WannaCry hacker group email scam (Free Instructions) - Easy Removal Guide
WannaCry hacker group email scam Removal Guide
What is WannaCry hacker group email scam?
WannaCry hacker group email is a scam that threat actors use in order to blackmail users to pay Bitcoins
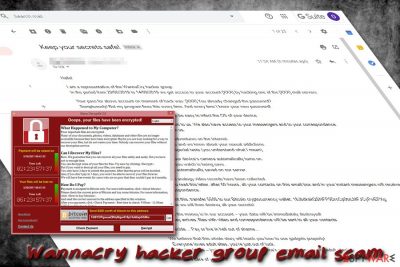
WannaCry hacker group email is a new variant of a massive malspam campaign that tries to make users giveaway their money after they allegedly were recorded watching porn via the hijacked video camera. While trying to scare users even more, they rely on an infamous Wannacry name which is known to be still active. The phishing email belongs to the group of sextortion scams[1] which have been used by various hacking groups, although the exact number of involved parties is not yet known.
Malicious actors behind WannaCry hacker group scam claim that as soon as victims enter porn sites, the computer camera turns on and starts recording a video automatically. Besides, crooks slip in the sentence about having access to users' contacts and then claim that they will disclose the compromising video to everybody. In order to allegedly stop this from happening, victims are asked to pay $550 into the provided Bitcoin wallet within 60 hours, or otherwise, the footage will be published. While visiting adult-related websites is dangerous, no one can launch your PC's camera to watch you.
| Name | WannaCry hacker group email scam |
| Category | Extortion scam which is also commonly referred to as Sextortion scam |
| Type | Social engineering attack, fraud, scam |
| The fake claim | Cybercriminals behind the attack claim that they are the developers of the notorious WannaCry ransomware virus and also include the email password they received from the underground hacking forums to make the message more believable. They claim that the hijacked camera recorded the user while he or she was visiting adult sites and threaten to release the compromising footage to the victim's relatives and friends |
| Ransom demand | Victims are asked to pay $550 ransom in Bitcoin |
| Cryptowallet address | 18JbdkskQSNFP9DrcCp9txLMFJCyPwEPXg, 12byutpYf1xpH8fR4qBj4833x2t94rSr8X |
| Further actions to be taken |
WannaCry hacker group email scam campaign is distributed with the help of botnets[2] – networks of computers that have been infected with malware. Therefore, the number of emails sent out may be counted in hundreds of thousands. Nevertheless, the scam message also includes a legitimate password that is or was used for the current user email account. This information is that baffles most and makes WannaCry hacker group email scam so much more believable.
Users can receive WannaCry hacker group phishing email at any time, and it often arrives into Junk mail section. For that reason, luckily, many might skip it and never have to deal with the hoax. However, those who do read the message might be caught off guard and straight out panic.
Due to the mentioned password, users might get scared even more and, due to the sensitive nature of the topic, give in to hackers' demands. However, WannaCry hacker group email is fake, and the provided email was most likely retrieved from previous data breaches[3] that happen relatively often nowadays.
WannaCry hacker group email scam claims the following:
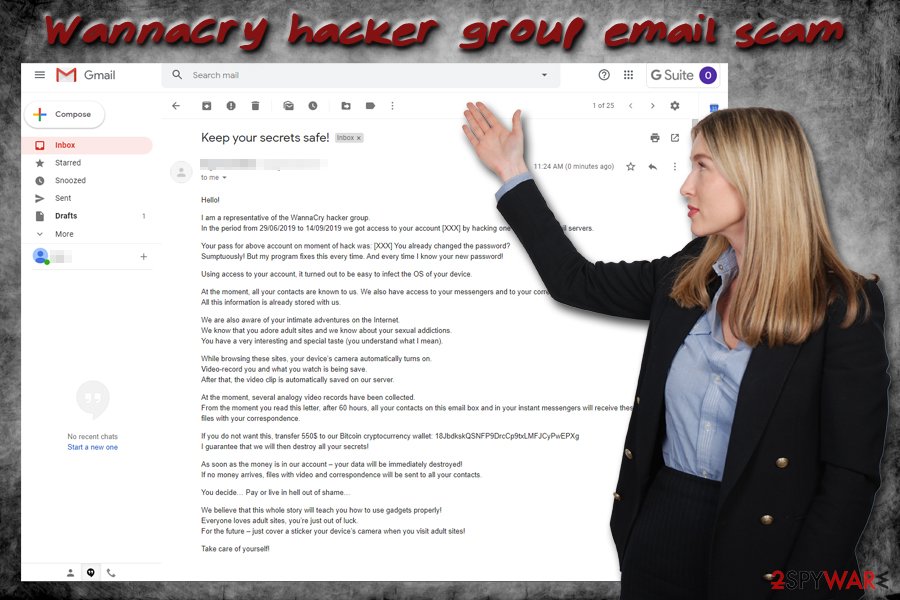
Hello!
I am a representative of the WannaCry hacker group.
In the period from 29/06/2019 to 14/09/2019 we got access to your account [XXX] by hacking one of the [XXX] mail servers.Your pass for above account on moment of hack was: [XXX] You already changed the password?
Sumptuously! But my program fixes this every time. And every time I know your new password!Using access to your account, it turned out to be easy to infect the OS of your device.
At the moment, all your contacts are known to us. We also have access to your messengers and to your correspondence.
All this information is already stored with us.We are also aware of your intimate adventures on the Internet.
We know that you adore adult sites and we know about your sexual addictions.
You have a very interesting and special taste (you understand what I mean).While browsing these sites, your device’s camera automatically turns on.
Video-record you and what you watch is being save.
After that, the video clip is automatically saved on our server.At the moment, several analogy video records have been collected.
From the moment you read this letter, after 60 hours, all your contacts on this email box and in your instant messengers will receive these clips and files with your correspondence.If you do not want this, transfer 550$ to our Bitcoin cryptocurrency wallet: 18JbdkskQSNFP9DrcCp9txLMFJCyPwEPXg
I guarantee that we will then destroy all your secrets!As soon as the money is in our account – your data will be immediately destroyed!
If no money arrives, files with video and correspondence will be sent to all your contacts.You decide… Pay or live in hell out of shame…
We believe that this whole story will teach you how to use gadgets properly!
Everyone loves adult sites, you’re just out of luck.
For the future – just cover a sticker your device’s camera when you visit adult sites!Take care of yourself!
Initially, because the WannaCry name was used in the message, one might think that crooks would try to intimidate victims about infecting their machines with the devastating ransomware. However, it seems like the scam goes straight into the “you have been recorded while watching porn” scenario. Most likely, criminals are counting on the immense publicity the virus got during its outrage in 2017[4] – it should intimidate victims and listen to their demands.
If you received such an email, you should ignore it but do not hurry to remove WannaCry hacker group email scam from your Inbox. Before you do anything, however, you should first scan your machine for malware just a precautionary measure – we recommend using FortectIntego or SpyHunter 5Combo Cleaner for the purpose.
If no malware was detected, you should also check your bank transaction list, change all your passwords, report the issue to the appropriate authorities and only then proceed with WannaCry hacker group email scam removal from your Inbox.
Spam emails might not only intimidate but also be the cause of a severe malware infection
Spam emails are among one of the older malware distribution tactics. While it is relatively primitive, it remains one of the most used methods for spam, scam, and malware delivery to millions of users daily. Therefore, it is important to stay vigilant, especially when email used regularly.
Be aware that cybercriminals come up with various tricks in order to make users click on malicious attachments or hyperlinks, and even make them transfer money by using social engineering. Note that most of the malicious emails will be sent to the Junk mail, and, while sometimes it happens by mistake, you should not casually open these messages without closely examining them.
When dealing with spam emails, keep in mind the following:
- Never allow the attachments to execute macro commands, as this will most likely end up in malware infection;
- Watch out for various grammar and spelling mistakes, as well as formatting inconsistencies;
- Always check Sender's address, as crooks often impersonate well-known companies and high-profile retailers like Amazon, UPS, etc. Usually, the Sender's address differs by one letter and looks almost identical from the first sight;
- Watch out for email spoofing – this technique allows crooks to make it seem like the email was sent from somebody else;
- Always ask questions like “should I be receiving this email?” “why am I receiving this email?” etc.
- If in doubt, never open any attachments or click on links!
Finally, when it comes to extortion scams, you need to do your research and never believe everything that is written in an email that comes from an unknown source.
Proceed with the following actions after receiving WannaCry hacker group email
Let's make it clear: if you received WannaCry hacker group email scam, it is highly unlikely that your machine is infected with malware that can take over your camera. Nevertheless, some malware actually has the capability of performing actions that crooks describe. Therefore, you should immediately scan your machine with anti-malware software to remove WannaCry hacker group email scam virus.
If no malware was detected by the security software, we suggest you report the email to the local authorities that deal with fraud:
- https://www.usa.gov/stop-scams-frauds – USA
- https://www.actionfraud.police.uk/ – UK
- https://www.scamwatch.gov.au/report-a-scam – Australia
- https://www.europol.europa.eu/report-a-crime/report-cybercrime-online – other European countries
Once you have done that, you should also check your online payment transaction history to make sure no illegal money transfers were performed. After that, you can finally proceed with WannaCry hacker group email scam removal from your email box.
Getting rid of WannaCry hacker group email scam. Follow these steps
Manual removal using Safe Mode
If you think you might be infected with any type of malware, you should scan your machine with anti-virus software in Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove WannaCry hacker group email scam using System Restore
You can also attempt to delete malicious software by using System Restore:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of WannaCry hacker group email scam. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from WannaCry hacker group email scam and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting spam tools
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Anatomy of a sextortion scam. Cisco Talos. Security Intelligence blog.
- ^ Botnet. Techopedia. Where IT and Business Meet.
- ^ Gaby Del Valle. The Marriott hack exposed the passport numbers of more than 5 million people. Vox. Understand the News.
- ^ Lee Mathews. How WannaCry Went From A Windows Bug To An International Incident. Forbes. American business magazine.





















