UNIT09 ransomware (Improved Instructions) - Recovery Instructions Included
UNIT09 virus Removal Guide
What is UNIT09 ransomware?
UNIT09 ransomware – a file locking virus which urges $10 in Bitcoin in exchange for file decryption
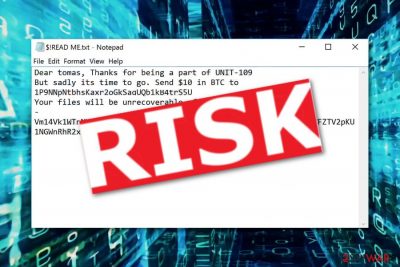
UNIT09 ransomware appears to be a file-encrypting threat which locks up important documents and demands a ransom in order to restore them. This malicious program infiltrates the system by using secret techniques, for example, spam email messages, infected hyperlinks, and files. .UNIT09 files virus starts the encryption process[1] and locks up all data by using symmetric or asymmetric encryption. Furthermore, all files end up with the .UNIT09 appendix added. Once files are locked like this, they cannot be accessed properly anymore. As a solution, the cybercriminals offer an exchange. They present all conditions in a text message named “$!READ ME.txt”. The crooks demand a $10 BTC price for file decryption and give three days to pay the urged amount. If not, files will be permanently lost.
| Name | UNIT09 |
|---|---|
| Category | Ransomware |
| Danger level | Very high. Infects the system and locks up files |
| Encryption process | This cryptovirus uses algorithms such as AES, SHA, or RSA |
| Appendix | .UNIT09 |
| Ransom note | $!READ ME.txt |
| Distribution | Spam messages, infected links, files |
| Detection | FortectIntego can detect malicious content on your PC |
| Removal | Use only reputable tools for removal purposes |
UNIT09 ransomware threatens users that their files will be lost if they do not pay in 72 hours. However, as we can see, the price for decryption is very low:
Dear tomas, Thanks for being a part of UNIT-109
But sadly its time to go. Send $10 in BTC to 1P9NNpNtbhsKaxr2oGkSaqUQb1kB4trS5U
Your files will be unrecoverable after 72 hours. Be quick 😉
–
However, we suggest not to rush and not to trust the developers. Even though the price is very low, we still advise avoiding any contact with the cybercriminals if possible. They are very likely to scam people and run away with their money. Instead of paying the demanded ransom, you should remove UNIT09 virus from your computer system automatically. We suggest using specific computer tools to detect all malicious content in the system. For this, try FortectIntego.
After you perform the UNIT09 ransomware removal, you can take a look at some data recovery techniques we have displayed below the text. Even though crooks who create and spread ransomware viruses use unique and hardly-identifiable keys that lock up files, that does not mean you should not try to decrypt them by using other tools. However, keep in mind that you need to terminate the ransomware virus first before you carry on with the file restoring methods.
Moreover, UNIT09 virus might bring other unwanted consequences also. Some of these dangerous infections are capable of permanently erasing Shadow Volume Copies of locked documents. Others have the ability to inject malware programs and make the system even more vulnerable to various infections. Because of these reasons, you should get rid of the cyber threat as soon as you spot encrypted files or the ransom note on your computer's desktop.
Once UNIT09 ransomware infiltrates the targeted computer system (this mostly happens to Windows desktops and laptops), the dangerous cyber threat injects dubious registries straight into the Windows Registry section.[2] Moreover, .UNIT09 files extension ransomware can place unwanted and hazardous files in different locations of your system. All of these components need to be terminated if wanted to get rid of the computer infection for good.

Ransomware infections can be spread by tricky messages
Ransomware usually is brought from rogue email messages that crooks send to random users.[3] You can usually find such letters in the spam section, however, in some cases, the infected letter might fall in your inbox section too, and this is the main reason why you need to be so cautious. Before opening any unexpected email message you should investigate it closely.
First, check the sender and its email address. After that, measure the risk and your expectations, were you waiting for anything important recently? No? So there is no reason of opening the message, better delete it permanently. However, if you have checked the email from all sides and it did not look suspicious to you, you can open it and search for grammar mistakes.
Crooks often leave mistakes in their message texts which lets the victims doubt the legitimacy of such letters. However, even though if the message does not contain any grammar mistakes, we still recommend avoiding opening any attached files or links as it also might be a trick. Some cybercriminals pretend to be from reputable organizations and trick users this way.
Perform the elimination of UNIT09 ransomware and get rid of all related files ASAP
According to cybersecurity experts,[4] ransomware viruses should be erased as soon as possible as these cyber threats might bring unwanted consequences to the user and his/her computer. Remove UNIT09 virus by using automatical computer tools only. Manual elimination is not a possibility in this case as the virus might be too hard to get rid of on your own and you might do just more damage to the computer system or its components.
UNIT09 ransomware removal should be performed after detecting all malware-laden content in the system. We recommend using tools such as FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes to find all malicious components in the infected system. Furthermore, do not forget to perform some system backups, activate the Safe Mode with Networking function, or disable the virus activity by using the System Restore feature.
Getting rid of UNIT09 virus. Follow these steps
Manual removal using Safe Mode
Use Safe Mode with Networking to disable the file locking cyber threat:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove UNIT09 using System Restore
Activating the System Restore feature might allow you to disable all ransomware-related activities:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of UNIT09. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove UNIT09 from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If you have found some encrypted files on your computer, do not rush to contact and pay the crooks. Take a look at these below-provided data recovery steps.
If your files are encrypted by UNIT09, you can use several methods to restore them:
Data Recovery Pro tool might appear to be really helpful:
Use this method if you want to recover some of your important files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by UNIT09 ransomware;
- Restore them.
Windows Previous Versions feature can restore some data:
Note that this method works only under one condition – you should have enabled the System Restore feature in the past.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
The Shadow Explorer tool might recover some files:
Try using this tool if the cyber threat did not erase Shadow Volume Copies of encrypted data:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Sadly, no UNIT09 ransomware decryptor has been released yet.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from UNIT09 and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Christina Mercer . What is encryption?. Tech world. About cybersecurity.
- ^ Tim Fisher. What Is the Windows Registry?. Lifewire. Independent news website.
- ^ Phil Goldstein. The 3 Main Ways Ransomware Spreads in 2017 . Biztech magazine. Articles.
- ^ Dieviren.de. Dieviren.de. Virus removal guide.





















