VHD ransomware (Free Guide) - Decryption Steps Included
VHD virus Removal Guide
What is VHD ransomware?
VHD ransomware is the cryptovirus that uses a mix of AES and RSA encryption algorithms while locking files
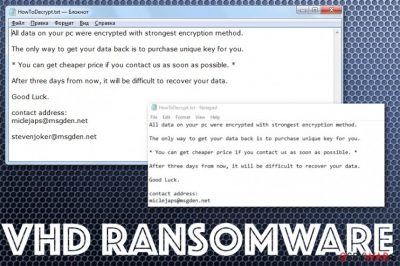
VHD ransomware virus starts the attack with infiltration and file encryption, so the text file HowToDecrypt.txt that contains ransom note can deliver the particular instructions for victims and encourage them to pay up. The paying should, allegedly, ensure that the decryption tool will get to the victim, and their files may get recovered. Unfortunately, this is not a trustworthy group of people that developed this threat and released it to people all over the globe. Experts[2] never recommend trusting them or even paying cybercriminals, even though it seems to be the only option to get your files back. Even contacting these people via their emails miclejaps@msgden.net, stevenjoker@msgden.net can lead to issues with your privacy or expose you to the dangerous material. In most cases, malicious actors collect money and keep those files encrypted.
| Name | VHD ransomware |
|---|---|
| Encryption methods | AES-256 and RSA-2048 |
| File marker | .vhd or .vhd! gets added on files affected by the encryption processes. This appendix does the indication only, data becomes useless and locked after the encoding that happens as the first step of a ransomware attack |
| Ransom note | HowToDecrypt.txt – a file that contains all the contact information from criminals and their message for victims, instructions on what to do next. This text file gets placed in various folders on the computer that contains altered data and on the desktop, so the person finds and reads it |
| Contact emails | miclejaps@msgden.net, stevenjoker@msgden.net |
| Distribution | It can be spread via spam emails and malicious files attached to those notifications, breaking through RDP[3] and relying on pirating services, software cracks, and so on. Criminals can infiltrate the system, install the trojan or worm and the virus drops ransomware payload directly on your computer |
| Danger | This type of malware involves ransom demands, blackmail, and can lead to permanent data damage or even money loss. These criminals can perform various background processes on the infected machine, so you cannot predict any scenarios when it comes to malicious actors behind the cryptovirus like this |
| Elimination | You need a proper anti-malware tool when you decide to remove VHD ransomware because full system scan can ensure that AV detection-based tool finds all associated files and programs that manage to affect the machine |
| Repair | Don't risk getting your system damaged and files encrypted forever and repair affected files, corrupted settings with a system tool like FortectIntego that can indicate parts of the OS that is damaged and needs repair as soon as possible |
VHD ransomware is not the threat that can be surely associated with any other malware family, so this is new and still need to be fully analyzed. Unfortunately, that also means that decryption is nor possible for files that get affected during the infection. Researchers may come up with a solution, but until then, you need to tackle the virus and get rid of the possible damage that ransomware caused on your computer.
You can become a victim of this threat no matter where you are because VHD ransomware targets English-speaking users and can spread around the world with all the deceptive, stealthy, and malicious techniques. Even though the attack focuses on file locking and ransom demands malware like this can easily infiltrate and affect settings or more crucial parts of the system.
VHD ransomware adds files and runs processes to stop particular programs and system functions like Microsoft Health Manager, server agents, security assistants, anti-malware programs, security functions, applications that allow data recovery to happen. Malware creators want to get as many payments as possible, so keeping your options to a minimum helps them to ensure that.
However, no experts recommend paying or even contacting those criminals behind this malicious cryptovirus. You need to remove VHD ransomware from your machine as soon as possible instead and try to repair all the functions yourself or with the help of programs like FortectIntego that can find and re[air system settings, files belonging to the operating system or needed for important programs. 
All data on your pc were encrypted with strongest encryption method.
The only way to get your data back is to purchase unique key for you.
* You can get cheaper price if you contact us as soon as possible. *
After three days from now, it will be difficult to recover your data.
Good luck.
contact address:
miclejaps@msgden.net
stevenjoker@msgden.net
If you contact these criminals, you may expose yourself to the more dangerous connection that the infection of the cryptovirus itself. VHD ransomware developers want to get profit from easily scared people, and when you write them or even pay the ransom you indefinitely put yourself at risk. Your files probably will remain damaged even if you transfer the number of Bitcoin you got asked. This is a common outcome of such incidents.
Stay calm and try to ignore those messages from malware developers. You need to perform the VHD ransomware removal as soon as you get the demanding message placed on the machine and go straight to cleaning the traces of this infection. You need to do that because anything related to data restoring cannot start until virus is fully terminated.
When you get the VHD ransomware on your machine it manages to alter Windows registry, startup preferences, and disable many programs that run on your device, install files, and apps behind your back. You cannot deal with these alterations and issues yourself because manual alterations in system files can cause even further damage than this virus itself. 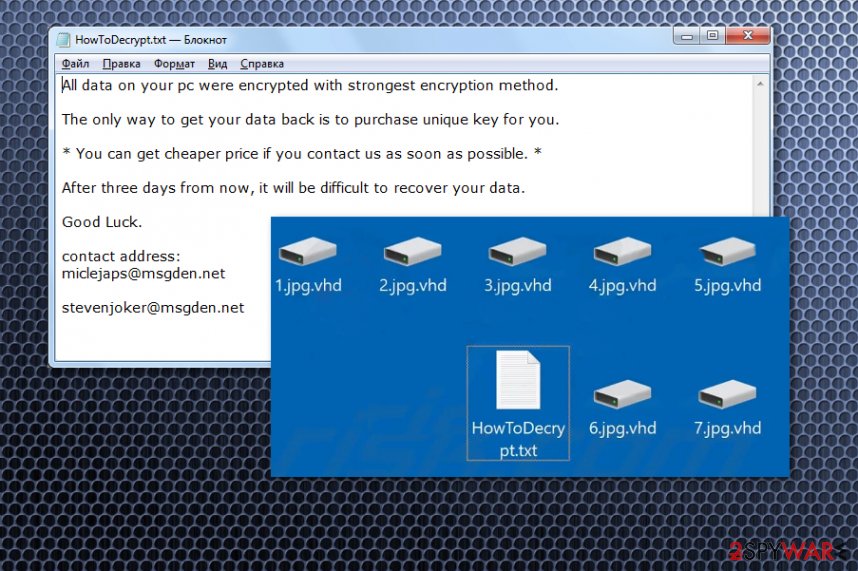
The infection gets spread with the help of malicious script injections
The payload of the ransomware can end up dropped on the machine without your knowledge because criminals rely on stealthy methods, misleading spam campaigns, malicious programs, and even hacking tools and online content. There are many options and the possibility that the wide-spread virus is distributed by at least a few of them at the time.
The first method is email campaigns during which receivers get notifications with alleged financial documents, and those MS files ask to enable the macro content that result sin macro virus release and triggers the ransomware infiltration. You should pay attention to grammar mistakes, typos, and any minor suspicions about the sender or the email itself, to avoid this type of infiltration.
Another issue with malicious files can be pirating services because of software cracks, game cheats, and other files that include scripts triggering the cryptovirus payload installation. You cannot notice these instances because executables get added alongside the wanted program or file. Staying away from these services and torrent sites entirely can help you keep the machine clear of malware. Also, scanning the system with an AV tool occasionally ensures that there are no flaws and possible infections that may lead to these serious attacks.
VHD ransomware virus removal guide
You need to take this VHD ransomware virus infection seriously because it is new and can get updated. Malware relies on encryption and uses two army-grade algorithms to achieve all the goals of cybercriminals who are money-driven hackers. Paying is not an option, you need to remember that and take care of the virus infection.
The best way to remove VHD ransomware and other more serious threats that infiltrate the machine and make all the alterations is by using anti-malware programs and applications designed to clean the system, repair files and functions. SpyHunter 5Combo Cleaner or Malwarebytes cold be the best options for your security tools.
Since threat actors included the code that disables AV engines and security tools VHD ransomware removal may get difficult. We have included a few options below that help to avoid that like Safe Mode reboot. When you terminate the malware, get FortectIntego and run it on the computer, so all the affected system files get repaired. Then, data recovery can happen without risks of getting encryption repeat itself.
Getting rid of VHD virus. Follow these steps
Manual removal using Safe Mode
Reboot the machine in Safe Mode with Networking, so you can freely run the AV tool and remove this malware from your device
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove VHD using System Restore
You can rely on System Restore feature and get rid of VHD ransomware this way
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of VHD. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove VHD from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by VHD, you can use several methods to restore them:
Data Recovery Pro is the optional program when you don't have backups of encrypted data
When VHD ransomware virus encodes your files or you delete some of them yourself, you can rely on the program like Data Recovery Pro and restore those files yourself
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by VHD ransomware;
- Restore them.
Windows Previous Versions can help with encrypted data too
When you sue System Restore as the option for virus removal, you can rely on Windows Previous Versions and manage to recover individual files
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadoExplorer is the way to restore files after VHD ransomware virus attack
When Shadow Volume Copies are still left untouched, ShadowExplorer can be a great alternative for your data backups
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption tool for VHD ransomware is not developed yet
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from VHD and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Ne VHD ransomware report. Twitter. Social media platform.
- ^ Virusai. Virusai. Spyware related news.
- ^ Lucian Constantin. Microsoft urges Windows customers to patch wormable RDP flaw. CSOonline. Tech news.





















