Twitter Crypto Giveaway scam (fake) - Free Instructions
Twitter Crypto Giveaway scam Removal Guide
What is Twitter Crypto Giveaway scam?
Twitter Crypto Giveaway is a scam that might result in heavy monetary losses
Twitter Crypto Giveaway is a fraudulent message you may encounter on twitter-elon.net or similar scam websites online. In most cases, users end up on a fake page when they click a link on Twitter or other social media platforms, although less known websites could also host the link to it.
The premise of the scam is to convince users that they can make double the invested Etherium or Bitcoin and participate in a giveaway, allegedly organized by Elon Musk and Twitter. None of these entities have anything to do with the Twitter Crypto Giveaway scam, and the website exists only for scamming purposes.
By transferring the BTC or ETH to the promoted wallets 14nDGZLhBnfNBwJ9pckccDfdK9Ltopgc38 or 0x8b0725961c3986E4605610137C56A6648e93185E, you would be handing money directly to cybercriminals without the possibility of retrieving the invested sum. We also recommend not clicking any links or downloading files from the fake site, as it could result in personal data compromise or malware infection.
| Name | Twitter Crypto Giveaway scam |
| Type | Online scam, fraud, phishing |
| Related URL | twitter-elon.net |
| Operation | Claims that Elon Musk is conducting Bitcoin and Etherium giveaway, tricking users into sending the cryptocurrency to cybercriminals |
| Crypto wallets used | 14nDGZLhBnfNBwJ9pckccDfdK9Ltopgc38 (Bitcoin) 0x8b0725961c3986E4605610137C56A6648e93185E (Ethereum) |
| Dangers | Monetary losses, personal data compromise, malware infections |
| Removal | Do not interact with the website promoting the scam; scan your device with powerful security software to secure it |
| System fix | To fix malware damage and clean your browsers thoroughly, employ FortectIntego repair and maintenance utility |
The scam scheme explained
Crypto, blockchain,[1] and NFTs and everything about them has become the latest trend in the digital sphere. Users attempt to cash in as they don't want to miss out on an opportunity of obtaining money seemingly while doing nothing. When Bitcoin first arrived, people could have bought it for mere cents, and nowadays, one of the coins is worth thousands of dollars.
Fear of missing out (otherwise known as FOMO)[2] is a well-known psychological phenomenon, and scammers are ready to exploit it. This is why we have seen so many NFT scams around, where users invested thousands of dollars just to see the token fall down in value almost immediately.[3] Scammers, on the other hand, get away with these schemes due to a significant lack of moderation from the authorities and other regulatory bodies.
To make users believe they can make money easily, scammers use several social engineering tricks. In the case of the Twitter Crypto Giveaway scam, they use two prominent names that many might associate with something legitimate and influential – Twitter and Elon Musk, who has recently announced about acquiring the social media platform for billions.
Scammers claim that Musk is giving away 5,000 BTC and 50,000 ETH for grabs, and the only way to participate in the giveaway is by investing some money first. For example, those who invest 0.1 BTC would receive 0.2 BTC in return, or those who send 200 BTC, would receive 400 BTC later.
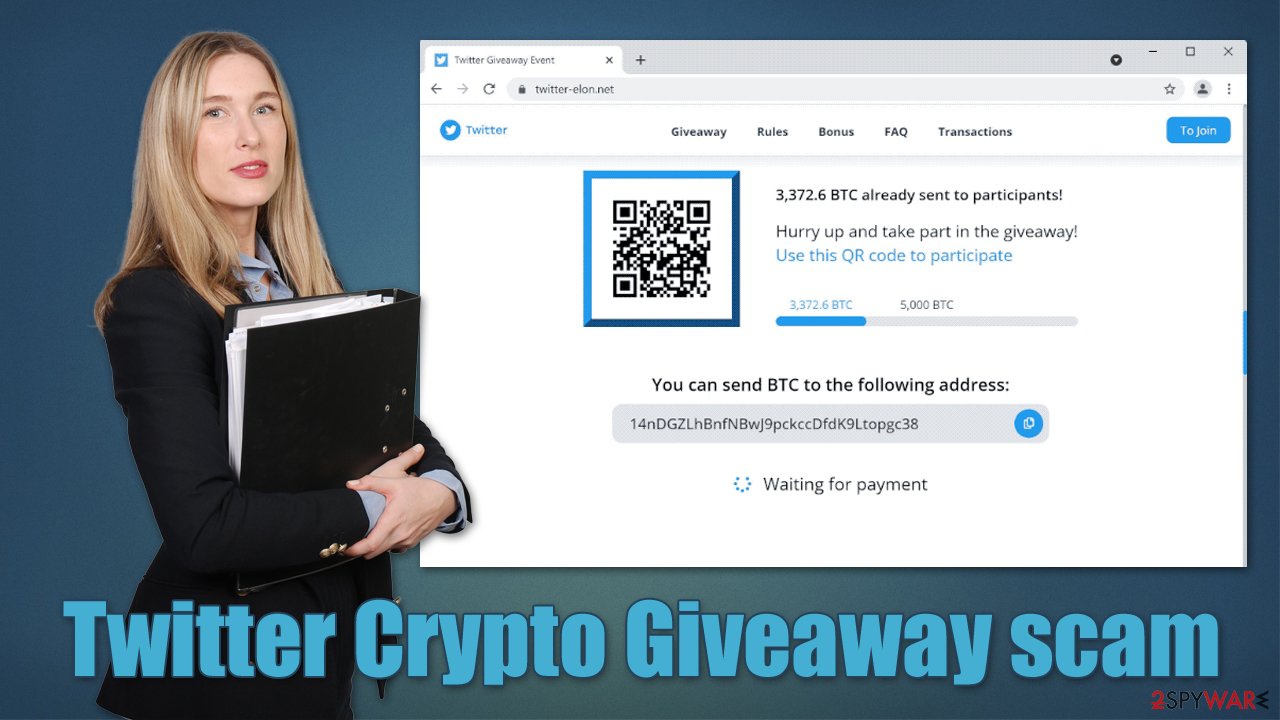
This is obviously not true, and the money would be lost upon transfer, as crypto is highly anonymous, which makes it an attractive currency for cybercriminals. In fact, ransomware developers always ask for crypto (Bitcoin, most commonly) to remain anonymous – they cash out using several rogue transactions later.
What to do next?
As evident, you should not interact with any components of the scam. By transferring money, not only do you lose your own money but also confirm to scammers that their schemes actually work. The best way to go about this is not to interact with the page at all, and simply close down the malicious site that hosts the Twitter Crypto Giveaway scam.
If you have interacted with the fake giveaway and provided your personal information, you should expect targeted phishing attacks in the future – especially if you provided your contacts such as email or phone number.
Likewise, it is not a secret that websites of dubious origin might insert malicious links or scripts that could result in malware infections. In some rare cases, if you have vulnerable software installed on the system, malware could be installed in the background without any interactions of yours. To mitigate this, make sure you protect your system with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful security program and have all the software on your computer updated to the latest version.
Note that redirects to phishing websites and malicious links could also be a sign of adware infection. This software is rather deceptive and spread in ways that often result in unintentional installation. Therefore, make sure you scan your system with security software to check it thoroughly.
Once you are sure that your system is clean from adware or other malware, you should also make sure you clean your browser caches to ensure no unwanted parties are tracking your data passively. The easiest way to do it is by employing the FortectIntego repair and maintenance tool, although the manual method is also provided below.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.
![Clear Edge browsing data Clear Edge browsing data]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ What is blockchain technology?. IBM. Security research blog.
- ^ Fear of missing out. Wikipedia. The free encyclopedia.
- ^ David A Banks. NFT scams, toxic ‘mines’ and lost life savings: the cryptocurrency dream is fading fast. The Guardian. British news site.





