VirTool:Win32/DefenderTamperingRestore (Virus Removal Guide) - Dec 2020 update
VirTool:Win32/DefenderTamperingRestore Removal Guide
What is VirTool:Win32/DefenderTamperingRestore?
VirTool:Win32/DefenderTamperingRestore is a type of malware that is programmed to stop your security software from working correctly
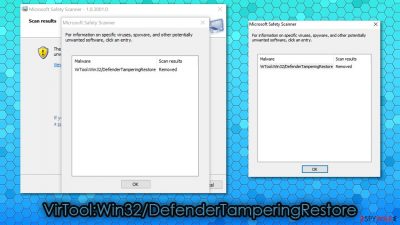
VirTool:Win32/DefenderTamperingRestore is a detection name of a potential threat that is flagged by Windows Defender security software. The main purpose of the infection is to tamper with the installed anti-malware, weaken computer defenses, and compromise the device. Once the security software has been tampered with, it might not be able to protect users from viruses, trojans, worms, ransomware, and other types of malware.
While the initial goal of this virus is to compromise security software to bypass its defenses, cybercriminals behind it may have various goals. For example, they might place a backdoor on the system in order to compromise it even further, consequently achieving the nefarious goals. Victims of such an attack might suffer from financial losses, additional malware infections, identity theft, and other privacy/security issues.
It has also been widely perceived that the detection might be a false positive[1] when the popup shows up at unexpected times. While it might be the case, it is important to investigate further and check for rootkits, uninstall extensions, reset browser settings, check system files, etc.
Finally, users who were infected with this malware also reported that their screens had been locked by a scam message which asks users to contact fake Microsoft support. Several fake warnings popup at the same time and claims that the computer has been locked and that “Trojan_Spyware Alert – Error Code #0x268d3 (!x3)” has been detected on the system. Do not trust these alerts – if you call the provided contact number, you might be scammed into paying money to cybercriminals and infect your PC with more malware.
| Name | VirTool:Win32/DefenderTamperingRestore |
| Type | Malware |
| Purpose | To disable Tamper Protection feature of Windows Defender and bypass its security |
| Distribution | Malware developers typically employ various distribution methods, although the most prevalent one remains spam email links and attachments |
| Symptoms | A popup message shows up on the screen; otherwise, malware is programmed to operate without traces (some users may experience crashes, errors, and similar unexpected computer events) |
| Risks | Malware can affect the infected users in various ways – it can steal passwords, banking details, take screenshots, install other malware, encrypt files, and much more |
| Associated scam | Trojan_Spyware Alert – Error Code #0x268d3 (!x3) |
| Removal | Windows Defender should be able to detect and eliminate the infection; in some cases, this process might fail due to malware's functionality. In such a case, we suggest you download a reputable third-party security tool (we recommend SpyHunter 5Combo Cleaner or Malwarebytes) and perform a full system scan. If malware is tampering with other security solutions, you should access Safe Mode and perform a full system scan from there |
| System fix | A malware infection can seriously damage Windows operating system files and settings, and security software might fail to fix these compromised items. If that happens, you should employ FortectIntego repair software to fix virus damage on your computer |
VirTool:Win32/DefenderTamperingRestore is a rather generic detection that can be encountered at any time. In most genuine cases, however, this occurrence happens when users come in contact with potentially malicious content online. In other words, cybercriminals attempt to spread the infection to as many people as possible, so they often choose multiple attack vectors for higher success chances. Here are a few of them:
- malicious spam email attachments and embedded hyperlinks;
- software vulnerabilities and exploit kits;[2]
- false claims on phishing websites and fake Flash Player updates;
- software cracks and pirated program installers, etc.
Thus, there are several ways how you could come in contact with the VirTool:Win32/DefenderTamperingRestore virus in the first place. Once the contact is made, Windows Defender might or might not detect the intrusion, as the malicious program is designed to disable certain security software defenses (mainly, Tamper Protection feature).
In case the security app does not get compromised completely, it will stop and remove the virus successfully. However, there is also a chance that weakened defenses would prevent a successful elimination. Unfortunately, if case malware manages to break in, it can continue to operate in the background, all while anti-malware is rendered useless.
Users affected by malware can suffer all kinds of damages, as the initial infection can be used only as a pathway for other malware to be infected. For example, ransomware such as Booa, Geno, or Kobos can be deployed in order to lock all personal files on the device and then demand ransom in Bitcoin for their return. Other invisible infections, such as trojans, may be used to steal all your passwords, bank account details, and other sensitive information, which can be later used for malicious purposes.
It is also important to note that the detection might stem from various settings set by users themselves or programs installed on the PC. For example, in the Windows Registry, the “HKLM\SOFTWARE\Policies\Microsoft\Windows Defender: Restriction” key should never be enabled, as it prevents normal operation of Windows Defender. This setting might also be changed by malware, which, in this case, should be eliminated immediately.
Without a doubt, VirTool:Win32/DefenderTamperingRestore removal should be your top priority. This is why it is important to use additional protection when trying to defend yourself from all types of malware. We suggest you scan the machine with alternative security software, such as SpyHunter 5Combo Cleaner and Malwarebytes, to ensure that the infection is completely eliminated. Experts also advise running a PC repair tool FortectIntego after the malware removal process.
VirTool:Win32/DefenderTamperingRestore infection might start showing “Trojan_Spyware Alert – Error Code #0x268d3 (!x3)” scams
There are plenty of tech support scams all over the internet – malicious actors come up with various bogus claims about users' computer security status and then provide the contact number to call to allegedly resolve the malware infection issues. As it turns out, a VirTool:Win32/DefenderTamperingRestore virus might start showing these types of fake alerts at any time when browsing the web.
While in most cases, suspicious popups are contained within the browser and can be shut down with the tab closure; this time, it is not the case. Users reported that they receive several alerts that try to imitate Windows Defender window, as well as use Windows Firewall name to intimidate users. Here's what one of the alerts claims:
Windows_Firewall_Protection
Trojan_Spyware Alert – Error Code #0x268d3 (!x3)
Access to this PC has been blocked for security reasons.
Contact Windows Support: +1-888-210-6024
We can assure you that this Trojan_Spyware Alert – Error Code #0x268d3 (!x3) popup has nothing to do with Windows or Microsoft, and all the attributes, such as logos and the identical UI features, are all faked. “Your computer has been blocked” alert is also present in the background, which is commonly used on various websites in a similar manner.
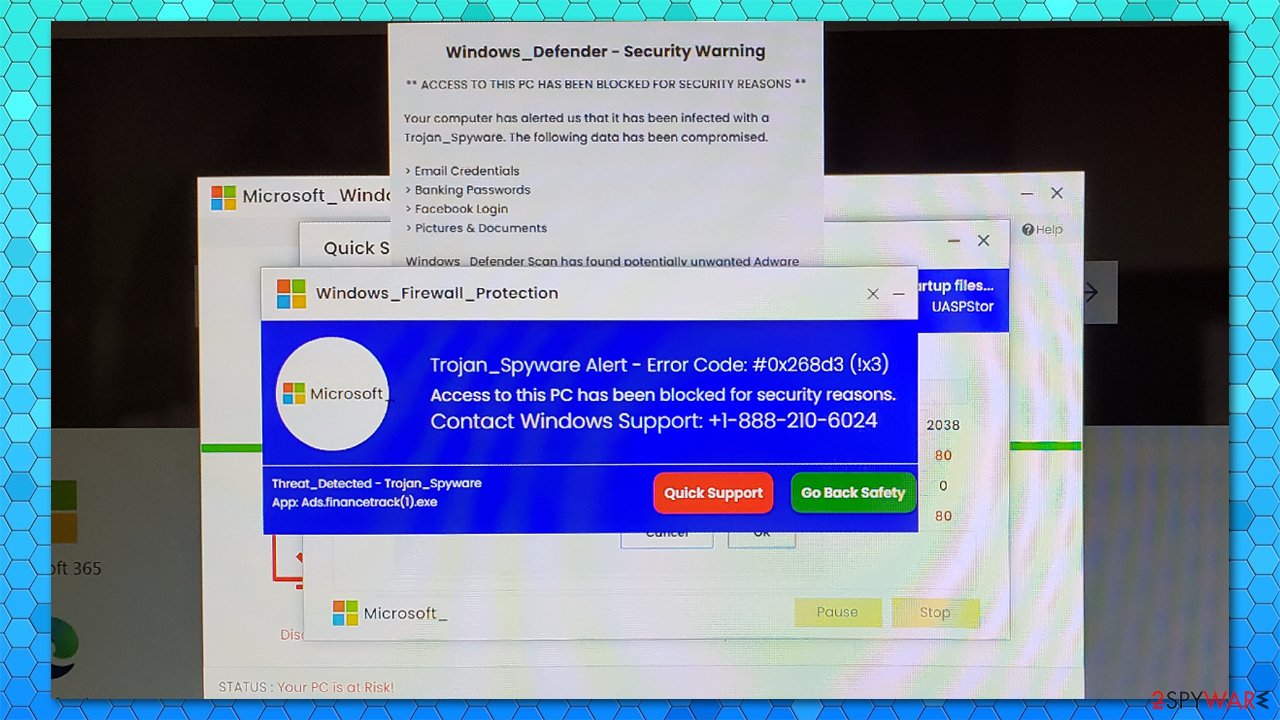
Due to several messages that bombard the screen, many users might be intimidated and believe that these alerts are real. You should never call these provided numbers, as you might be scammed or additional malware installed on your system once you contact the crooks and provide them remote access to your machine.
Many users were baffled as they could not use their computers properly due to the screen-locking function. One of the best ways to bypass this is to open the Task Manager and shut down all the unneeded programs currently running – including the web browser. If no luck, you should reboot your PC and access Safe Mode, and then perform a full system scan from there.
Security software conflict issues: VirTool:Win32/DefenderTamperingRestore pop-up might show up as soon as you install a third-party security tool
Some users reported that they keep getting the VirTool:Win32/DefenderTamperingRestore detection on several occasions, i.e., the infection does not go away after removing it with Microsoft Safety Scanner; according to reports, alternative security solutions, such as Norton or Trend Micro, fail to find this threat completely.[3]
In such cases, the issues seem to lie within how different security solutions interact with each other. Windows Defender uses the Tamper Protection feature that can be enabled and disabled via the anti-virus interface or Registry Editor (HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Features). Some malware might attempt to tamper with this setting. However, each time a third-party security solution is installed, the Tamper Protection feature is also disabled in order to prevent false positives and allow the normal operation of the software.
Microsoft launched the Tamper Protection feature with the release of Windows 10 version 1903 in early 2019.[4] According to Microsoft, it provides additional protection from outside intervention. Unfortunately, this can also cause major conflicts when third-party security software is used, as the function is disabled each time a new anti-malware is installed.
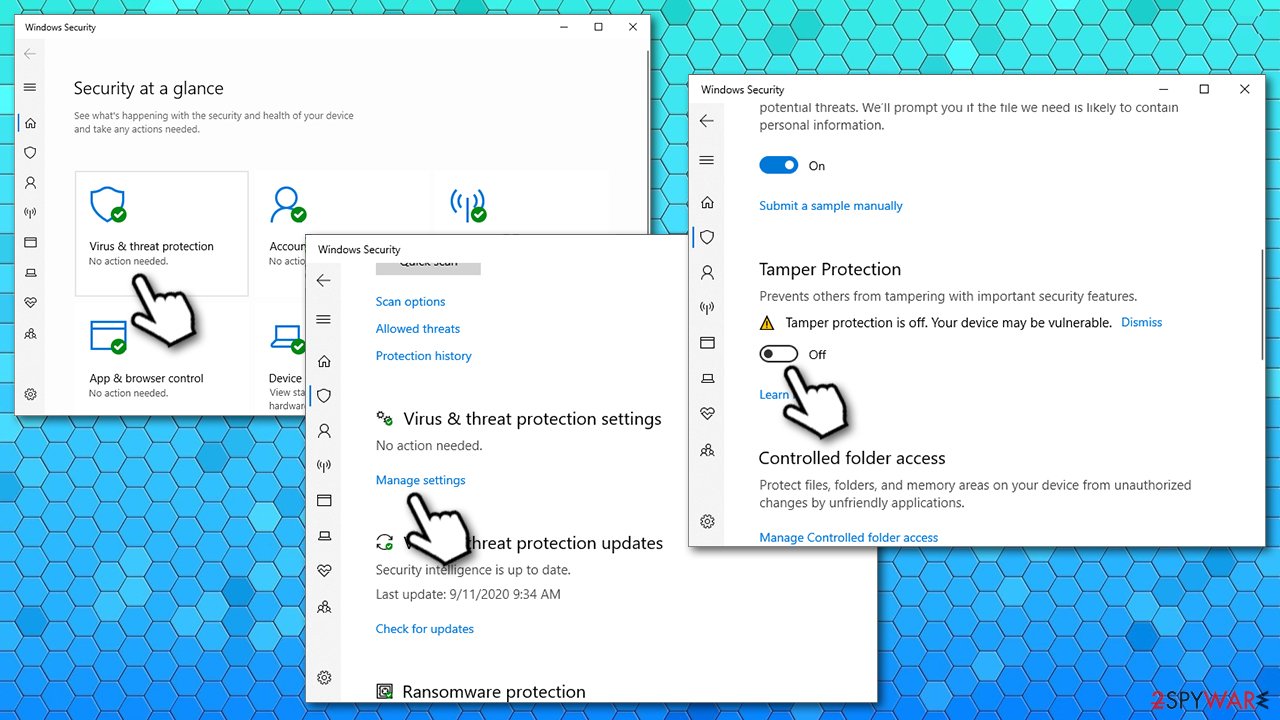
Therefore, to stop VirTool:Win32/DefenderTamperingRestore popups, if you are using a third-party security tool and disable Tamper Protection, you should follow these steps:
- Type in Windows Security in Windows search and hit Enter
- Pick Virus & threat protection
- Under Virus & threat protection settings, click Manage settings
- Scroll down, locate Tamper Protection
- Turn the switch to the left to turn Tamper Protection off.
VirTool:Win32/DefenderTamperingRestore removal instructions
As mentioned above, if your security software managed to catch the infection despite being tampered with, the VirTool:Win32/DefenderTamperingRestore removal process should occur automatically. In case your security application fails due to malware's main function, we advise you to download and install alternative anti-malware solutions, such as SpyHunter 5Combo Cleaner or Malwarebytes, and then perform a full system scan. If the need arises, you can also access Safe Mode with networking, as explained below, and perform a scan from there.
However, if you are unable to remove this virus automatically and you are using a third-party anti-malware tool along with Microsoft Defender, you should disable the Tamper Protection feature to prevent software conflict from happening in the future.
It was also reported that some malware could cause significant side effects after it is eliminated. For example, the setting “Managed by your organization” might prevent normal functions of anti-virus. To fix this issue, you might have to edit Group Policy, enable Telemetry Service, and change settings within the Windows registry. If you are not IT-savvy, we highly recommend employing FortectIntego to fix various issues with Windows systems after the infection is deleted.
Getting rid of VirTool:Win32/DefenderTamperingRestore. Follow these steps
Manual removal using Safe Mode
If VirTool:Win32/DefenderTamperingRestore prevents your security software from working normally, perform a scan with alternative software in Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from VirTool:Win32/DefenderTamperingRestore and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Chris Hoffman. How To Tell If a Virus Is Actually a False Positive. How To-Geek. Site that explains technology.
- ^ What is an Exploit Kit?. Palo Alto. Security research blog.
- ^ VirTool:Win32/DefenderTamperingRestore. Norton. Official community forums.
- ^ Martin Brinkmann. Windows 10 1903: Windows Defender Antivirus gets Tamper Protection feature. Ghacks. Technology News.
• Nederlands
• Deutsch
• Français
• Italiana
• Português
• Español
• Svenska
• English (UK)














