinde dönüs yapilmadigi taktirde, sistemede kullanilan sifre silinecektir ve verileriniz asla geri döndürülemeyecektir.
Diskleriniz Full disk encryption ile sifrelenmistir yetkisiz müdahale kalici veri kaybina neden olur!
Para Verseniz Daha Açmazlar Diyen Bilgisayarcilara veya Parani Alir Dosyalarini Vermez Diyen
Etrafinizdaki insanlara inanmayin
Size Güven Verecek Yeterli Referansa SahibimSizi tanimiyorum, dolayisi ile size karsi kötü duygular beslememin size kötülük yapmamin bir anlami da yok,
amacim sadece bu isten bir gelir elde etmek. Yaptiginiz ödeme sonrasinda
en kisa zamanda verilerinizi eski haline getirmek için sunucunuza baglanacagim.24 saat içerisinde dönüs yapilmadigi taktirde, sistemede kullanilan sifre silinecektir ve verileriniz asla geri döndürülemeyecektir.
Verilerinizin sifresini çözdürmek için asagidaki iletisim kanalindan bizlere ulasabilirsiniz.
Ulasmak istediginide mutlaka asagida size özel üretilen kodu eklemeyi unutmayiniz.SITE_CODE:
recoverydbservice@protonmail.com
The note can appear scary or even legitimate enough, so you consider paying the ransom. This is not a good option, even when the threat is not decryptable because malware creators are focused on money, they don't care about your belongings. You need to remove TurkStatik ransomware as soon as possible instead and rely on file recovery using data backups or the official decryption tool.
Such file-locking malware starts with encryption and targets audio files, videos, photos, images, documents and backup files, databases. However, additional scripts can run in the background during the encrypting process, so your machine gets significantly damaged and affected by the threat. The more time you give the TurkStatik ransomware on your machine, the more persistent it gets. React as soon as you get the ransom message and clean the system. 
You need to thoroughly clean the machine and make sure that TurkStatik ransomware is deleted completely from your machine to avoid any possible damage to the machine or losing your files permanently. File recovery can be useless when the virus runs the encryption again.
Getting the anti-malware tool, removing the threat, repairing system files with a tool like FortectIntego, ensuring that the virus is terminated. These are the most important steps you need to take when dealing with TurkStatik ransomware. Only then file recovery can be achieved.
Possible TurkStatik ransomware detection[2] names that should help you determine what anti-malware tool to use for elimination process:
- Trojan.Agent.EGYV;
- TR/Ransom.qtrbx;
- TrojanRansom.Crypren;
- Win32.Trojan.Agent.0ZH7EH;
- Win32.Malware!Drop.
You need to rely on the professional anti-malware tool, but every engine uses different virus database, so these names can vary from tool to tool. However, experts[3] can also recommend checking a few times with multiple tools during TurkStatik ransomware removal, to be sure that the machine is virus-free and prepared for the data recovery. 
Malspam techniques allow hackers to spread their malware on a large scale
Email campaigns, when document attachments include files with malicious codes, enables hackers to deliver direct ransomware payload or the virus itself on the system in a matter of seconds or minutes. Commonly used types of files get injected with scripts and once the person opens and downloads the file code triggers the execution of virus:
- receipts of purchases;
- invoices;
- order details;
- documents with financial information.
The email itself looks legitimate, and people who receive similar notifications often don't think twice before opening such an email and downloading the file directly. Unfortunately, the only way to avoid infection is to delete suspicious emails, clean the email box more often, and stay away from anything raising questions online like pirated software delivering services, torrent sites.
Get rid of TurkStatik ransomware cryptovirus and decrypt your files
TurkStatik ransomware virus is a serious threat that needs to be terminated no matter if you choose to decrypt files or replace them with copies from the backup device. Malware also runs in the background, and even though the encryption might be done, your machine is still infected.
To remove TurkStatik ransomware completely, get an anti-malware tool, and run a scan to indicate malicious files and delete them fully. Then, you should try FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes and look for damaged or corrupted system files, which can affect the performance further.
After the proper TurkStatik ransomware removal, you can go through the decryption process. Run the tool and select the file pair that is needed for the data recovery. Decryptor should start the reconstruction. This may take time, so prepare to be patient if you want to get your files back.
Getting rid of TurkStatik virus. Follow these steps
Manual removal using Safe Mode
Reboot the infected machine in Safe Mode with Networking, so your AV tool can run on the system as it supposed to
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove TurkStatik using System Restore
System Restore is the feature that can be used to recover the device in a previous state when the virus is not affecting the PC
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of TurkStatik. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove TurkStatik from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by TurkStatik, you can use several methods to restore them:
Data Recovery Pro is the program capable of recovering files after TurkStatik ransomware attack
Try Data Recovery Pro when your files get accidentally deleted or encrypted by the ransomware virus
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by TurkStatik ransomware;
- Restore them.
Windows Previous Versions can help with files individualy
When you want to use Windows Previous Versions for encrypted files, you should enable System restore before hand
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer is the method for file restoring
When your files get encrypted, but TurkStatik ransomware leaves Shadow Volume Copies untouched, ShadowExplorer can get restored
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
TurkStatik ransomware can be decrypted with a tool released for free
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from TurkStatik and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Virusai. Virsuai. Spyware related news.
- ^ Differences Between Rijndael and AES. Stackoverflow. Online forum.
- ^ JavaEmbededLibrary.exe detection rate. Virustotal. Online malware scanner.







